Inadvertent Waiver
Blog
Thought Leadership
Inadvertent Waiver
Fred Touchette

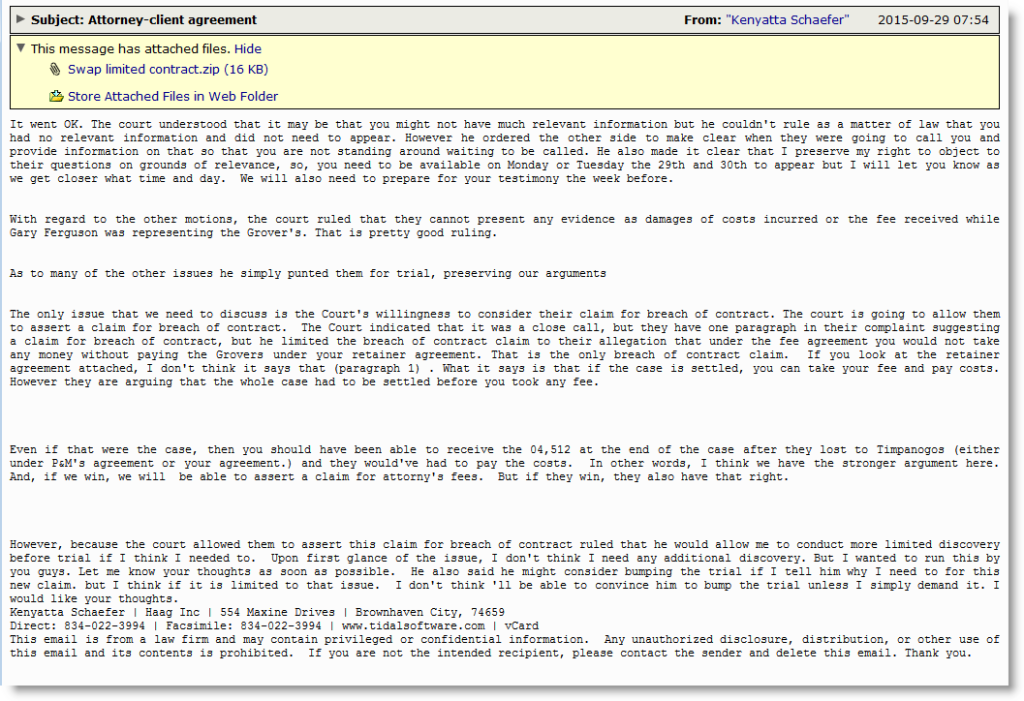
This morning we've been seeing yet another offering from the Upatre guys. This time it comes in with a rather lengthy, by comparison, email with the subject line "Attorney-client agreement". This story line certainly leaves out a few major details as it begins with a lawyer apparently already in court fighting against some sort of breach of contract suit against the recipient. The opening paragraph even forgives the intended targets for missing court this morning, citing that the court "understood". This must come as a real shock to those of us who don't keep a lawyer on retainer and those who didn't realize they were being sued. It probably would've been really nice of this mystery lawyer to let you know that this was going on before it got to this point, I would think.
Regardless, the email goes on to give a vague report on what happened in court this day and a few things that the new defendant can expect as this fake lawsuit unfolds. This is a very classic, although slightly long-winded, social engineering technique employed by cyber thieves to both raise a little fear and a lot of curiosity in their victims which will then hopefully entice them into falling for their ruse. The payload in this attack lives in an accompanying attachment. Each of these attachments are quasi randomly named by stringing together three different words from an apparent wordlist supplied by the command and control server. This randomization makes it slightly harder to nail down these files, simply because one cannot block based on the filename alone. Otherwise, it's business as usual when it comes to stopping these nuisances.
One interesting detail about this line of attacks is that they seem to be targeting older, out of date PCs. After running the samples on a couple different operating systems, they only seemed to want to carry out their malicious intent on machines running Windows XP (I was using SP3). On newer versions it would shut itself down almost immediately after execution. Once operational though, this malware begins to hijack system processes to get a foothold on its new victim. It then reaches out to check its IP address and then looks to communicate with the IP 197.149.90.166 on port 12299 where it reports back with information about the new target such as the IP it had just looked up and the computer name. Following this, the malware adds a good number of registry entries dealing with security certificates, mostly disallowing them and peeks around for debugging tools.
Even on Windows XP these samples seemed a little rickety as they tended to crash after a fairly short period of time, but they did have the best success rate on the XP machines. I wouldn't be surprised though if this little issue is quickly resolved and we start seeing the next campaign from these guys within the day. Seeing several different themes from this particular family of malware has been commonplace and happening on a daily basis for quite sometime now.
AppRiver's SecureTide has everyone covered though as we're blocking these preemptively to help keep your machines happy and healthy.