Malicious Macros and OLE Malware
Blog
Thought Leadership
Malicious Macros and OLE Malware
Jonathan French
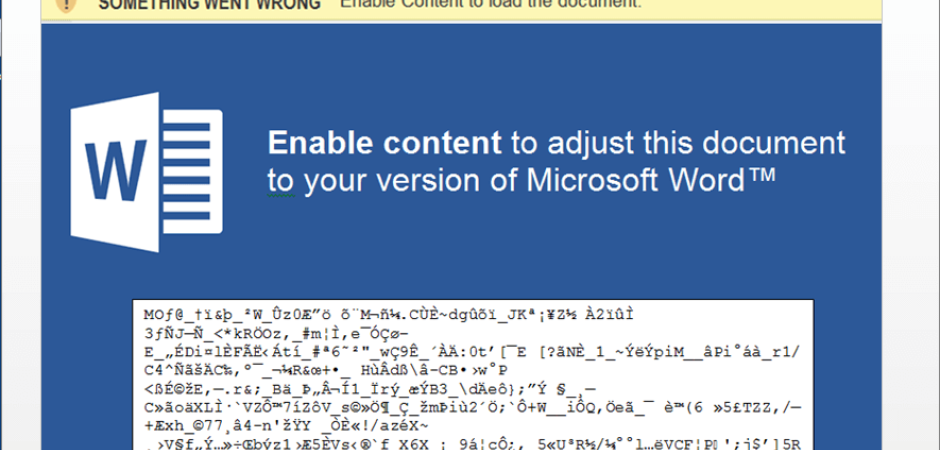
Malicious macros are nothing new these days. They've been around for years and will likely be staying for years to come. Macros themselves aren't the enemy though, and in fact can be a very powerful tool to help users automate complex tasks within a document. However, malware authors use the macro power for evil by creating bits of code that can download and execute malicious files when the documents are run on a victims machine. Macros are disabled by default in Office products these days, but unfortunately users still get a pop up asking them if they want to run the macro. Since most users don't know what this means and the document often says they need to run the macro to see the actual content, people end up clicking enable and it goes downhill from there.
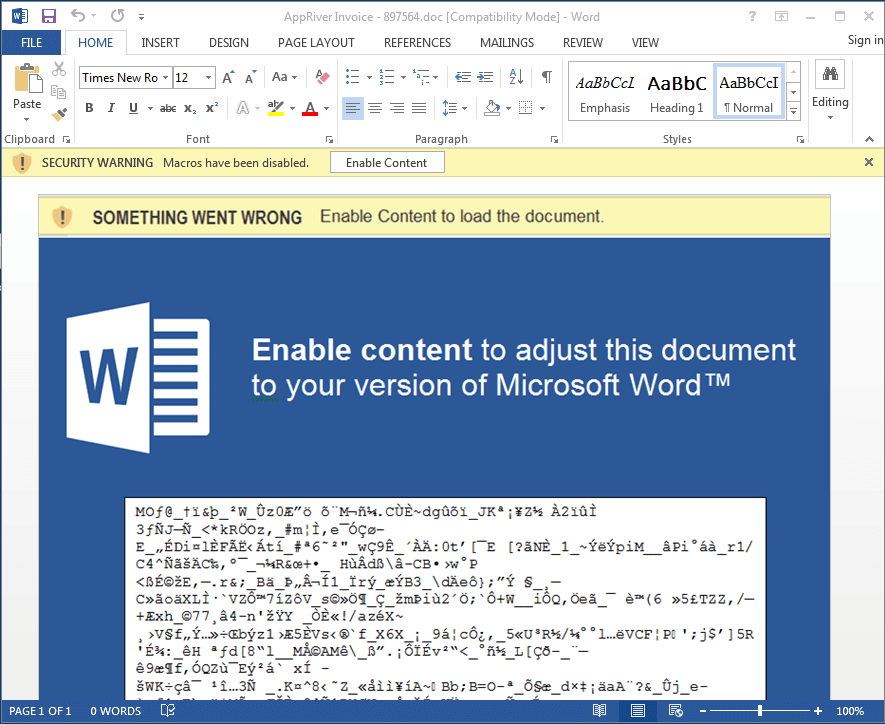 Clicking "Enable Content" will run the malicious macro and download malware to the machine.
Clicking "Enable Content" will run the malicious macro and download malware to the machine.
But macros aren't the only threat when it comes to malicious document attacks. Office documents also support Object Linking and Embedding (OLE for short). Microsoft recently published a blog about OLE malware as well. While OLE's aren't new either, they are being used for malicious purposes as well. Many times they are formatted similar to the Macro documents saying you need to click something to see the content, but you don't get the macro warning banner when opening the file. As with macros, this is supported both in Excel and Word as well.
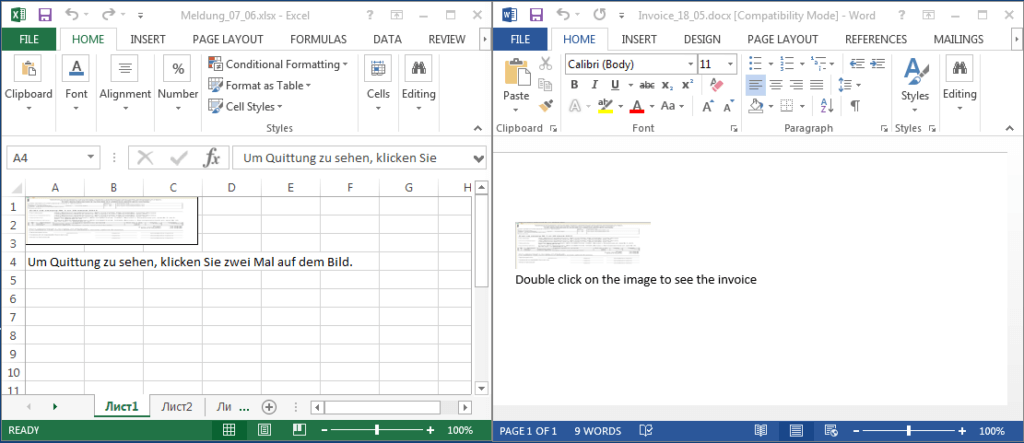 OLE support is in both Excel and Word.
OLE support is in both Excel and Word.
The benefit for an attacker using OLE's is that the payload is contained as an OLE object inside the document itself. While with most macro malware, the macro reaches out to a server on the internet, downloads the payload, and then executes it. So OLE malware is an all in one package for delivery. They can set the object to execute or run whatever file they please as well (exe, vbs, js, etc).
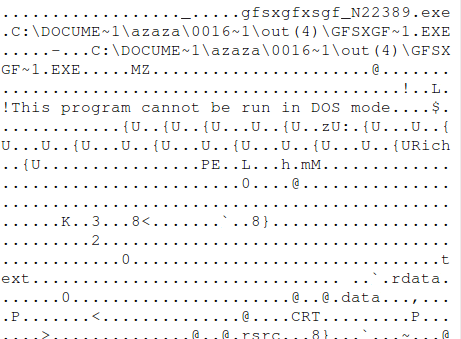 Extracting the contents of the document shows the executable inside the OLE object.
Extracting the contents of the document shows the executable inside the OLE object.
Many AV engines as well as our filters are capable of detecting these types of threats and blocking them. But as with all other types of malware, the authors are constantly trying to find ways to bypass any sort of filtering or detection solutions. Macro and OLE malware, especially in the world of business, is dangerous since handling documents is a normal day-to-day task for most people. A user being given the power to run a malicious macro or open a bad OLE is a default permission on the Windows machine. After all, these Office features do have their good uses. Fortunately if you wish to just block these outright on the machines and not even give users a choice of running them, it can be done with registry edits and group policies. These days it may be worth IT departments to look in to enforcing these blocks. With document malware like this being likely to stay around, disabling these mostly unused features just adds another layer of security.
