Ransomware Spreading via Malicious Java Script Files
Blog
Thought Leadership
Ransomware Spreading via Malicious Java Script Files
Troy Gill
Cybercriminals are nothing if not persistent. Part of that persistence comes in the form of reoccurring themes.
One of the most popular social engineering themes utilized in malware distribution over the past decade have come in the form of phony emails posing as a parcel delivery notifications. Think UPS, FEDEX, DHL or USPS etc...
The attackers tend to stick to what works. After all, why stray from the formula so long as some people are willing to click?
BE WARY OF ATTACHMENTS
Today there we began seeing a large influx of messages claiming to be from none other than UPS.
The messages have varying text in the body but all aim to convince you that you missed a parcel delivery and that the details are in the message attachment. The attached zip archive contains a java script file (MD5 2e351e0ff1c4bd95749a918cff85353e) named to appear as a doc file.
RELATED LINK: Keep your business safe from ransomware, malware
The file is a downloader, that once clicked, goes to work pulling down and dropping more exploit code and malicious payloads onto the victim’s machine. This leads to an install that appears to be a version of the Locky Ransomware. Locky Ransomware has been in circulation for quite a while now and is often distributed via the Necurs botnet.RELATED LINK: Hancitor, a malicious downloader picks up steam
WHAT TO LOOK OUT FORHere’s a look at the message/attachment: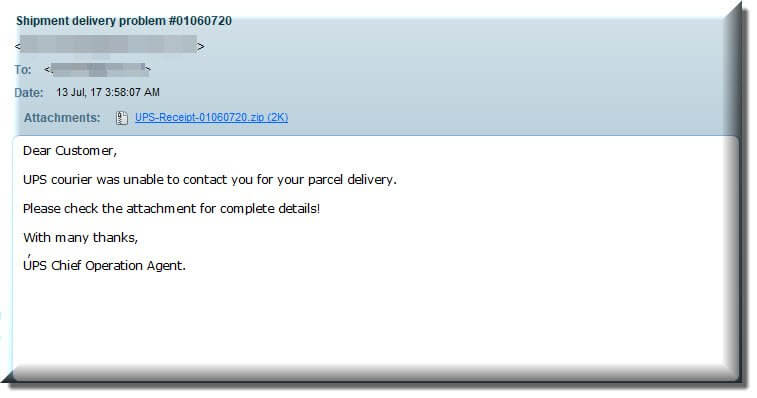
![]()
We observed the malware reaching out with the following network communication to complete the attack chain:
Please stay clear of this threat and make sure that these sites/IP are all blocked on your network. As usual, our SecureTide and SecureSurf customers are all protected from this threat.

