Global Security Report
The Global Security Report for 2020 highlights the threats and trends Zix | AppRiver Security analysts saw throughout the year.
In this report, we will take a deep dive into many of the threats and trends we saw in email security as well as discuss examples of prevalent attacks and explore potential impacts.
Prevent advanced threats from compromising your email by
identifying those vulnerabilities before they happen.
Introduction
Threat actors have always leveraged both local and world events to help spread their attacks. Never more so than in 2020. Early in the year, as the global pandemic came to fruition, attackers began launching spam, phishing and malware attacks utilizing interest in the pandemic. It wasn’t long before they had begun crafting attacks centered around the surge in remote work. Later in the year they took advantage of the contentious US Election cycle to distribute attacks.
In 2020, Attackers continued to embrace the use of more targeted attacks versus the large volume email blasts we have seen in the past. Attackers continued to evolve and improve their distribution methods especially with “living off the land” style phishing attacks. They did this by ramping up their abuse of many legitimate service providers as well as adding new services to their toolbox on a regular basis throughout the year.
Pandemic Prominent During First Half of the Year
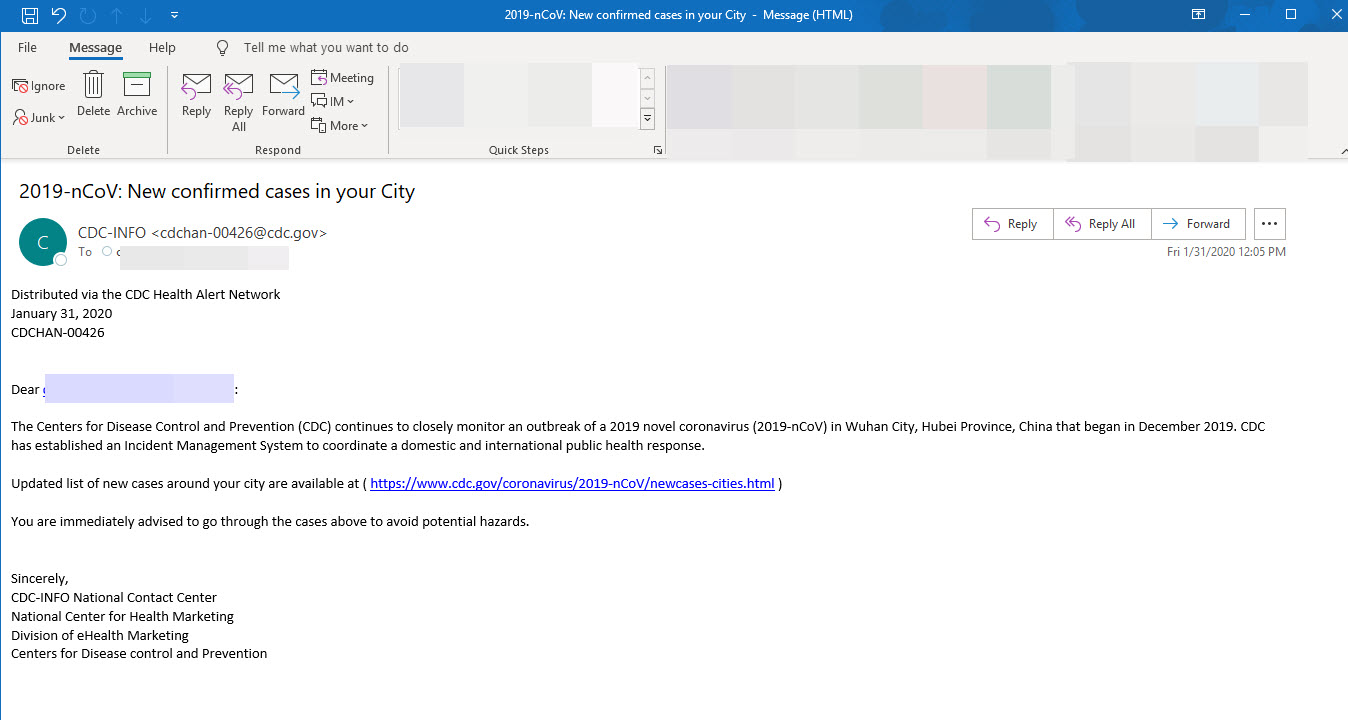
Keeping true to form, attackers were quick to take advantage of the global pandemic. The first attacks we observed in early 2020 were phony PPE distribution email scams. While these emails contained no malicious code, they were and continue to this day to be quite damaging to entities that need this equipment. With so many on a tightened budget they can hardly afford to lose funds to scammers at such a critical time.
Not long after though, we began seeing phishing attacks exploiting the pandemic to spread their attacks. Attackers were seen posing as organizations such as the CDC, WHO and SBA pushing out hundreds of thousands of phishing and malware attacks per day.
Malware Attacks
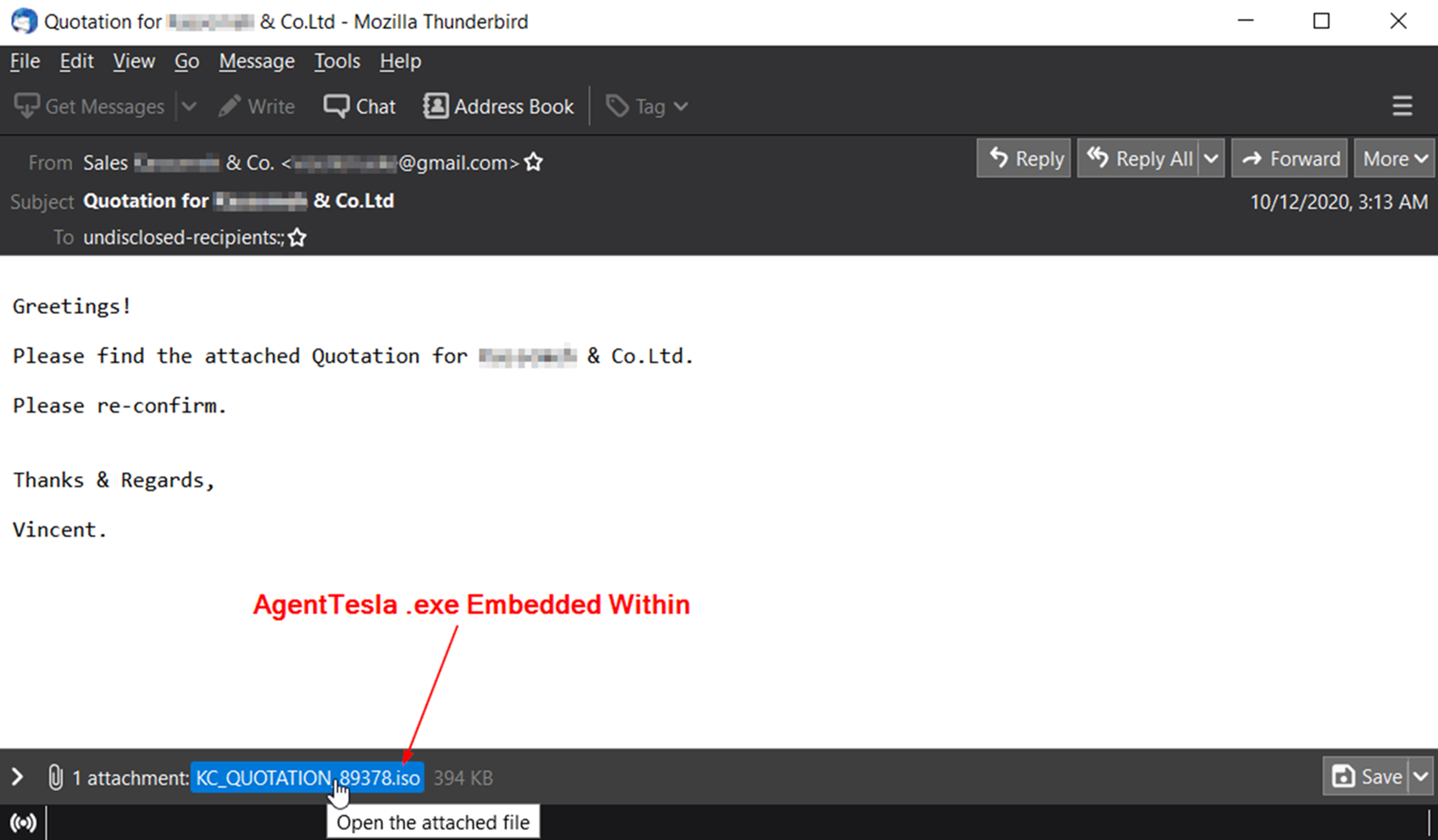
There has been a popular trend by threat actors to ‘chain’ malware attacks. We have increasingly observed attacks that begin as a remote access trojan to gain a foothold into systems. Once that backdoor is established, a banking trojan can be deployed to steal as much credential and financial data as possible from the victims. If the attackers decide the environment is suitable or they have compromised a high-value target, then additional data exfiltration and an end-stage ransomware deployment may be the final payload delivery.
Phishing Threats via Living Off the Land
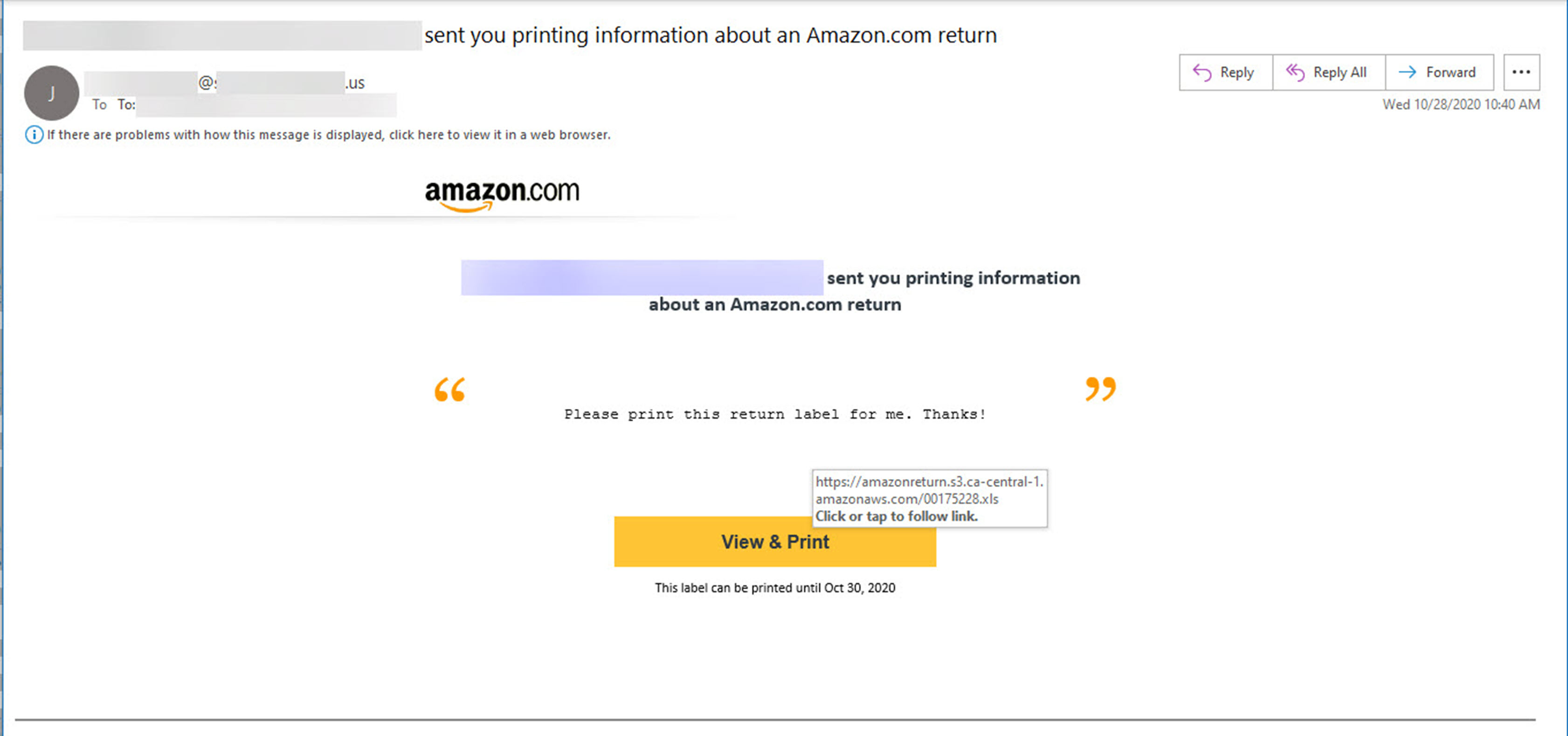
Malicious “living off the land” (LOtL) attacks attempt to fly under the radar by utilizing native tools that already exist in the target environment. Malicious actors leverage these existing tools and processes to commit their malicious activities while hiding among the white noise. LOtL phishing attacks are increasingly relying on the same methodology. These attacks attempt to blend in by leveraging well known services that are already seen in daily legitimate traffic. They do this to mask the true nature of their attacks and to evade capture.
We have been seeing this sort of activity for years, but in 2020 LOtL phishing saw a marked escalation of these tactics. We saw many otherwise very reputable services abused on a scale we had not yet seen. New services cropped up weekly as they were leveraged by attackers to help distribute and host their attacks. We even saw some product ‘spammers’ beginning to utilize the tactic while trying to avoid detection.
Some of the attacks involve sending messages directly from a legitimate platform while other LOtL attacks abuse the legitimate platform to either redirect to or host the payload — credential harvesting/phishing sites or malware delivery. Some of these attackers will even use all the above techniques in their attack by spoofing the brand they are sending from and using the platform itself for intended payloads. The top threat groups commonly rotate the platforms they abuse for these attacks to increase the efficacy of their campaigns.
Metrics
The volume of malware being delivered via attachment was down overall from last year as malicious actors opted for more targeted attacks vs the scattergun tactic we have captured over the past. Throughout the year, our Advanced Email Threat Protection quarantined about 143 million emails containing malware in a message attachment. Malware (as an attachment) activity peaked in January and again in March before falling off prior to a return to larger volumes in the fall of 2020.
Public Breaches

Fittingly, 2020 set new records with countless billions of company records breached. It is hard not to become desensitized to the constant flow of data breaches, but it is important to be aware of them as they may impact you eventually, if they haven’t already.
Utilizing a password management app is necessary nowadays because credential stuffing is as prevalent as it has ever been. Credential stuffing is the act of inputting harvested credentials into a myriad of services to see where else that password is being used and compromising said accounts. This Wired article does an excellent job of breaking down the top-rated password management applications.
Tax Scams Arrive Early
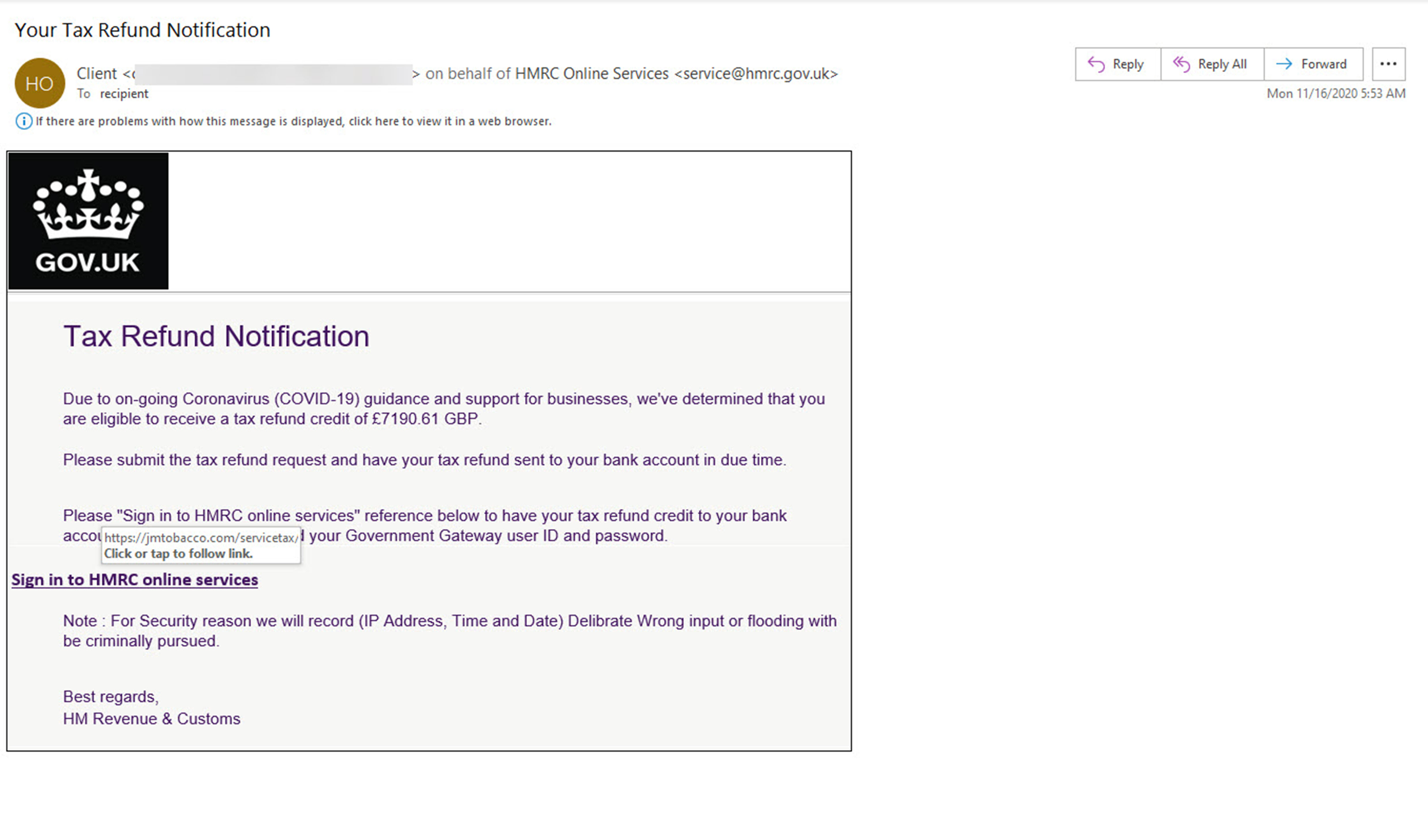
Even though tax season is still several months away, attackers did not waste any time attempting to exploit the event. In mid-November, we observed a phishing attack posing as an HMRC notification. Attackers were looking to capitalize on the uncertainty and need surrounding Covid-19 relief once again. This time utilizing the tax credit angle to gain access to their targets personal data. The massages claimed to be from the HMRC and contained a link to a phishing site.
Predictions 2021
The Dirty Dozen
- Covid19 vaccine themed attacks have already been occurring. We expect to capture state-sponsored vaccine mis-information campaigns in addition to e-crime groups spoofing companies poised to deliver the vaccines.
- Supply chain attacks will become more common. We have only just begun to see the fallout from the Solar Winds compromise but it is a prime example of what is possible with this sort of breach. We expect both e-crime groups and state sponsored actors to further escalate these attacks.
- Living Off the Land attacks will continue to be one of the most popular tactics by threat actors. They will expand their scope of companies to abuse to help blend in with legitimate traffic and confuse recipients.
- BEC threat actors may begin to integrate Deep Fake technologies into their attacks. Given that identity is often exploited in these attacks, look for attackers to leverage this technology to lend added credibility to their attacks.
- Security professionals will have to account for the “new normal” work landscape. Defenses will continue to evolve for in-office, work from home, and hybrid-model work scenarios.
- Phishing attacks will become even more personalized, localized, and geographically targeted. Much in the same way tech companies have been so successful in building personal profiles of their users to provide pinpoint ad targeting, we expect attackers to follow suit by building personal profiles of their targets using public data, information gained from stolen data and historical interactions with prior attacks.
- Ransomware double-extortion via threatening to leak data and holding locked data hostage will increase. With the number of hacking groups exfiltrating sensitive data before encrypting files, ransomware attacks must be considered data breaches now until proven otherwise.
- Ransomware has also resulted in death of hospital patient this year. Attackers will increasingly target hospitals and the U.S. government has warned healthcare providers of this threat.
- Nation vs nation cyberwarfare will increase and carry into space for electronic dominance.
- As prices and adoption for virtual currencies such as Bitcoin increase, so will attacks trying to steal the currency.
- While the 5G rollout continues to gain steam, the associated cyber risks grow. This is due to the move toward decentralized hardware, increased reliance upon software, IoT device vulnerabilities, and dynamic spectrums for sharing bandwidth.
- Mobile devices attacks will only increase over time. Their attack surfaces and possible vectors targeting them are numerous. The devices connect to many different networks, use many different communication protocols, routinely conduct sensitive communications and transactions, and are considered “softer targets” for attackers due to the lack of traditional security solutions that protect against threats.
