Lookout for Fake Outlook Messages
Blog
Thought Leadership
Lookout for Fake Outlook Messages
Troy Gill
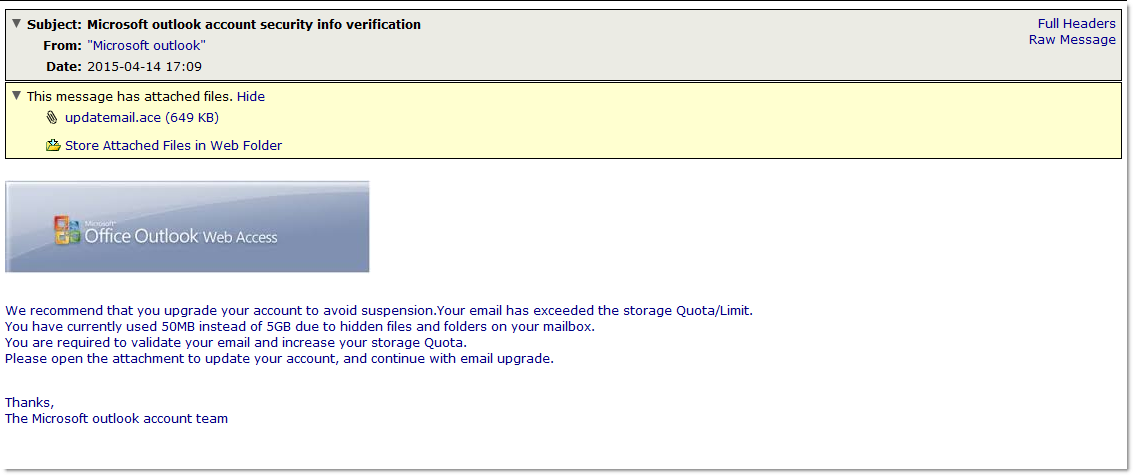
 Yesterday we began seeing a malware campaign posing as a message from “Microsoft Outlook”. The messages pose as a notification to the user that they have exceeded their mailbox storage limit. They advise the user to open the attachment to upgrade their account. The attachment in these messages is an ACE (.ace) archive that contains a malicious SCR (.scr) file. ACE is a data compression file format similar to the more commonly used ZIP or RAR files and though it is not as commonly used as ZIP or RAR, unpacking ACE files is supported my many third party archivers so it should not pose a problem for most users. The file inside is a rather large (643kb) SCR file named updatemail(dot)ace.
Yesterday we began seeing a malware campaign posing as a message from “Microsoft Outlook”. The messages pose as a notification to the user that they have exceeded their mailbox storage limit. They advise the user to open the attachment to upgrade their account. The attachment in these messages is an ACE (.ace) archive that contains a malicious SCR (.scr) file. ACE is a data compression file format similar to the more commonly used ZIP or RAR files and though it is not as commonly used as ZIP or RAR, unpacking ACE files is supported my many third party archivers so it should not pose a problem for most users. The file inside is a rather large (643kb) SCR file named updatemail(dot)ace.
While the majority of malware hitting our filters each day contain an smaller Trojan ‘dropper’ file that pulls down additional malicious software from the internet, this particular piece contains all needed functionality in the original attached file. In other words, it has no need to pull down more malicious software from the internet to do its damage. Once executed the malware drops a file in AppData then adds to run regkey to ensure that it remains running on the system at all times in the future. It also immediately registers a hook to monitor keyboard input (keylogging) as well as setting up a listener on TCP port 49202. We also observed the malware attempting to harvest bitcoin that might be stored on the user system. We also observed a self-propagation functionality via smtp so we can likely expect to see more of these in the future.
File Name Updatemail(dot)ace MD5 7e46f98e98eb39d13ddfaa66551181b7 SHA1 6baeced8fdf6c93a024167fb961e5037b59e5006 SHA256 eb97f6d0a454e0034e06d16e69ab6dddbf9d3d8e790e66003d6b3cfebd9d29e7