Don't Get Phished out of Your Tax Return
Blog
Thought Leadership
Don't Get Phished out of Your Tax Return
Jonathan French

Yes, it's tax season again. Time to get all your financial documents in order in hopes for a good refund (or at least not owe anything). While many people file their taxes right away, other people sometimes wait a while. Spammers know they have a wide window of opportunity to defraud and spam users and companies during this time. This year's dark and trying times tax season has shown again that spammers are keeping up with tradition of trying to trick and infect individuals.
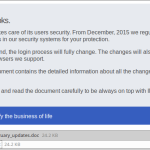
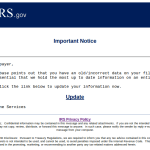
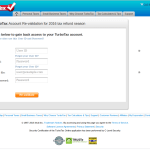
Tax season has a lot to do with following procedures and having your documents in order. No one wants the wrath of the IRS. The individuals that run malware campaigns use this as a tactic against users and send out campaigns that mention changes in policies or some new document that was processed and you need, or simply try to scare people in to doing something. Many of these campaigns are with standard malicious attachments in the message but many also have links in them disguised as legitimate links. These links can lead to compromised websites that offer malicious downloads or have fake website login pages to steal credentials. This is why having multiple pieces to you security like mail filtering, local antivirus, and web filtering can all work together to stop new threats coming in at different angles and using different methods.
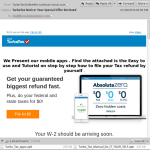
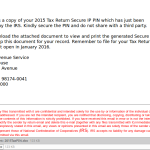
While some of the messages sent out, attachment or not, look convincing to many people...there are others that are less likely to fool an individual. But "less likely" doesn't mean "won't." Regardless of the effort put in to creating a malware campaign, there are bound to be users that will click links and run attachments if it makes it to their inboxes. The threats from these types of attacks luring users in to clicking things can span all platforms as well. Phishing sites usually work just as well on mobile devices as they do a desktop, and some campaigns even send mobile malware in the attachment (example with a malicious Android apk below).
To avoid getting "hooked," users should hover over links to see if the URL is leading where it says it is and double check file extensions for executables. Machines having antivirus solutions, showing file extensions, and making sure macros are disabled are also great steps to prevent infections.
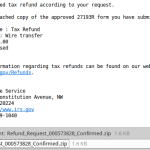
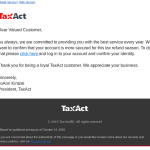
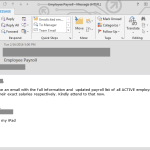
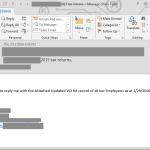
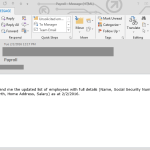
But it's not just malicious links, generic phishing emails, and attached malware to worry about. No, there are also customized spearphishing campaigns going on every day as well. These campaigns are tailored to the target businesses, and are infamous for being convincing. They use the clients domains, signatures, first names, and display names in the messages. All the items needed to make them seem genuine. And all the attacker needs do is send the spoofed message and then just use a Reply-To address they control. Most users won't pick up on the non-internal email address after they click "reply" and they can end up conversing with the attacker and be none the wiser.
Typically, these are aimed at financial departments within a company since they control the money, and the private data about who gets the money (aka employees). Wire transfer spearphishing happens year round using similar methods, but there is a spike that happens in spearphishing during tax season involving non public information, like payroll and W-2 data that can later be used to target individual employees.
Looking at the below samples with personal information removed, picture your own company's domain in the email addresses and your username being used. The message says it's from your CEO and he needs information sent to him. Ask yourself if you would second guess an email from your top executive asking about tax information. It is tax season after all. Unfortunately, with convincing spearphishing messages like these, employees can be "reeled in" and end up sending highly sensitive information back out to the cybercriminal. This same method is used to steal data and money from all sorts of companies out there.
While tax season is a time for financial departments to be on high alert for suspicious activity, it's good business practice for companies to have an IT security policy in place throughout the year. IT security practices that can save you a lot of heartache (and money) include:
Require double authentication through mediums as simple as a call, text message, or even a new email (not using the reply button) anytime company financial or employee non public information is requested (keep in mind how a non public information breach can make you non compliant with federal and local regulations). Adopt redundant, layered IT security solutions, such as spam/virus filtering, machine installed antivirus, and web filtering. Create a formal IT security policy if your organization doesn't already have one, and then train employees on the policies. Show some real life examples of why security is important and test users. Review and if necessary, update your IT security policy at least annually. Require the entire organization to re-certify in IT security policies annually as well.For more information on how AppRiver can help your business stay secure during tax season, please see our security suite of options.