Customized Attacks still on the Rise
Blog
Thought Leadership
Customized Attacks still on the Rise
Troy Gill
Customization in malware infection is a trend we have been seeing for years now but never has it been more prominent than as of late. From customized Spearphishing attacks to CEO fraud and BEC’s, today’s threat landscape is more fraught with pitfalls than ever before. Over the past few weeks we have been seeing an increase in customized and targeted malware attacks sent via email. Most of the recent attacks rely on malicious Microsoft Word Documents with embedded Macros. While the malicious macro approach has been quite popular lately we are now seeing the attackers go the extra mile with customization in the message and filename.
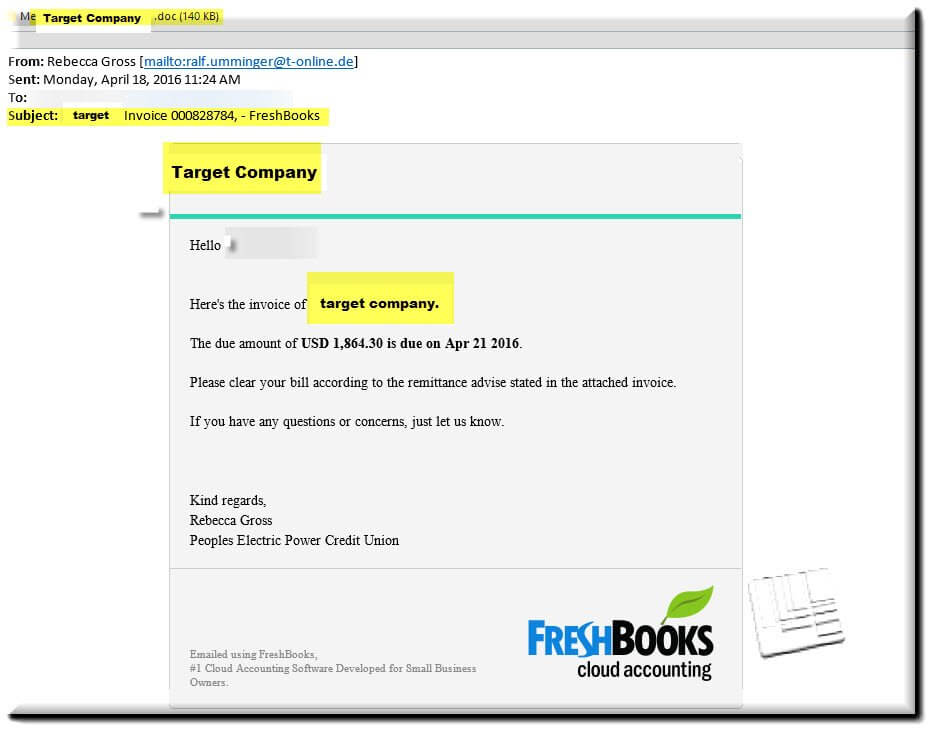
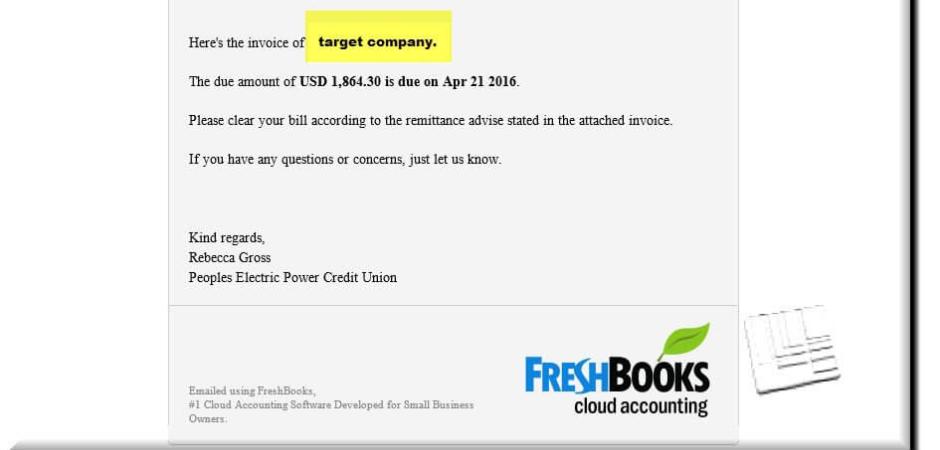
The messages pose as actual invoices from a legitimate accounting service called FreshBooks. Each email displays the name of the company that is being targeted, throughout the subject and message body. Also, each message contains a customized .doc attachment, complete with embedded Trojan, which uses the target companies name as well.
As you can see in the email below that the name of the target company is utilized throughout the message as well at the filename. (We have redacted the actual recipient company name and replaced it with “Target Company” and highlighted)
We have also seen evidence that the cyber-criminals responsible for sending these messages have made an effort to send these messages to the email addresses of actual key finance personnel. Naturally these messages will raise less red flags than the ordinary generic 'fake invoice' messages that we see day in and day out since having been littered with your own company name gives them the appearance of being legitimate. Of course, we have this campaign blocked with our own proprietary virus filtering software but it is currently still only being identified by 2 of 56 AV engines (according to virustotal). Finance departments everywhere should take notice at the recent trends and make sure they are up to date with awareness training. Network administrators may also want to consider disabling the use of Macro’s across their entire organization unless they are being relied upon for operations, this should be fairly easy to do with something like group policy.