JavaScript Malware with a Short Bio of Avira AntiVirus
Blog
Thought Leadership
JavaScript Malware with a Short Bio of Avira AntiVirus
Jonathan French

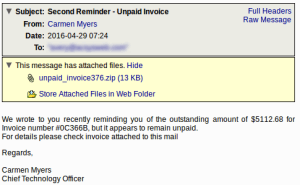
This morning, AppRiver began filtering a malware campaign around 3AM and is still sending malware in bursts. The campaign is similar to ones we had seen yesterday about unpaid invoices.
The message reads with an impatient tone in an attempt get users to urgently open its attachments. Giving users enough detail to think the file is legitimate is what gets users in the grasp of curiosity to open files. The attached .zip contains a single JS file inside.
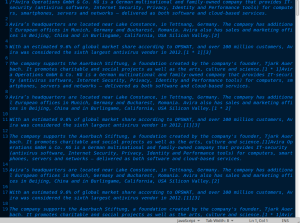
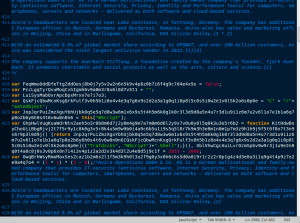
JS malware is pretty popular these days. We see campaigns in the tens of millions some days, with recent records being set just last month. While obfuscated JavaScript is pretty common, this one stood out from standard ones we see, mainly because inside the unzipped JS file, the contents of the file mostly contain information and history about the antivirus company Avira. The short information is just repeated throughout the file with the text being pulled from the Avira Wikipedia page.
We don't often see filler text like this within the actual payload itself so this stood out. This filler text pushed the size of the file up from about the 14K it needed to actually be, to around 470K. No doubt this was an attempt to throw of virus scanning while keeping the filler context somewhat relevant in a slightly ironic way. With all of the comments removed, the file goes from about 3000 lines to a little less than 90.
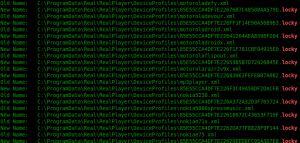
The payload that the JS file executes is the Locky ransomware that's been popular lately. The payload downloaded (bb1378b7cc4f2a9963c1b9c91b9a2fe5) has a hitrate of 14/57 on VirusTotal while the js file (various hashes) has a hitrate of 2/57.
As of writing this, there have been a little over four million messages quarantined in the campaign.