PayPal Themed Phishing Making the Rounds
Blog
Thought Leadership
PayPal Themed Phishing Making the Rounds
Troy Gill

Over the past few years, we have seen explosive growth in malware and targeted spear phishing attacks being distributed via email. While those threats have necessarily garnered a lot of attention, it’s important to stay aware that other more historically common attacks are also quite persistent and still pose a significant threat to consumers and businesses.

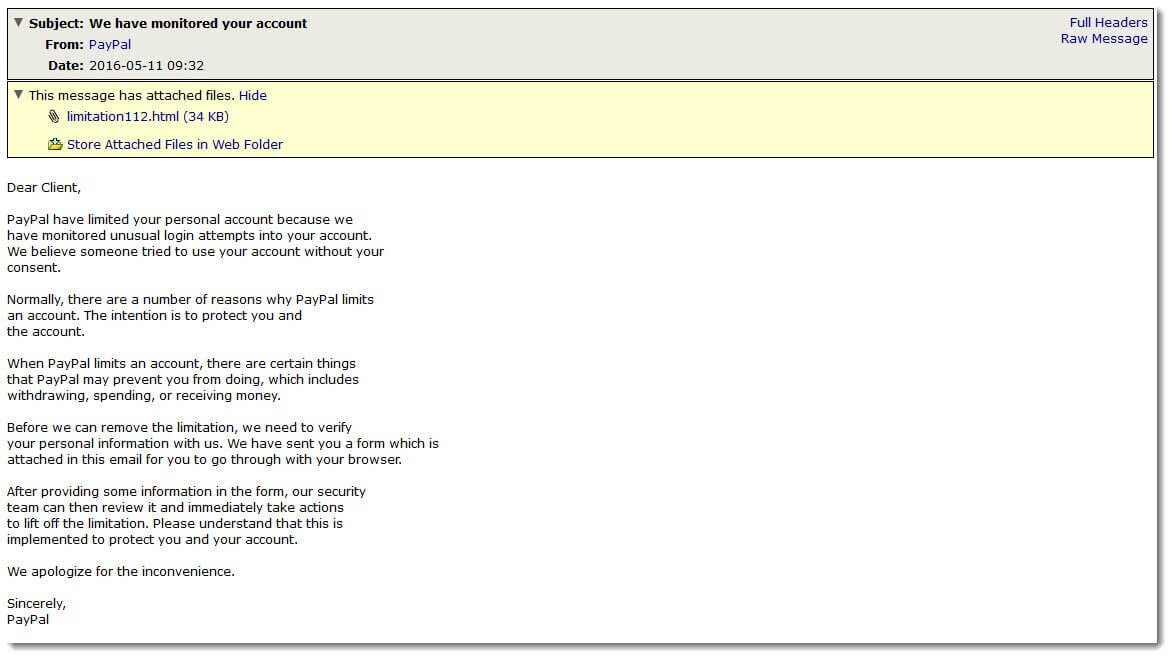
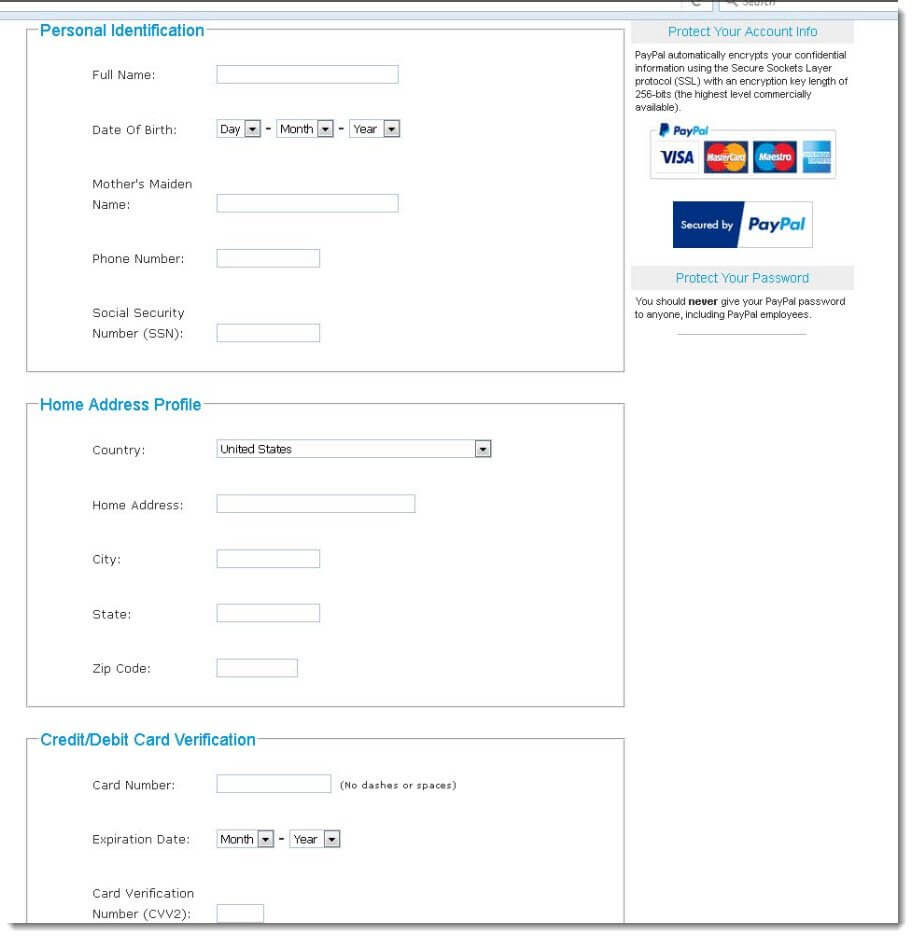
One phishing attack that we have been monitoring this week utilizes a cast net style (one size fits all) approach in its effort to steal sensitive personal and financial data-- all under the guise of a PayPal security message. These phishing messages rely on the ever popular fake security notice approach in an attempt to trick users into disclosing their personal information such as name, address, mother’s maiden name, social security number and credit card info. The attackers’ method for extracting this information from the recipient is through the inclusion of an HTML attachment posing as an official account verification page belonging to PayPal. Because an HTML attachment, when clicked, opens in your browser—the victim may even believe they are on the actual PayPal website.
Here's a look at the message and the attached phishing page:
Though most users are not accustomed to receiving HTML attachments, many may not realize how unusual it would be for a real company like PayPal to actually request a security verification in this manner. In fact, any real business (like PayPal) would almost certainly simply request that you navigate to PayPal on your own and verify things after logging in normally. If you ever find yourself on the receiving end of an email similar to this especially if it is asking you to provide any personal information, ALWAYS go directly to the site by typing it in your browser directly and not by following links of attachments within the email itself. As always, our customers are protected from these messages.