Malware Targets Scandinavia via Dropbox Abuse
Blog
Thought Leadership
Malware Targets Scandinavia via Dropbox Abuse
Troy Gill
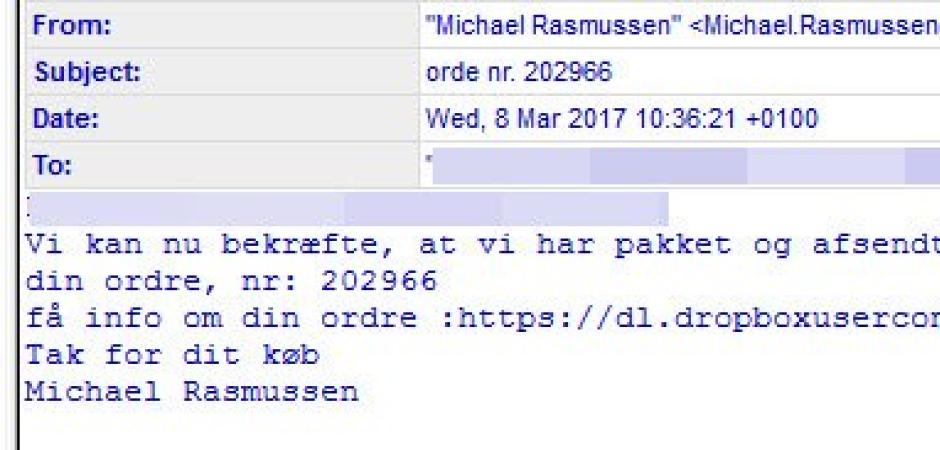
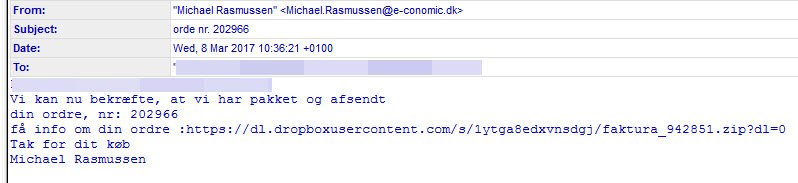
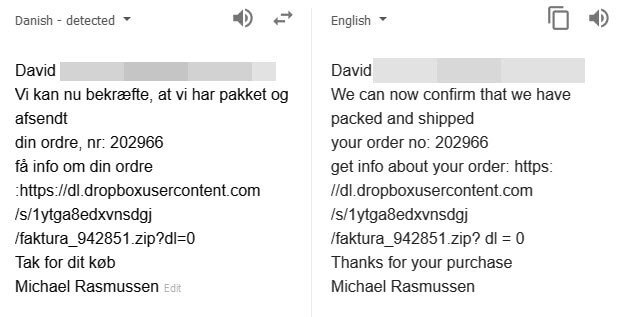
Early this morning, Denmark, Germany and several surrounding Scandinavian countries were hit with a large volume malware attack. The attack leveraged the legitimate cloud storage service Dropbox to host their malware payloads while attempting to disguise the links with random strings of characters and varying filenames. In the past 12 hours, we have quarantined thousands of these messages, which only represents a small percentage of the total message volume.
The messages purport to contain shipping details along with a fake "invoice:"
The links lead to a .zip archive containing a JavaScript file. The malicious JavaScript file in none other than the Trojan dropper some refer to as “Nemucod." We have seen this dropper family being used quite extensively over the past year or so. It has been leveraged in multiple Teslacrypt ransomware campaigns in past months. We have also seen evidence that the same group may be attempting to spread their infections using .xls and .doc files with embedded macros also under the guise of a fake invoice. 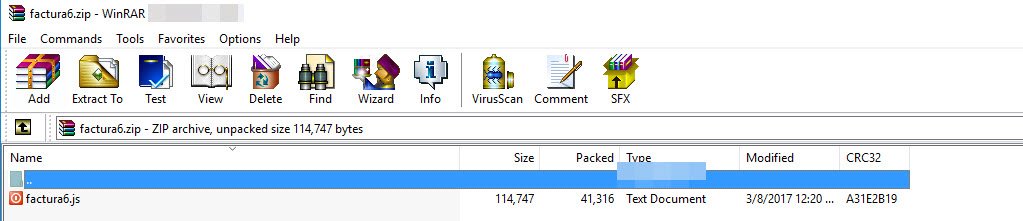
We have seen just about every file hosting service being abused at one point or another but Dropbox remains a very popular vector for attackers. Dropbox did identify and disable these links a short time after the attack happened but there was still a window of opportunity—which is often all they are looking for. Lately we have seen more email providers tighten restrictions on what type of files can be sent/received as an attachment. In response, malware distributors, whom are always looking for a weakness to exploit, have embraced file sharing as an alternative means to distribute those malicious files. We expect this trend to continue throughout the year.