Phishing attempts riding WanaCry coattails
Blog
Thought Leadership
Phishing attempts riding WanaCry coattails
David Pickett
After every large news-making event, we see malicious campaigns pop up quickly to ride the coattails. It is very easy for the scammers to modify their malevolent templates to match the latest headlines. They do this to prey on users emotions. The scams range from simple social engineering to malicious programs that promise to identify and remove infections from a machine.
Below are examples of a couple different phishing we've discovered attempting to take advantage of the WanaCry publicity.
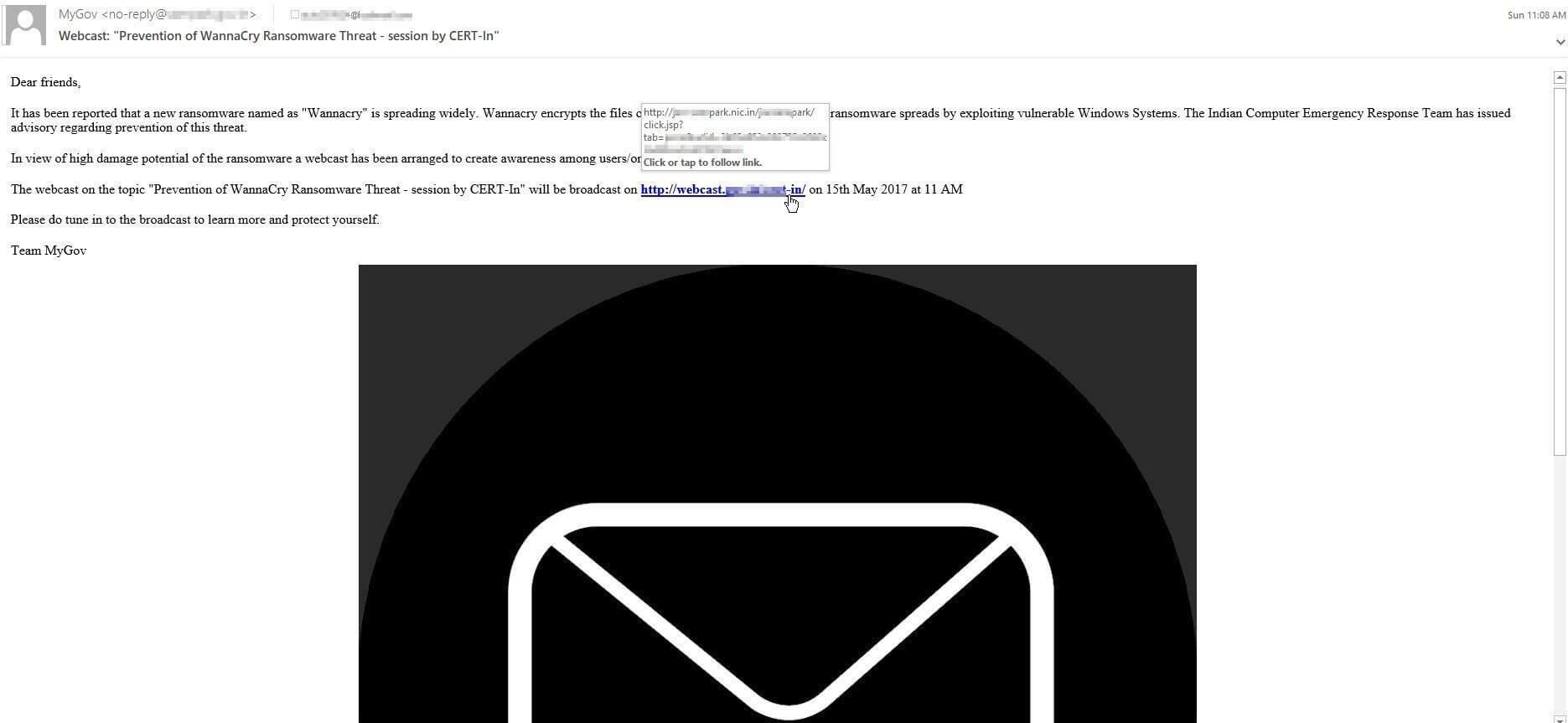
'Indian Computer Emergency Response Team'This one attempts to look like an Indian Computer Emergency Response Team (CERT). Typically, CERTs are a group of legitimate experts tasked to respond to computer security incidents. The scammers wanted to add a feeling of legitimacy and pass off their malicious site as a government webcast. The suspicious link and large inserted mail image are red flags.
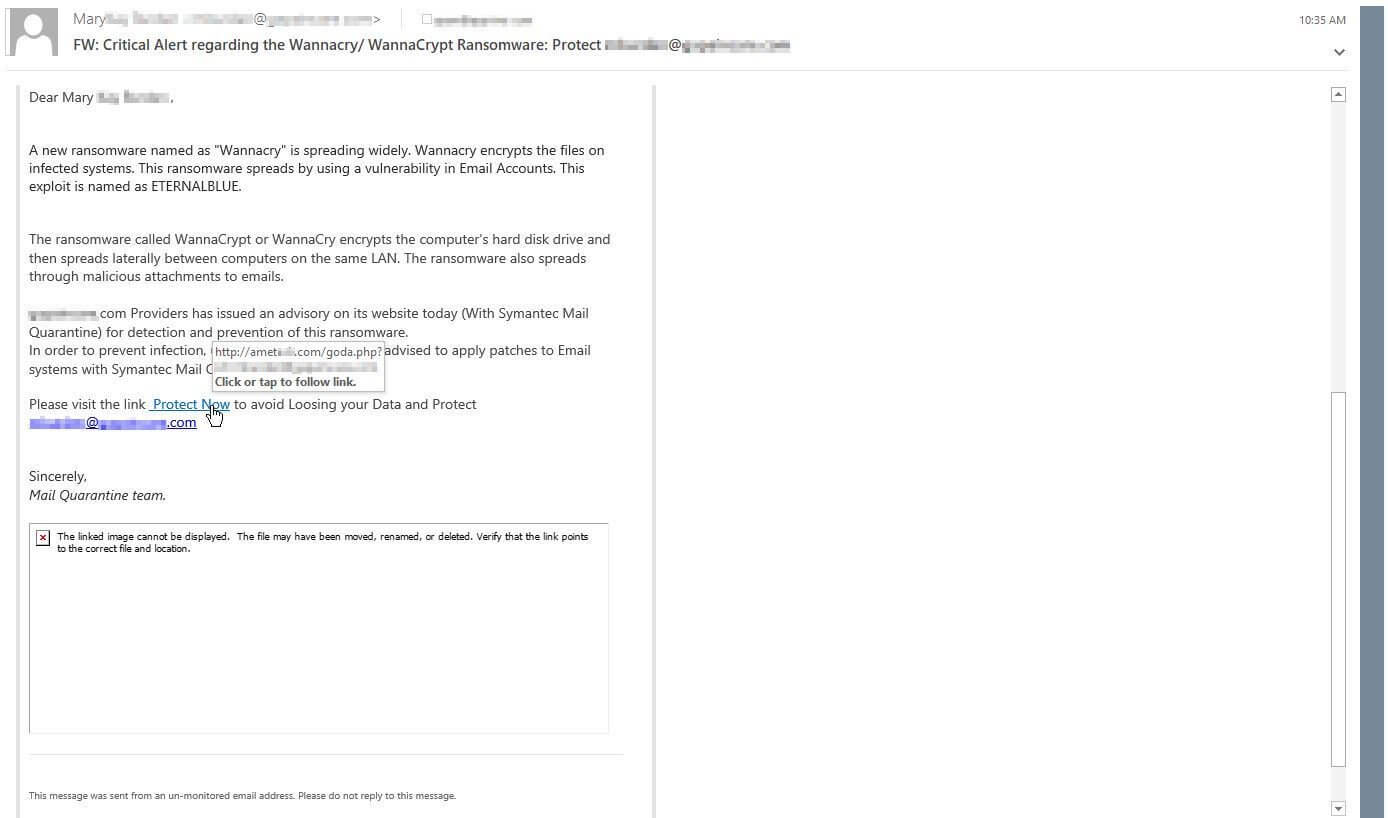
SymantecThis next example masquerades as the familiar security software company Symantec.
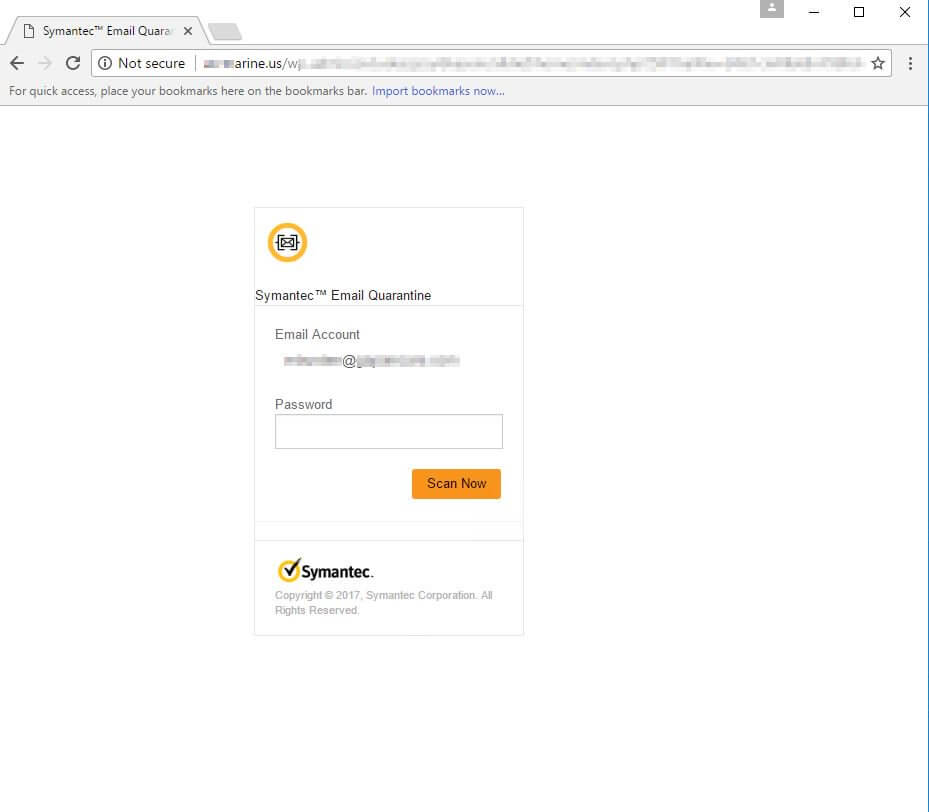
By following the hyperlink, readers will be redirected to a fake Symantec login page (see photo below). This site will insert the recipient's email address to appear more legitimate. Aside from increased filter evasion, url redirection allows the site to last longer before removal. This example pictured from last week, continues to be active.
A nefarious website operator may change the site at any time from a phishing attempt to something more malicious. It is important to not let the curiosity get the best of you. At AppRiver, we use isolated test systems to perform these actions to gather intelligence. Our in-house team monitors incoming campaigns like these 24/7/365. AppRiver SecureTide filtering protects you against these type of threats.