Malware Activity Heating Up
Blog
Thought Leadership
Malware Activity Heating Up
Troy Gill
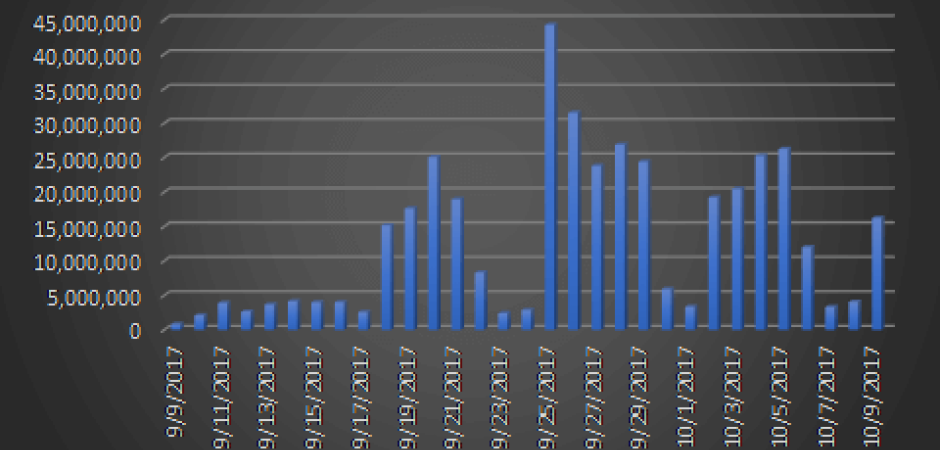
In September, the number of emails containing malware reached their highest levels thus far in 2017, as seen by our filters. So far, October is shaping up to continue that trend.
We have been monitoring this activity closely.
NECURS BOTNET PUSHING OUT MALWARE
During the past few months the most prolific vector for malware distribution via email has been the Necurs botnet. This has been the single largest distribution channel for the Locky ransomware family thus far in 2017. While we have seen Necurs varying its content being sent between Locky and Trickbot (a nasty banking trojan by its own right) over the past month, Locky still has been the most trafficked malware. Over the past 30 days we have quarantined more than 400 million emails that contained malware attempting to infect users across the world.
This morning’s Locky variant uses a simple approach, where the malicious payload hiding in a seemingly innocuous attachment. In the past 12 hours, we already have blocked millions of this particular variant.
The messages come with an attachment Invoice- [varying strings] [dot]7z.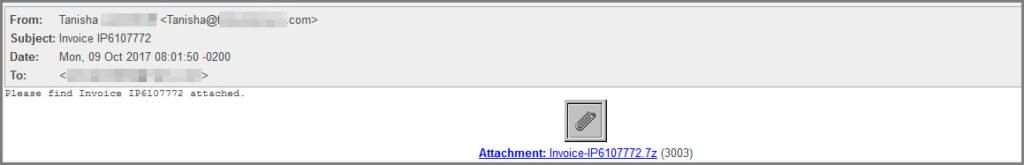
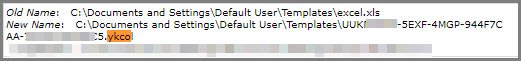
Inside is a .vbs file which is the ransomware downloader. The samples we analyzed were reaching out to cagliaricity[dot]it to pull down the full payload. Once it finishes hiding its processes in the system it goes to work encrypting files on the host machine, changing the file extensions to .ykcol, which is “Locky” spelled backwards.
Once the encryption routine has been completed the user is presented with a ransom screen and instructions on submitting the ransom payment.
On average, these payments have been around $1,300 USD, but since Bitcoin prices varies daily so do ransom amounts. Bitcoin is the preferred payment method for these attacks. In the past 12 hours, we already have blocked millions of this particular variant.
ARE YOU CONNECTED?
Are you following AppRiver’s social media? Like us today on FACEBOOK, TWITTER, YOUTUBE and LINKEDIN