'Ammyy Admin' RAT Leveraged in Massive Malware Campaign
Blog
Thought Leadership
'Ammyy Admin' RAT Leveraged in Massive Malware Campaign
Troy Gill
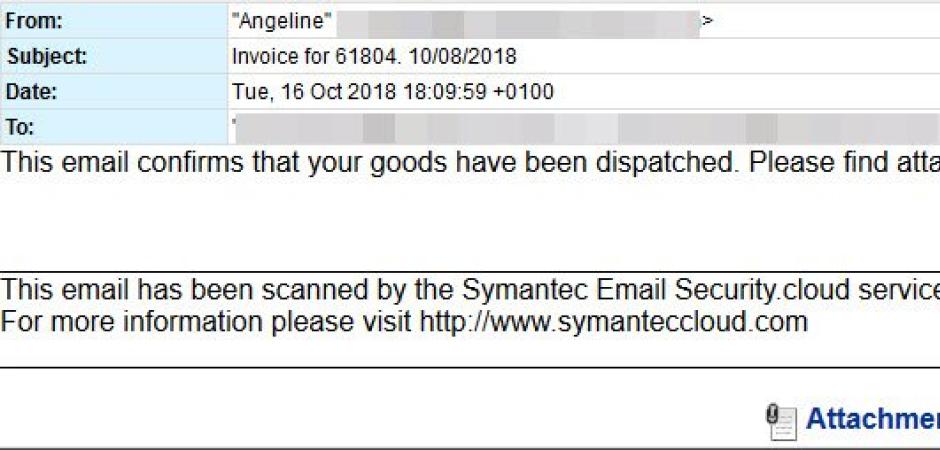
Late yesterday, while most people were just settling back into their desk after lunch… a large botnet [Necurs] began pumping out a massive malware campaign targeting millions of businesses and individuals. After the dust had settled, we had quarantined just over 25 million of these email-based attacks. This campaign had quite the volume in comparison to what we have seen in recent months.
The messages were rather generic in that they claimed to contain an invoice for goods purchased. The message body also included a phony Symantec security disclaimer. Attached to each email was a macro-enabled Word document.
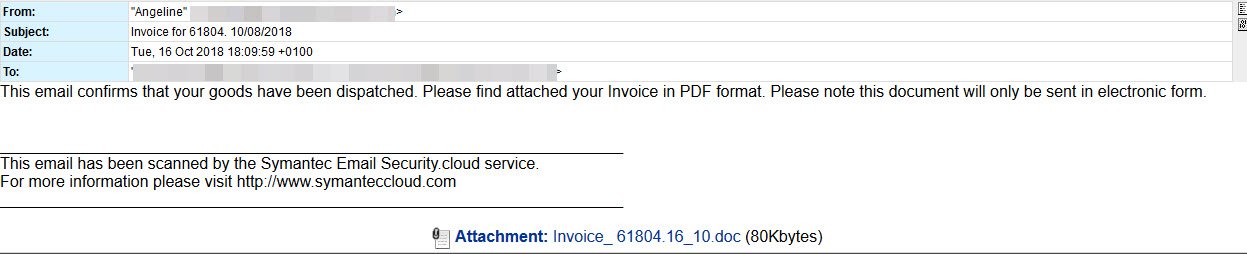
The attached file contained a malware dropper that, when executed, pullws down a Remote Access Trojan (RAT). We observed the malware communication with IP’s located in both Cape Town, South Africa, as well as in St. Petersburg, Russia. The RAT contained many dynamic analysis and debugging evasion techniques. Once complete, the attacker has nearly unfettered control of the infected machine. This includes recording screenshots, logging all keystrokes, reading clipboard data, etc.. During analysis, we also observed behavior that indicates the attackers intend to Ransomware the machine but not before they have had time to steal any-and-all of your sensitive data.
This RAT appears to be a newer iteration of one based on the leaked source code of the free “zero-config” Ammyy Admin remote desktop software. The first version of this RAT (based upon the Ammy Admin software) was first observed back in 2016. We have seen attacks launched leveraging this malware off and on since, but this has been the largest push we have seen to date. In fact, this was one of the largest volume malicious email campaigns we have seen this year.
Here's a look at the message arrival rates of this campaign:
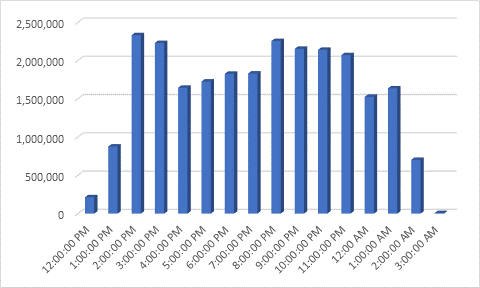
At the onset of this campaign, there was a very low detection rate of this file with less than ten percent of AV’s recognizing the file as malicious. This means the attackers likely have a lot of new nodes to explore today. However, thanks to SecureTide’s proprietary virus filtering technology this threat has been preemptively modeled and we were able to capture this campaign in its entirety.
