Banking Trojan Takes Aim at UK Businesses
Blog
Thought Leadership
Banking Trojan Takes Aim at UK Businesses
Troy Gill

Just after 10 a.m. this morning UK businesses were targeted with an email campaign attempting to infect networks with the Trickbot Banking Trojan.
Utilizing a similar approach to what we have seen in the past, the messages were crafted to appear as legitimate “secure emails” from Lloyds Bank. This approach is one we have seen before as the purveyors of this malware have often used Lloyds, HSBC, Barclays and NatWest themes in their malicious email campaigns. In that one hour we quarantined about 15K of these malware- laden messages for our customers.
ON TOPIC: TRICKBOT CAMPAIGN SPOOF DUN & BRADSTREET
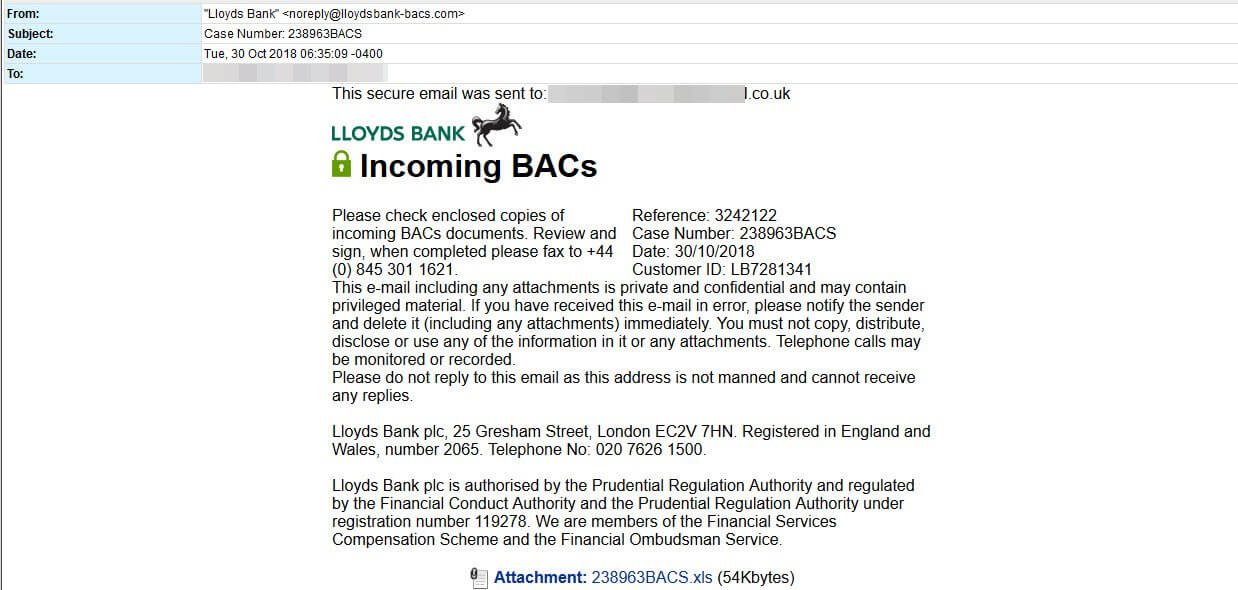
The attachment contains a macro-enabled spreadsheet. Once the macro has executed, it reaches out to a website located in Russia for the full payload, which is the Trickbot Banking Trojan.
Trickbot - Continually Evolving
Trickbot has received consistent upgrades over its lifecycle. It was seen leveraging the Eternal Blue exploit with MS17-010, thus giving it worm capabilities, not long after WannaCry had such success spreading via its use.
Late last year, it was updated with modules to target cryptocurrency wallets such as Coinbase. However, it’s primary functionality is to commit financial theft. It contains routines to disable Windows Defender and other AV, evade sandboxing, code-injection, keylogging, contact scraping and startup persistence. More recently it was updated with a module to encrypt targeted systems thus adding Ransomware to its repertoire. This evolution shows an effort on the part of the distributors to vary their business model to what works best to maximize their return per infection.
