Netflix Phishing Attack Targets Portuguese Users
Blog
Thought Leadership
Netflix Phishing Attack Targets Portuguese Users
Troy Gill

In the past 24 hours, AppRiver security analysts have seen a rash of emails attempting to fool Netflix account holders into believing their account has been suspended.
The emails, which are written in Portuguese, alert the user that their account has been suspended due to a billing issue. The recipient is then directed to a URL within the message that leads to the payload website, in this case a series of phishing pages to collect sensitive user data.
The attackers have leveraged Google cloud storage services to host the URL embedded in the message (as seen in the screenshot below).
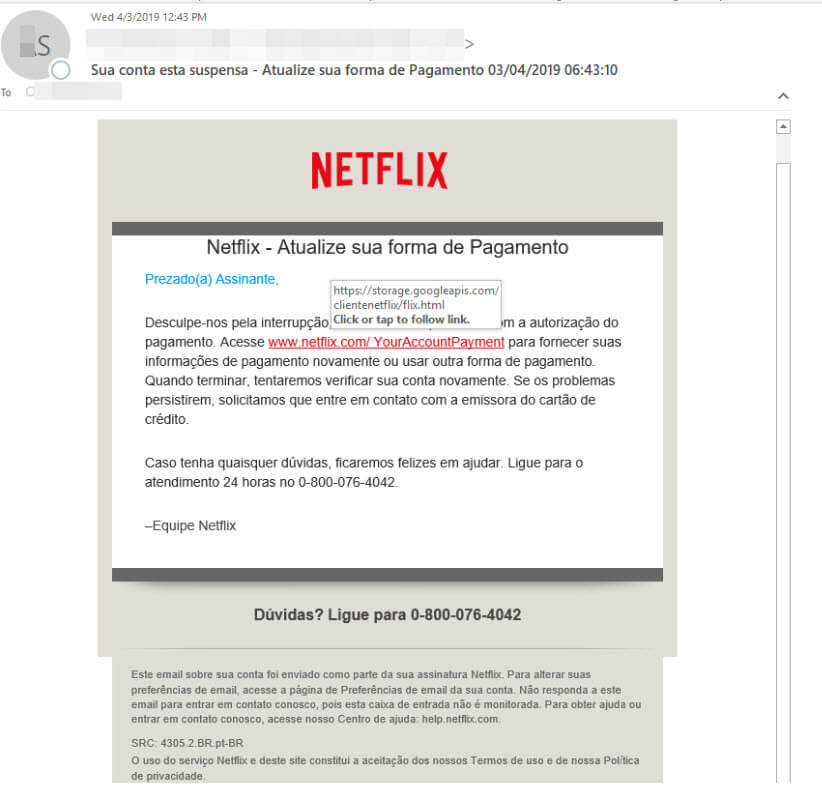
This link serves up a redirect to one of the phishing sites like the ones pictured below.
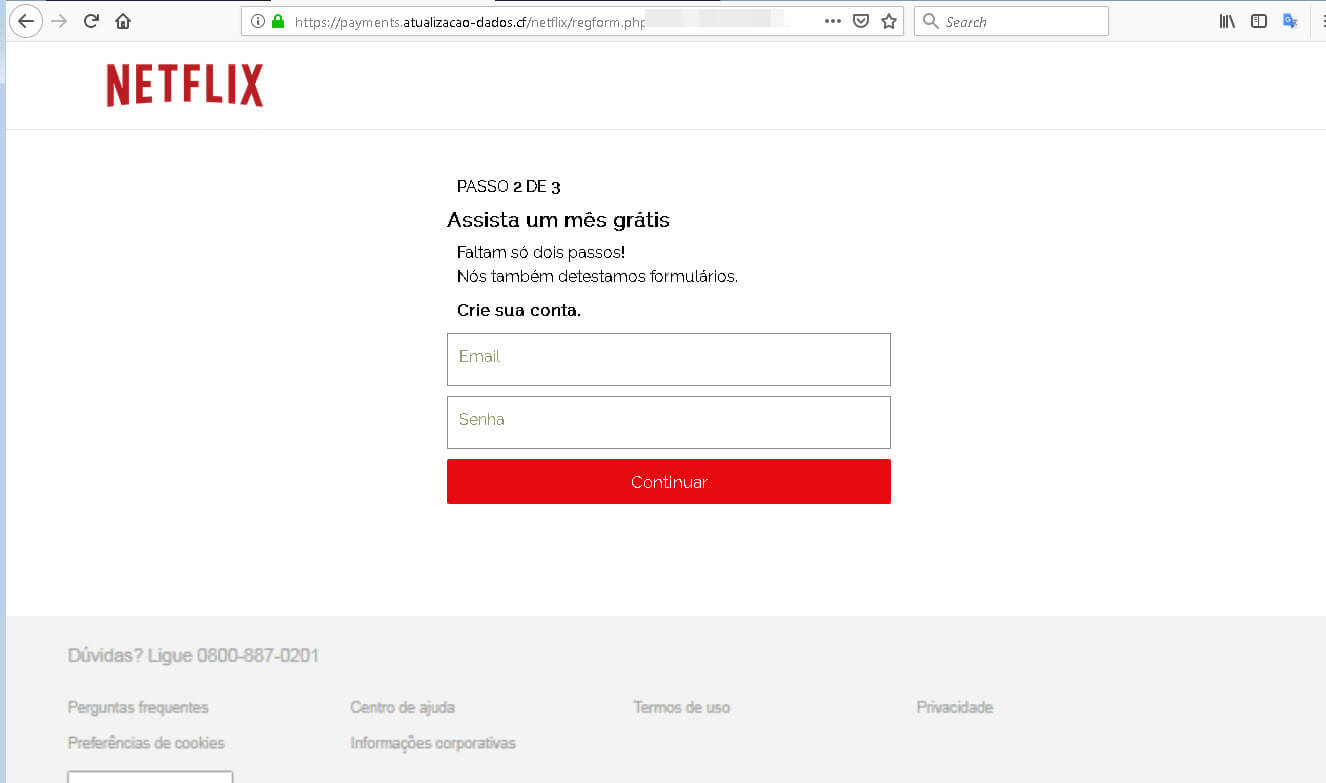
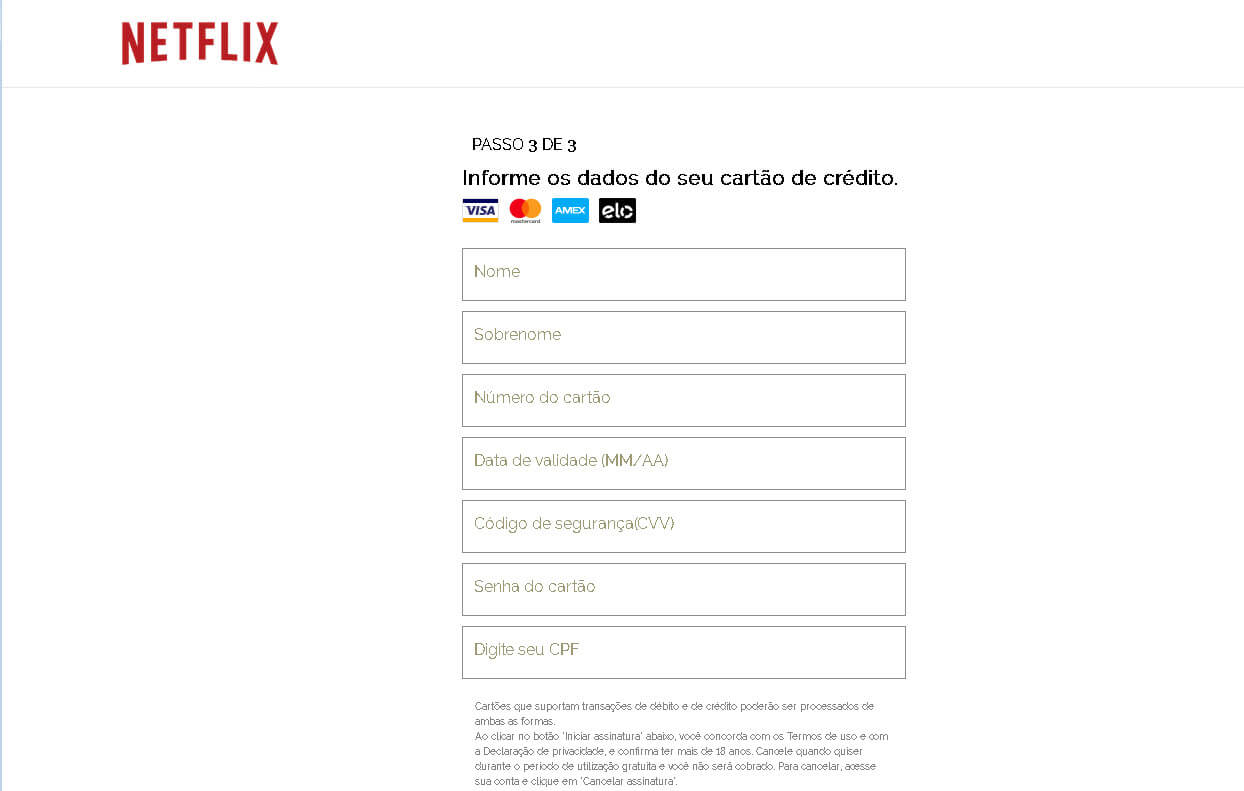
WHAT IS THE PAYOFF?
As you can see in the two phishing stages pictured above, the attackers are looking to harvest to valuable bits of data from their targets.
First they are attempting capturing the users Netflix email and password. The attackers can monetize these by selling them on underground marketplaces. It is not uncommon to find Netflix credentials for sale on the Dark Web for around $.50 to $1.00 per account. Barring detection by the end user or the service itself this would provide someone access to a Netflix account for as long as it exists, until a password is changed or until their activity is detected. At the cost of less than a dollar this makes for a handsome ROI for those unscrupulous enough to utilize stolen access to the service. And for the cybercriminals behind this operation, as is the case with many other similar attacks, this is a number game that can net them sizable profits when their attacks are delivered at scale.
Second, they are gathering full credit card info. If the attackers are not using the leveraged credit card info, they can easily sell the information on the Dark Web to a third party netting a nice little profit.
This attack demonstrates how cybercriminals will go after any type of data that they can profit from. It also underscores how many different types of attacks are currently leveraging legitimate services in their content to reduce suspicion around their attacks.
