Never Trust A Voicemail
Blog
Thought Leadership
Never Trust A Voicemail
Chris Lee

Voicemail phishing has been around for a long time, and it's not going anywhere anytime soon. Voicemail phishers are extremely proficient with obfuscation and well versed in getting around spam filters, so it is important to know what to look out for. But never fear, AppRiver Advanced Email Security (SecureTide) has an excellent track record of stopping these phishers in their tracks with our myriad of weapons in our arsenal. So let's dive in.
Example 1
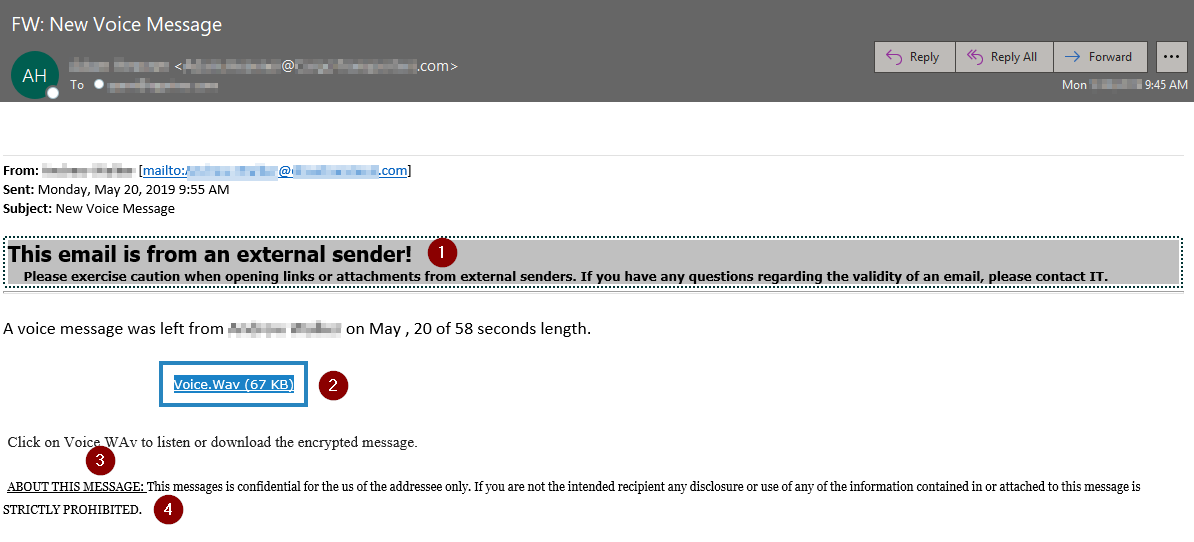
There are several fishy things to note in this email:
1. "This email is from an external sender!" This is a common tactic we see phishers use in an effort to appear legitimate. Some companies use inbound disclaimers like this for emails that originate from outside of your organization, if that's the case then please be familiar with your companies disclaimer, and if they don't match, then that's a huge red flag.
2 & 3. Here they're claiming that following the "Voice.Wav (67 KB)" link will give you access to a legitimate .wav (Waveform Audio File) file which is normal with a voicemail. However, the current standard for file extensions is lowercase letters so the capital "W" trailing the "." here is a red flag. It's true that you may also see file extensions in all uppercase letters like .WAV but that's much less common, you should raise a brow when there's a combination of uppercase and lowercase letters in a file extension like we see here.
4. Here the phisher includes a crafted confidentiality notice to lure you into a false sense of security. Skimming over it you'll notice grammar issues that you often see from foreign phishers: "This messages is confidential for the us of the addressee only."
It's important to know that these are all common tactics used by phishers, and, unfortunately, you can never let your guard down.
Example 2
Here's another example of a voicemail phishing campaign that we've seen in the past.
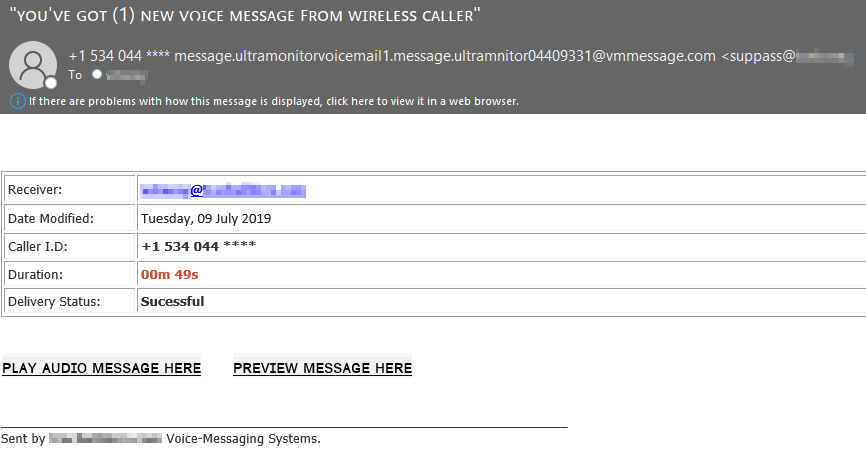
You may have noticed some of the strange characters in the subject of the email, my eye was drawn to that horseshoe-like character that they're substituting for an "O", well it turns out that it's a Georgian unicode character, specifically: U+10D8 : GEORGIAN LETTER IN. That character obviously has no business being there so that's abig red flag. These voicemail phishers enjoy using different obscure characters to substitute for other standard characters in an attempt to bypass filters, and the ones that have the most success are extremely proficient with obfuscation in all of its forms.
In this case and with most of these, the subject is base64 encoded and this is what it actually looks like behind the curtain:
=?utf-8?B?IsqP4bSP4bScJ+G0oOG0hyDJouG0j+G0myAoMSkgybThtIfhtKEg4bSg4YOYyarhtIThtIcg4bSN4bSHc3PhtIDJouG0hyDqnLDKgOG0j+G0jSDhtKHJqsqA4bSHyp/htIdzcyDhtIThtIDKn8qf4bSHyoAi?=
They alternate between base64 (=?utf-8?B? indicates that this is a base 64 encoded string) and quoted printable encoding (=?utf-8?Q? indicates that this is a quoted-printable encoded string) in order to obfuscate the subject, friendly "from" address, and sometimes even the recipient's email address.
Still, even with this new information, you'd think that this email would be simple to block, unfortunately, that is not the case. You may ask ... can't you block "PLAY AUDIO MESSAGE HERE" or "PREVIEW MESSAGE HERE"? After looking into the HTML (Hypertext Markup Language), which is the default email format for Microsoft Outlook and others, this is what we see:
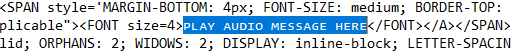
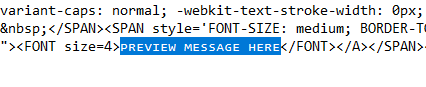
Something is off, right? It's almost like it's a different font. As it turns out they're obfuscating this by using small Latin capital letters, more specifically: U+1D18 : LATIN LETTER SMALL CAPITAL. Keep that in mind when you come face-to-face with one of these in the wild, they may look obvious or easy to stop, but in reality a lot of times it's quite the opposite.
Example 3
Now let's take a gander at this Office 365 voicemail phishing attempt.
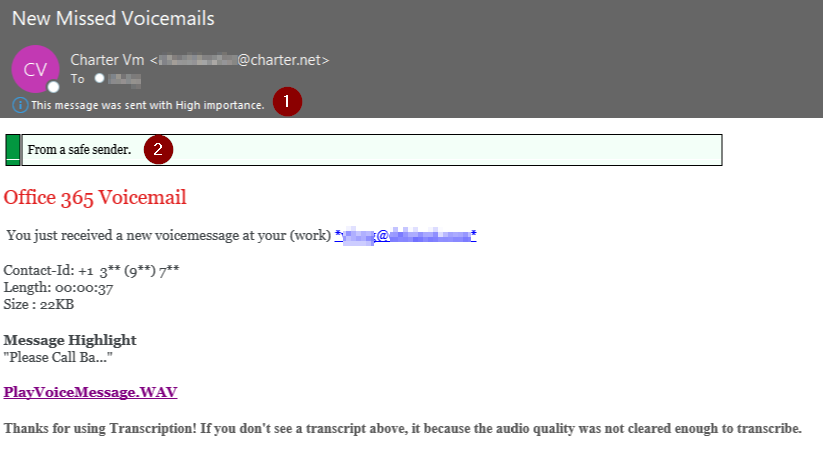
Here are a few things to look for when determining if this is legitimate or the work of a cybercriminal:
1. "This message was sent with High importance." Obviously marking an email with high importance often is done legitimately, but phishers often use it to force a sense of urgency.
2. "From a safe sender." Phishers love to insert messages like this at the top of emails to gain your trust. It should go without saying that if a voicemail is from an unknown sender, it's not a safe sender.
Example 4
Finally, let's look at the level of obfuscation these voicemail phishers been known to use to bypass various filters.
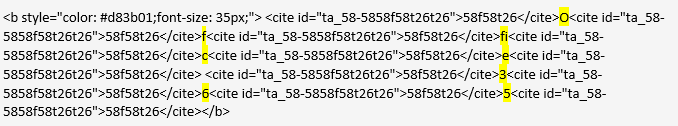
This looks like a harmless and legitimate Office 365 logo. Wrong. Shown below is what this logo actually looks like when viewing the source HTML code. I've highlighted how they've broken up Office 365.
Phishers have far too much time dedicated to obtaining your credentials, stay vigilant and don't let them win. If you're unsure how your company handles delivering voicemails, or about your companies use of inbound disclaimers, etc., then please reach out to your helpdesk/IT teams for insight. And if you are worried that you or someone you may know has been phished, reach out to your helpdesk/IT team for immediate assistance and update passwords.
Contact us today for a free trial of our Advanced Email Security
