THREAT ALERT - Malware Being Hosted On Azure
Blog
Thought Leadership
THREAT ALERT - Malware Being Hosted On Azure
David Pickett

THREAT ALERT - AZURE CURRENTLY HOSTING MALWARE
On Sept. 7, 2018, we first detailed how malicious attackers abused Azure's Custom Domain Name registrations to host credential phishing sites. On April 29, 2019, we released information on how compromised user data was exposed from attacks originating from phishing sites hosted on Azure.
Now the attacks have escalated to malware being hosted on the Azure service. Not only is Azure hosting malware, it is also functioning as the command and control infrastructure for the malicious files.
On May 11, 2019, malware researchers @JayTHL & @malwrhunterteam discovered the malicious software on Azure. It was reported to Microsoft on May 12 for abuse via ticket #SIR0552640. However, the original malware (plus additional samples uploaded since) still resided on the Azure site as of May 29, 2019 - 17 days later.
Malware Agent Detected by Windows DefenderNo service is infallible to being attacked or exploited. It's evident that Azure is not currently detecting the malicious software residing on Microsoft's servers. However, if a user attempts to download the executables, Windows Defender does detect the malicious files.
The first sample (searchfile.exe) was uploaded to VirusTotal on April 26, 2019. Windows Defender detects it as Trojan:Win32/Occamy.C. However, it does not appear the service is currently scanning Azure sites or, one could surmise that these files would've been detected by now. Another sample (printer/prenter.exe) was first submitted April 30, but also remains undetected on Azure servers.
Analysis of printer.exe shows the sample being a simple uncompiled c# .net portable executable file.
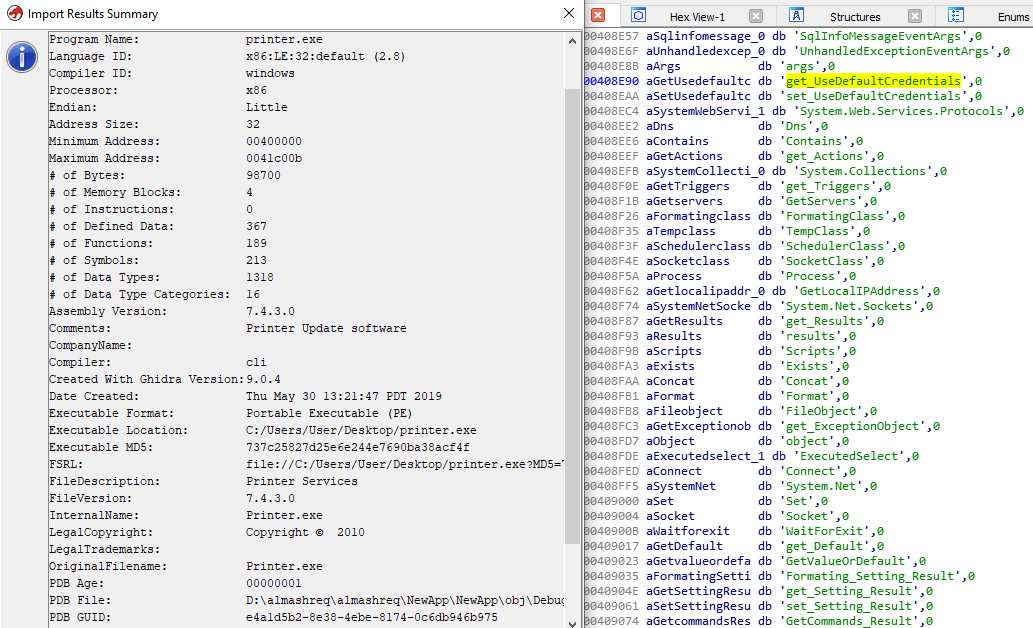
Using an uncompiled file is an evasion attempt for avoiding gateway and endpoint security solutions that heavily scrutinize downloaded binaries. Upon execution, the command line is invoked to run the the built-in visual c# compiler which activates the payload.
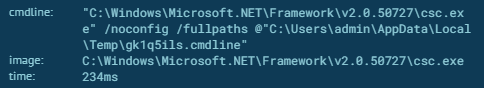
Once running, this malicious agent generates XML SOAP requests every 2 minutes to check-in and receive commands from the malicious actors Azure command and control site at: systemservicex[.]azurewebsites[.]net/data[.]asmx
 - Interactive analysis - ANY.png)
AppRiver Protection
There is no shortage of spam, malware, phishing, or nefarious websites AppRiver’s staff and systems continuously protect and defend against. Layered security solutions on top of 365 service is the strongest defensive posture for businesses to maintain. Malicious actors work around the clock, therefore, we at AppRiver work even harder to stay one step ahead. Our team is here 24/7, 365 days a year protecting and supporting clients and partners from security threats.
Contact us today for a free trial of our Advanced Email Security
