Undisclosed (BCC’d) Emails: Should You Trust Them?
Blog
Thought Leadership
Undisclosed (BCC’d) Emails: Should You Trust Them?
Chris Lee

It’s become increasingly apparent that malicious actors enjoy addressing phishing emails to undisclosed recipients via BCC. For those who may not be familiar, BCC stands for Blind Carbon Copy. That means no one can see who the email is going to. In the past month we’ve captured more than 20,000 phishing attacks addressing undisclosed recipients. It’s to the point that I must strongly advise users to proceed with caution when interacting with any email that’s been addressed to undisclosed (BCC'd) recipients.
Below are the 3 indicators that you may be dealing with an email addressed to undisclosed (BCC'd) recipients.

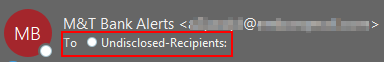
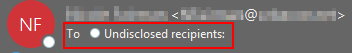
Now that you have the high ground and you're on high alert, you’ll want to exercise extreme caution if there is any file sharing service links present (Box.com, ShareFile, DocuSign, Dropbox) or a URL that’s been shortened (Bit.ly, Ow.ly, goo.gl). Like with all phishing, you’re still going to see links to sites that have been exploited, which can be difficult to identify. Additionally, a lot of these are coming from compromised mailboxes that you may have added as a contact, so err on the side of caution even if it’s a familiar name or email address.
In the below commonly found example, the attacker purports to be sending a secure dropbox document, however, when you hover over the link you can see that it leads to a blob.core.windows.net URL and not a Dropbox URL.
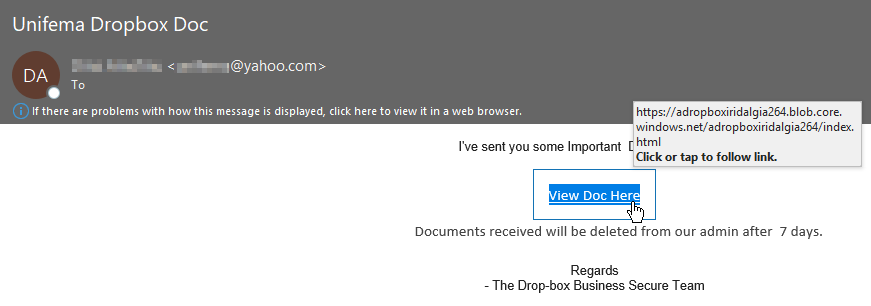
A key thing to remember when you’re determining if a site is phishing: If you see a multi-brand phishing page that offers login options for different email providers like you see here with Outlook, Google, AOL etc. it’s 100% phishing. If you were to click on “View Doc Here” in the email shown above, then you’d land on the phishing page shown below.

Below is another phishing page that’s found commonly in circulation with Box.com’s branding. You'll see that it's another multi-brand phishing page and provides options to log in with Office 365, Gmail, Hotmail, etc. Watch out for these, these are very effective against uneducated users and we're only going to see more of these.

As with anything, all phishing emails are not created equal. This next example is branded specifically to target Alibaba/DHL customers and it’s quite convincing at first glance.

If you were to follow that hyperlink (app.link is a regularly abused URL shortener), then you’ll be redirected to their crafted phishing page shown below. You’ll notice a common theme with a lot of phishing emails, a sense of urgency. They want you to do something, and they want you to do it now, and that something just happens to be your login credentials.
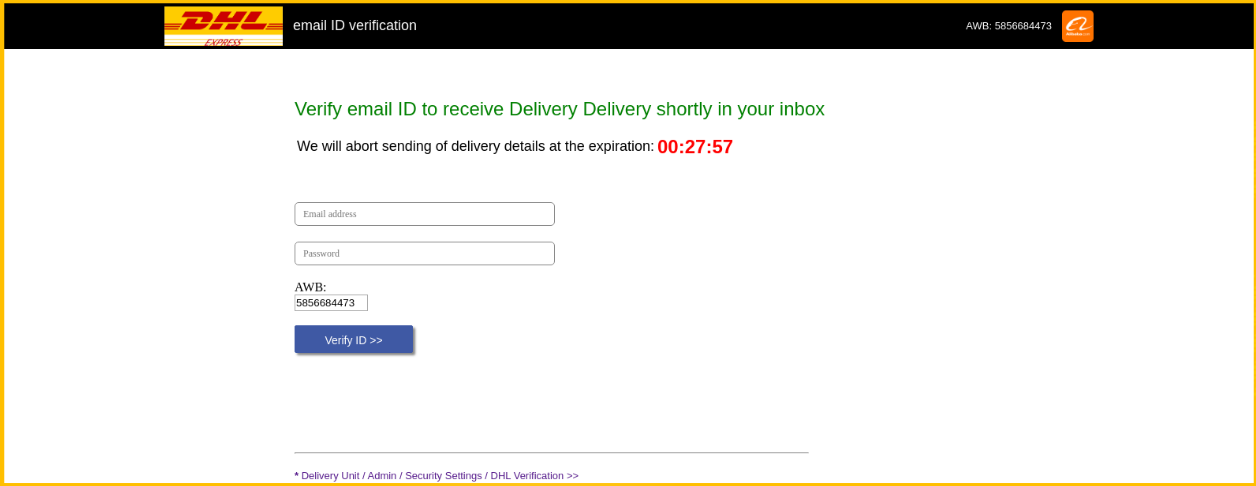
ABUSE OF A LEGITIMATE SERVICE
Now I’m going to take you through a full scenario where the malicious actor is abusing a legitimate service (OneNote in this case) from a potentially compromised account. Here’s the email in question:
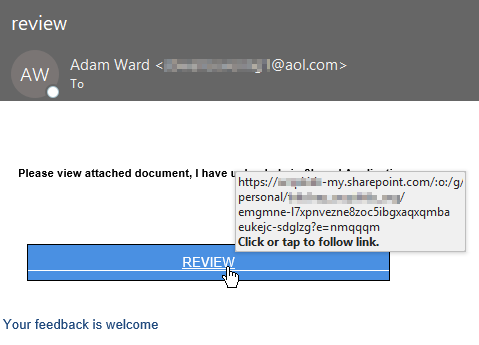
If you were to click on “REVIEW” it’ll pull up the senders OneNote and everything appears to be legitimate because it is a legitimate Microsoft OneNote page. That’s the major advantage of this tactic and why it’s so effective, these are legitimate services that are being used for nefarious purposes. They lure you into a false sense of security when this is merely a foothold to get you to their phishing site located on their exploited site.

Then if you were to select “Review Document” you’d land on the below credential harvesting page.

In summary, there’s nothing unique about these phishing attacks besides the fact that they’re all addressed to undisclosed recipients. But hopefully, you will look at undisclosed emails with a raised brow, because you should. If you are worried that you or someone you may know has been phished, reach out to the appropriate technical contact for assistance and update passwords.
Contact us today for a free trial of our Advanced Email Security
