Phishers Using Fake COVID-19 Tax Refund Notifications to Steal Credentials
Blog
Phishers Using Fake COVID-19 Tax Refund Notifications to Steal Credentials
David Bisson

Email scammers are using fake Coronavirus 2019 (COVID-19) tax refund notifications in an attempt to harvest victims’ credentials.
Inside the Phishing Attempt
Zix | AppRiver came across this phishing campaign in the middle of November 2020 when it flagged an attack email impersonating Her Majesty's Revenue and Customs (HMRC), a non-ministerial department which exists within the UK Government and which is responsible for collecting taxes as well as administering regulatory regimes including the minimum wage.
To create this disguise, the attackers used spoofing techniques to make the email appear as if it had originated from a client on behalf of HMRC Online Services.
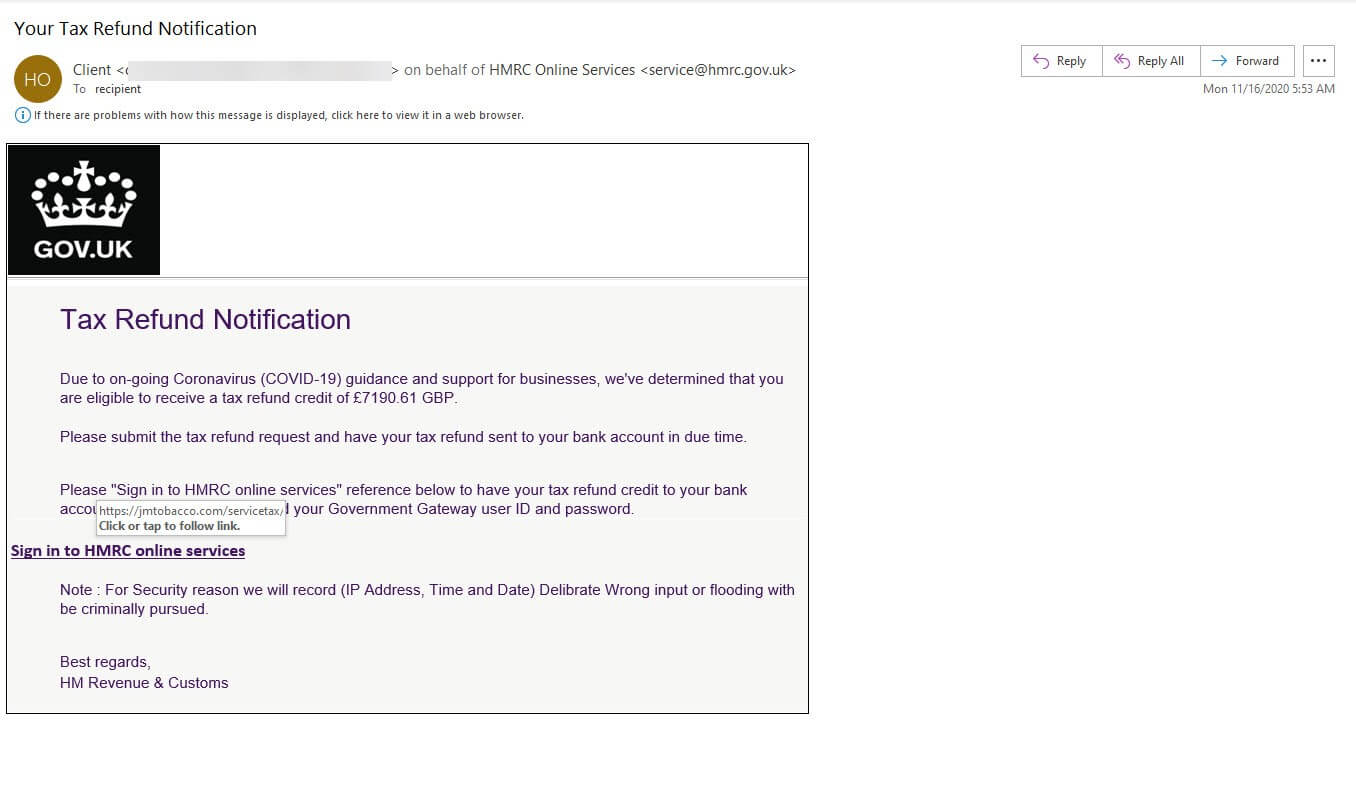
These spoofing techniques specifically tied HMRC Online Services to the email address service@hmrc[dot]gov[dot]uk. At first glance, this email address looks legitimate. It even uses “hmrc.gov.uk” as its domain.
But it’s not an official HMRC email account. It’s a fake. Indeed, a Google search revealed that this email address has featured in previous email attack campaigns. HMRC itself included it on a list of email addresses used by malicious actors to send out fake messages informing recipients that they were entitled to a tax rebate so long as they completed an online form.
![A screenshot of Google Search results showing some of the websites that warn against the email address “services@hmrc[dot]gov[dot]uk.”](/sites/default/files/inline-images/hmrc_2.png)
How fitting then that this email address appears in yet another tax-related ruse.
In this latest campaign, the malicious actors claimed that the recipient was entitled to a tax credit of £7,190.61 GB “due to on-going Coronavirus (COVID-19) guidance and support for businesses.” The email subsequently directed the recipient to click on the embedded link with the text “Sign in to HMRC online services.”
If the recipient took a moment to review the “legal disclaimer” included directly below this link, they would have determined the email to be hoax. The disclaimer’s grammar is seriously off. Not only that, but the message as a whole doesn’t make any sense.
Here it is in all of its muddled glory.
“Note : For Security reason we will record (IP Address, Time and Date) Delibrate Wrong input or flooding with be criminally pursued.[sic]”
Sounds legit to me.
If recipients missed the disclaimer, they still could have found the email to be a fake by hovering over the embedded link. The “Sign in to HMRC online services” text redirected users to a page located on the website for a premium cigar maker based in Los Angeles, California. (It’s unclear whether digital attackers compromised this website ahead of time.)
The linked page specifically mentioned “servicetax” in its URL. Looking this up on Google also revealed a few other hits on malware disallow lists.
At the time of writing, this linked page was down. But Zix | AppRiver followed the link upon its initial discovery and landed on a page designed to harvest victims’ credentials. Perhaps it even used the same online form as the other tax rebate operation referenced above.
Defending Against Fake Tax Refund Emails
The phishing campaign discussed above highlights the need for organizations to defend themselves against email attacks. One of the ways they can do this is by investing in an email security solution that’s capable of analyzing incoming messages for disallowed IP addresses, campaign patterns, suspicious URLs, malware signatures and other threat behaviors associated with ongoing digital attacks. This solution should be capable of looking for these indicators in real time while allowing legitimate correspondence to reach their intended destination.
