Hackers Using COVID19 Stimulus to Exploit End Users
Blog
Hackers Using COVID19 Stimulus to Exploit End Users
Troy Gill
It ended up taking just a few days longer than we expected but the malicious emails attempting to exploit the US economic stimulus package have begun to ramp up. Attackers ALWAYS have been relentless in their attempts to exploit every possible angle to accomplish their agenda. Human tragedy is, unfortunately, no exception.
For them, the current COVID-19 pandemic and resulting stimulus package are just opportunities to take advantage of the unsuspecting. As the topic began to gain media traction, attackers were quick to tailor their attacks to exploit the situation. In many ways, this is a perfect storm for them as they thrive on the inherent urgency, uncertainty and fear that comes with a pandemic. Through this, they are able to lower the defenses of their intended targets. Attackers have clearly recognized this and have embraced the topic to the extent as follows:
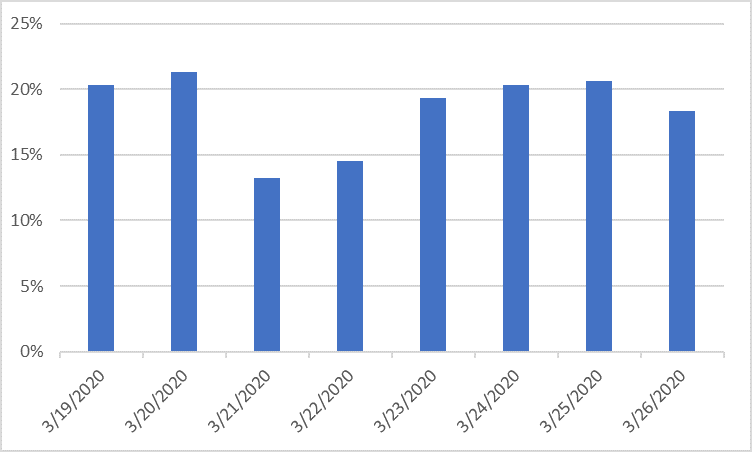
This chart represents COVID-19 themed emails as a percent of all “bad” email traffic. Currently about 1 of every 5 bad emails currently invokes the Coronavirus or COVID-19 terms to garner attention.
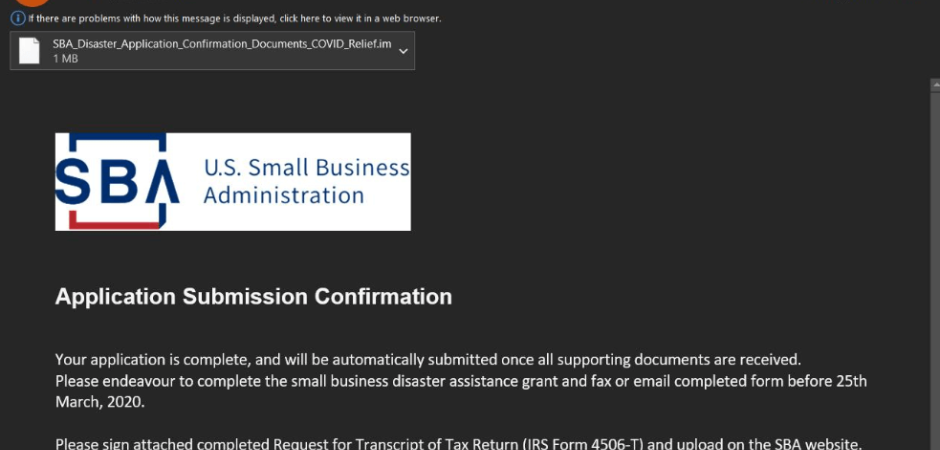
Since this new trend in COVID19-themed attacks has taken root we have been anticipating and monitoring closely for the next iteration of attacks – ones we assume will exploit public interest in stimulus relief funds. Though we have seen a few poorly formatted attempts in previous days, on Thursday the tide shifted as we are now seeing well-formatted and carefully crafted malicious emails spoofing the Small Business Administration (sba.gov) as stimulus relief communications.
Here’s an example of the current campaign and there will certainly be a variety of ones to come:
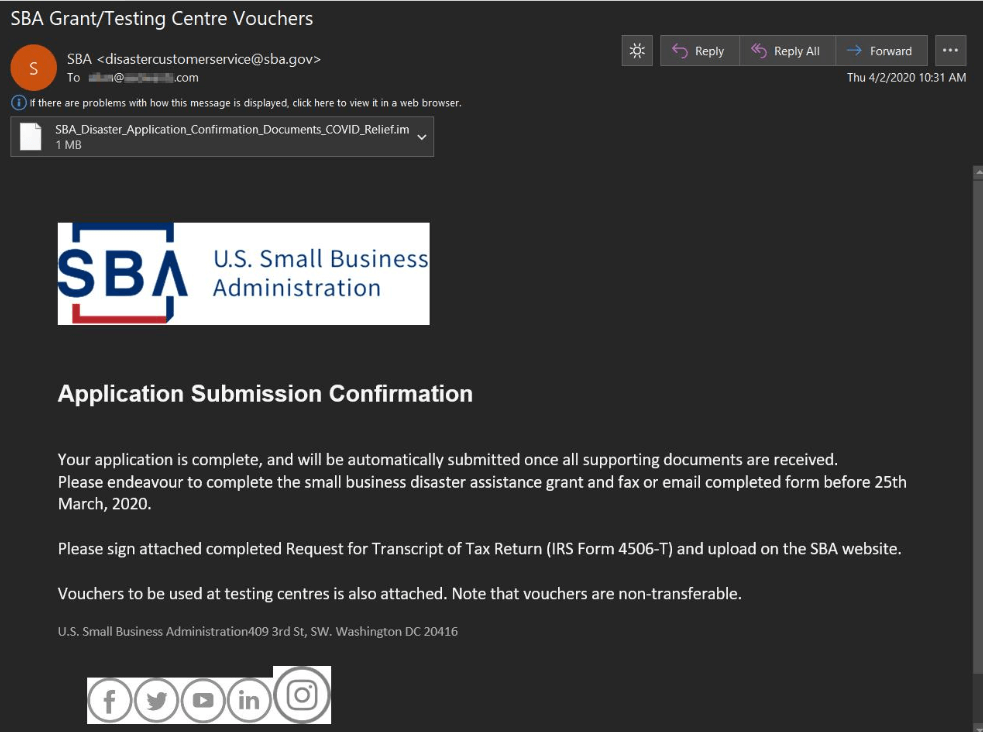
The malware payload in these messages initially delivers the Remcos remote access trojan, then drops Formbook, an info-stealer trojan which is fully capable of stealing sensitive data such as user credentials but also gains fairly wide-ranging control over the victim's machine thus allowing further code execution and data theft.
While the COVID-19 themed attacks have been going full steam ahead for weeks now, this is just the tip of the iceberg when it comes to attacks leveraging the topic of economic stimulus relief. We all need to be extra vigilant as we expect a multitude of new attacks to emerge in the coming days such as IRS notifications, phony internal communications from employers and other variations of these legitimately themed attacks.
