*UPDATE* Who Will Dridex Target Next?
Blog
*UPDATE* Who Will Dridex Target Next?
Chris Lee

Allow me to introduce our antagonist, Dridex. Dridex (also known as Bugat and Cridex) is a banking trojan that specializes in stealing credentials via the use of Microsoft Word/Excel macros and OLE's (Object Linking and Embedding). Lately their bread and butter has been utilizing malicious .xls files while purporting to be a legitimate delivery service (DHL last month, and UPS this month, FedEx next month?). On 3/12 we observed a large Dridex campaign comprised of ~100,000 malicious messages, then on 3/18 another ~257,000 messages. We achieved a 100% capture rate with these campaigns.
OLE’s have been quite popular as of late. The benefit for an attacker using OLE's is that the payload is contained as an OLE object inside the document itself. While with most macro malware, the macro reaches out to a server on the internet, downloads the payload, and then executes it. OLE malware is an all in one package for delivery. They can set the object to execute or run whatever file they please(exe, vbs, js, etc). Administrators can (and should whenever possible) prevent activation of OLE packages by modifying the registry key HKCU\Software\Microsoft\Office\<Office Version>\<Office application>\Security\PackagerPrompt.
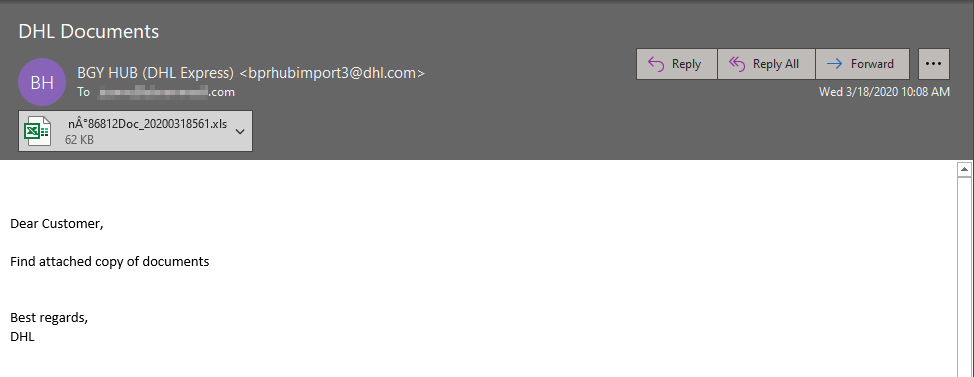
DHL Dridex email:
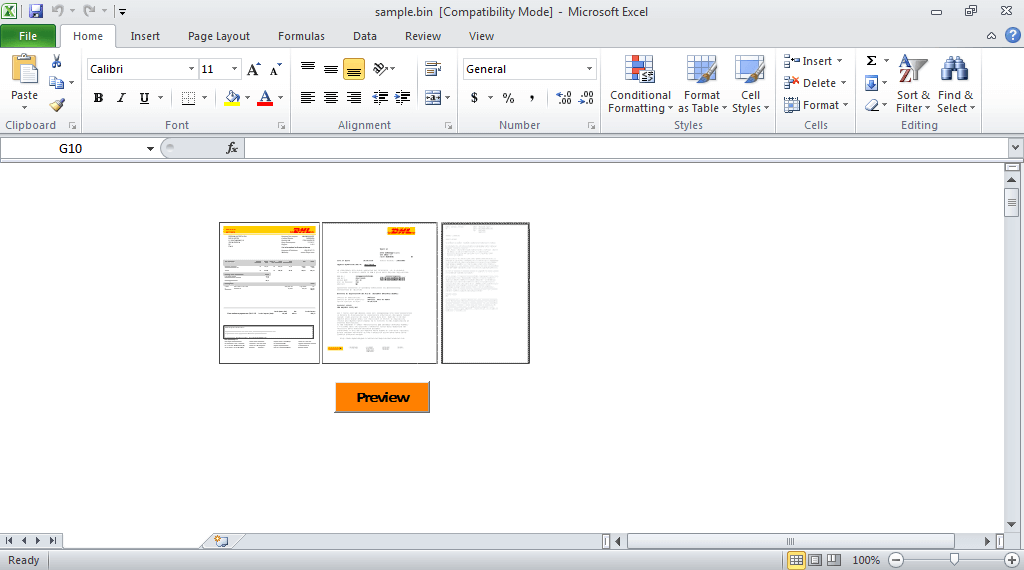
Here's a look at the file itself, these malicious actors like to utilize a button like you see here with "Preview" while including blurred images of legitimate looking documents to peak the end users interest.
This month on 4/20 we observed a Dridex campaign of ~132,000 messages, then they followed up on 4/22 with another of ~175,000 messages. In these campaigns they spoofed UPS, and we obtained another 100% capture rate on these campaigns as well.
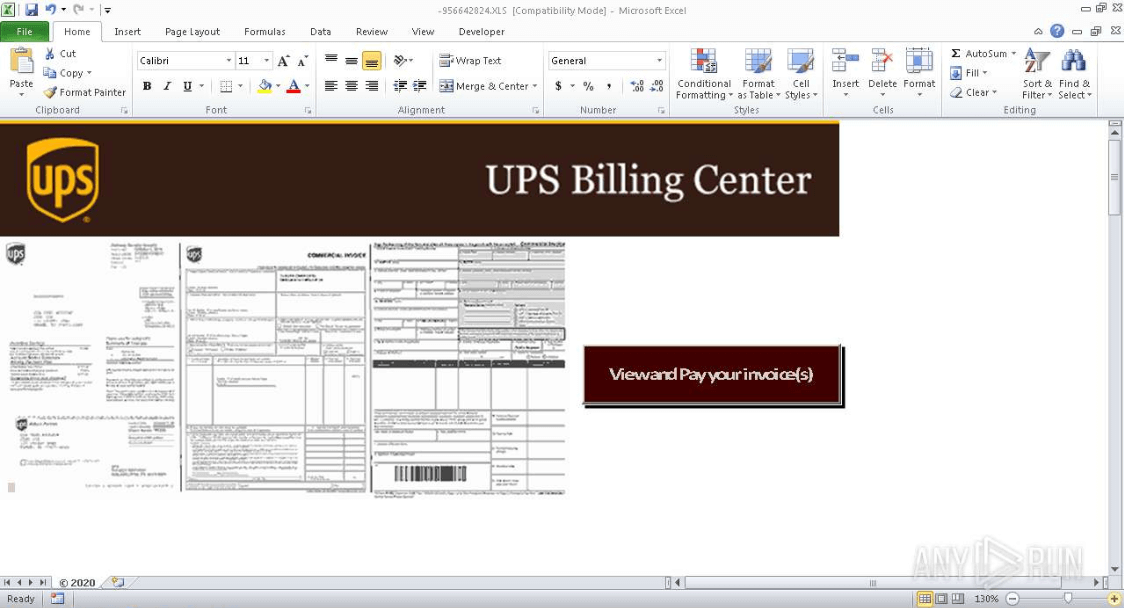
UPS Dridex email:

Taking a gander into this file you'll notice again the use of a button, in this case "View and Pay your invoice(s)" with some more blurred images of documents.
In these recent campaigns all of the network traffic points back to Russia, it would appear the coronavirus pandemic unfortunately hasn't slowed these malicious actors down. Additionally the OLE's are utilized to run an obfuscated powershell script which begins the infection process.
If trends continue my guess is they spoof FedEx next, but we'll have to wait and see. Stay vigilant and steer clear of any emails you may encounter that draw any similarities to these samples. Always reach out to your helpdesk/IT team for assistance if you have any suspicions about an email with an attachment or a potentially malicious link before interacting with it.
Defend your remote workers with AppRiver’s advanced threat protection tools today.
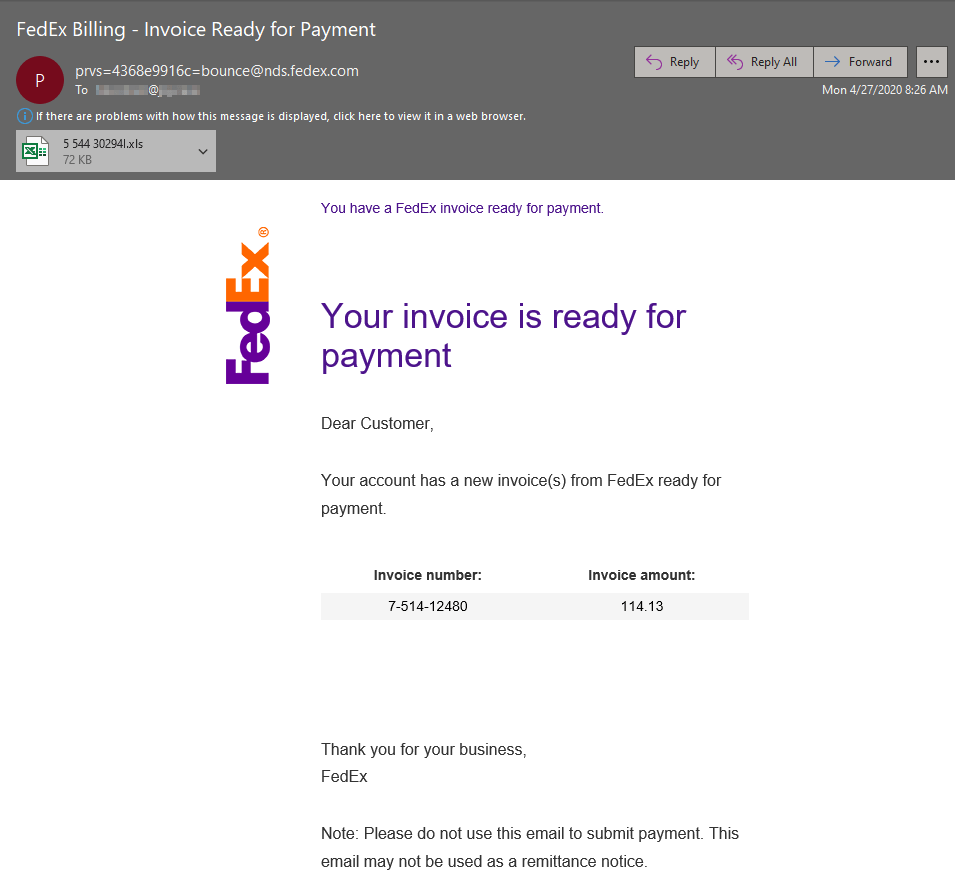
*UPDATE*
This morning the malicious actors behind distributing Dridex did indeed purport to be FedEx as I predicted. This time they stepped up the volume to ~212,000 messages. The next logical assumption is that they spoof USPS, please stay vigilant. Below is one of the sample emails from this mornings campaign.