Delivery Email Scam Delivers Buer Loader in Wake of Emotet’s Takedown
Blog
Threat Alert
Delivery Email Scam Delivers Buer Loader in Wake of Emotet’s Takedown
David Bisson

Digital attackers used a delivery email scam to deliver the Buer Loader just days after the Emotet botnet’s takedown.
A Boxed-up Buer Loader on Its Way…
Researchers at Zix | AppRiver spotted the delivery email scam at the beginning of February.
The attack email arrived with “order 4316624 Package” as its awkward subject line, and it used branding stolen from DHL to trick the recipient into thinking that it was legitimate.
Under this disguise, the email informed the recipient that the shipping service was preparing to deliver to them an Express package weighing 2.9 kg. It went on to notify the recipient that they could track the package using the information provided in an attached Excel spreadsheet.
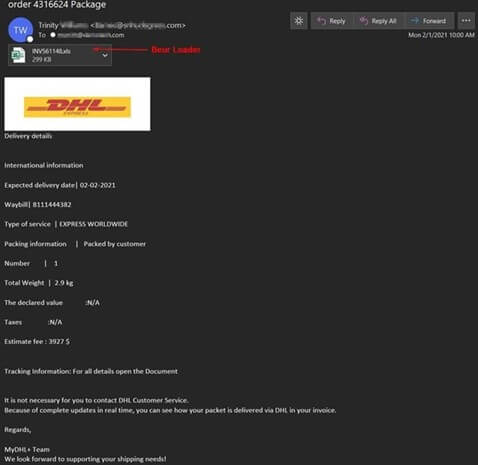
The security team at Zix | AppRiver took a close look at the attachment. They found it was a heavily obfuscated .XLS file that installed the Buer Loader.
Buer Loader: Its Attack Activity and Connection to Emotet
According to Threatpost, security researchers first began tracking a new modular loader named “Buer” by its developers in August 2019.
The first documented attack involving Buer Loader leveraged email messages that appeared to be responses to an earlier email conversation in order to distribute a weaponized Microsoft Word document. The file contained malicious macros that downloaded Buer as the next-stage payload.
Less than two months after that, researchers came across a malvertising campaign that used the Fallout exploit kit to redirect to Buer. The loader then dropped several second-stage malware strains including Smoke Loader and the KPOT stealer.
It was about a year later when SophosLabs observed digital attackers leveraging a malicious document stored in Google Docs. That document required the user to enable scripted content in order to interact with it. Once activated, the file loaded Buer, which installed Ryuk.
This was one of the first instances in which the security community witnessed ransomware operators embrace Buer as a means of distribution. It was also one of the first times when security experts framed Buer as a possible “alternative” to Emotet.
That latter point is particularly relevant now in the wake of Emotet’s takedown back in late January 2021, an event which occurred just days before Zix | AppRiver spotted the Buer Loader attack discussed above.
In the wake of that international takedown effort, Emotet did earn a top spot on some monthly most wanted malware lists. But its activity still dropped by more than 10% compared to pre-takedown levels. And with Europol planning on mass-uninstalling Emotet from all infected hosts later in the spring, threat actors might be actively seeking a replacement.
How to Defend Against the Buer Loader
After digging a little deeper into the attack, researchers found that threat actors were offering a customized Buer malware loader and a working command-and-control (C&C) server to interested parties for as little as $350. This price makes it possible for threat actors of varying levels of expertise to stage email attack campaigns using Buer for the foreseeable future.
This highlights the need for organizations to defend themselves now against email-borne threats such as Buer Loader. They can do so by investing in an email security solution that uses advanced link protection, quarantine and attachment sandboxing, among other features, to analyze incoming messages for potential digital threats. This tool should leverage machine learning and automation to streamline this threat prevention process and thereby allow legitimate business correspondence to reach their intended destination within the organization.
