Hackers Spoof 401K Notices & Expose Stolen Data
Blog
Threat Alert
Hackers Spoof 401K Notices & Expose Stolen Data
David Pickett

Overview
Since mid-February, the Zix|AppRiver Secure Cloud has been capturing phishing attacks masquerading as TransAmerica 401k retirement plan notices. We decided to investigate these attacks and found the attackers had succeeded against victims who were not protected by a robust email filtering solution.
What was even more disturbing, the threat actors had stolen the victim’s credentials and left them in an open web directory within a txt file that allowed anyone to view the victim’s email addresses, passwords, IP addresses, geolocation, browser, and OS platform info.
How the Attack Works
The phishing attempt spoofs transamerica.com. At face value, the message appears as it could be legitimate. However, there is a malicious html file attached.
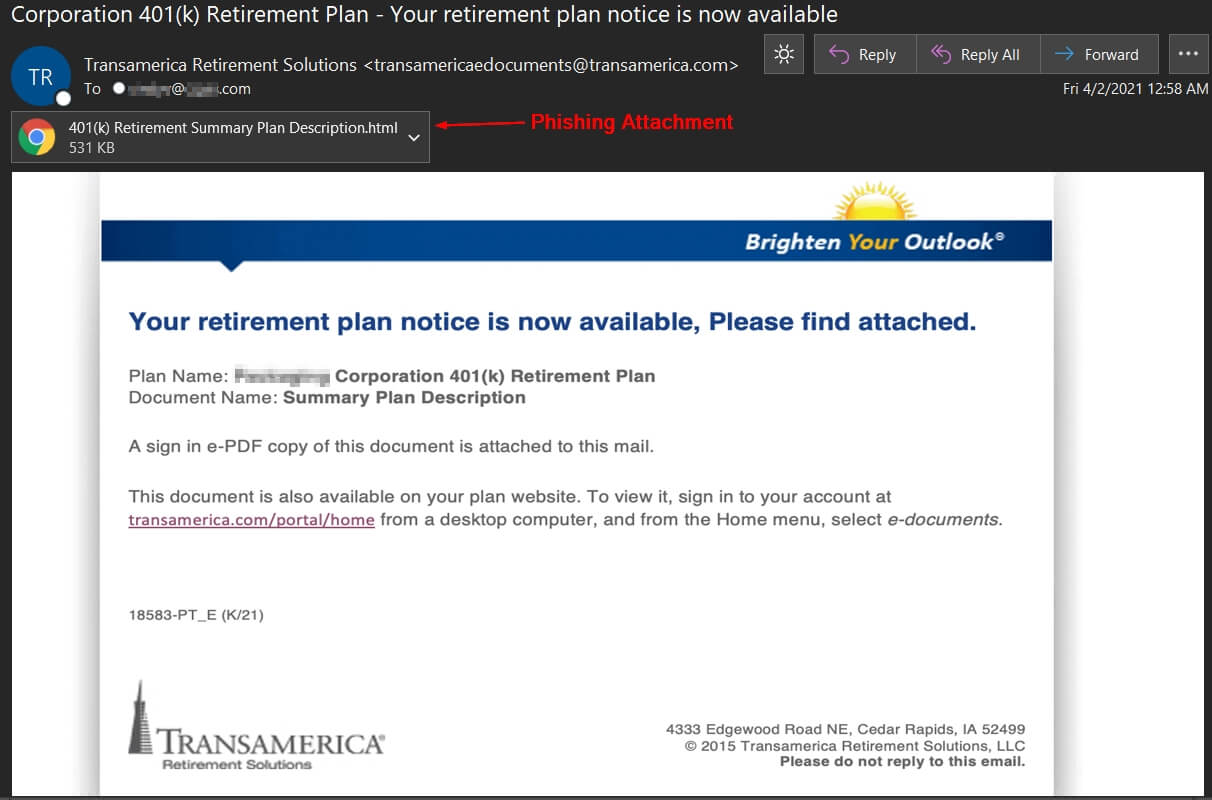
If the html attachment is opened, it will open locally in a web browser. This example gives the appearance the recipient needs to sign into Adobe’s Document Cloud to view asking for their email address and password.
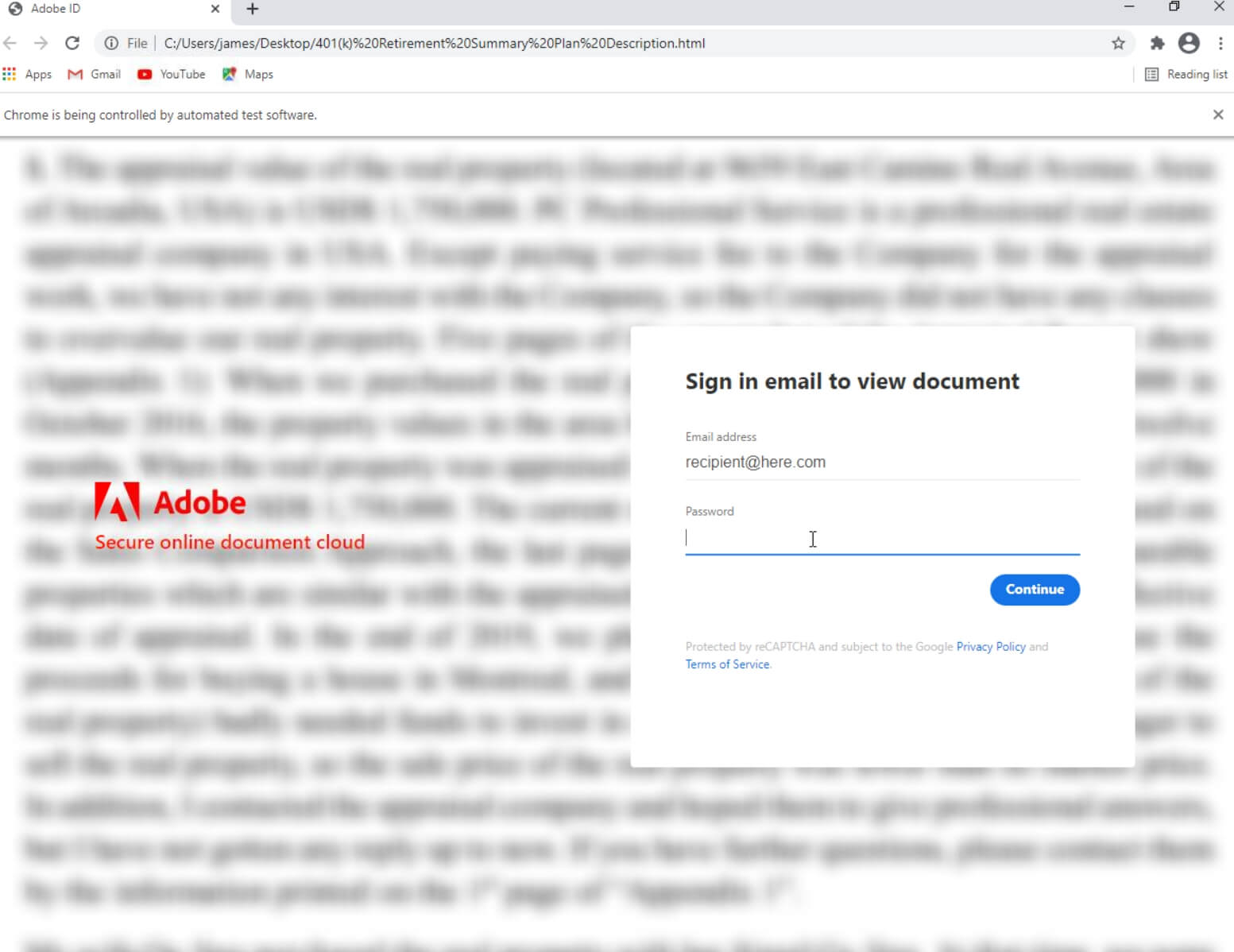
When looking at the html source code we can observe a blob of url encoded javascript. This is used to help obfuscate where the stolen credentials are posted back to the attacker.
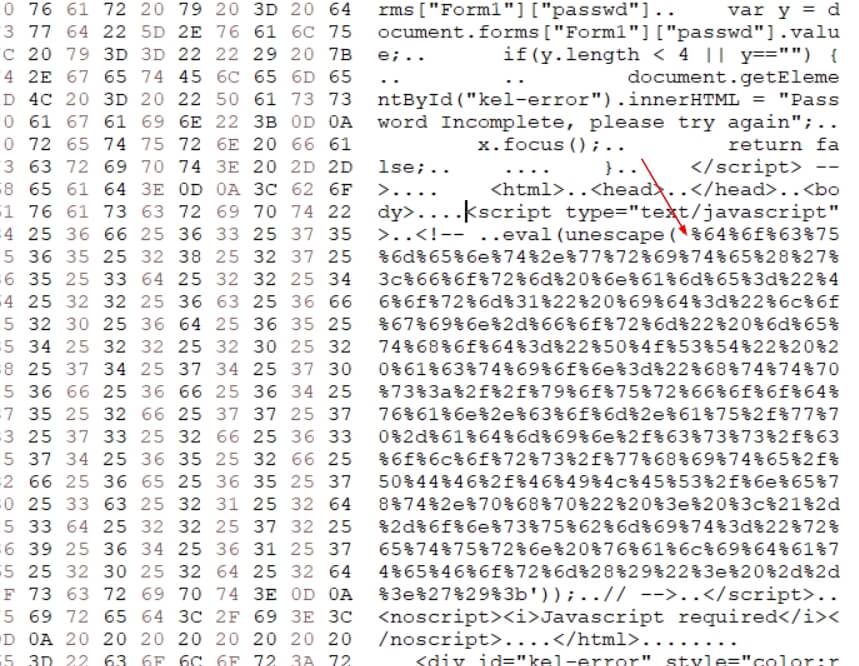
Upon decoding this url encoding, we can see where the attacker is posting the stolen data.
Compromised Victim Data
We navigated to this (compromised) Wordpress site and were able to find it was an open directory. Within was an error_logs.txt file in an atypical location that was recently updated. Inside it we found 50 different logs of victims providing passwords from to this attack with all their info exposed for anyone to view.
The attacker was capturing email address, password, IP address, date/time, city, region, and country. In addition, location data including browser name/user agent/version and machine OS version data, and if the victim was on a mobile device.
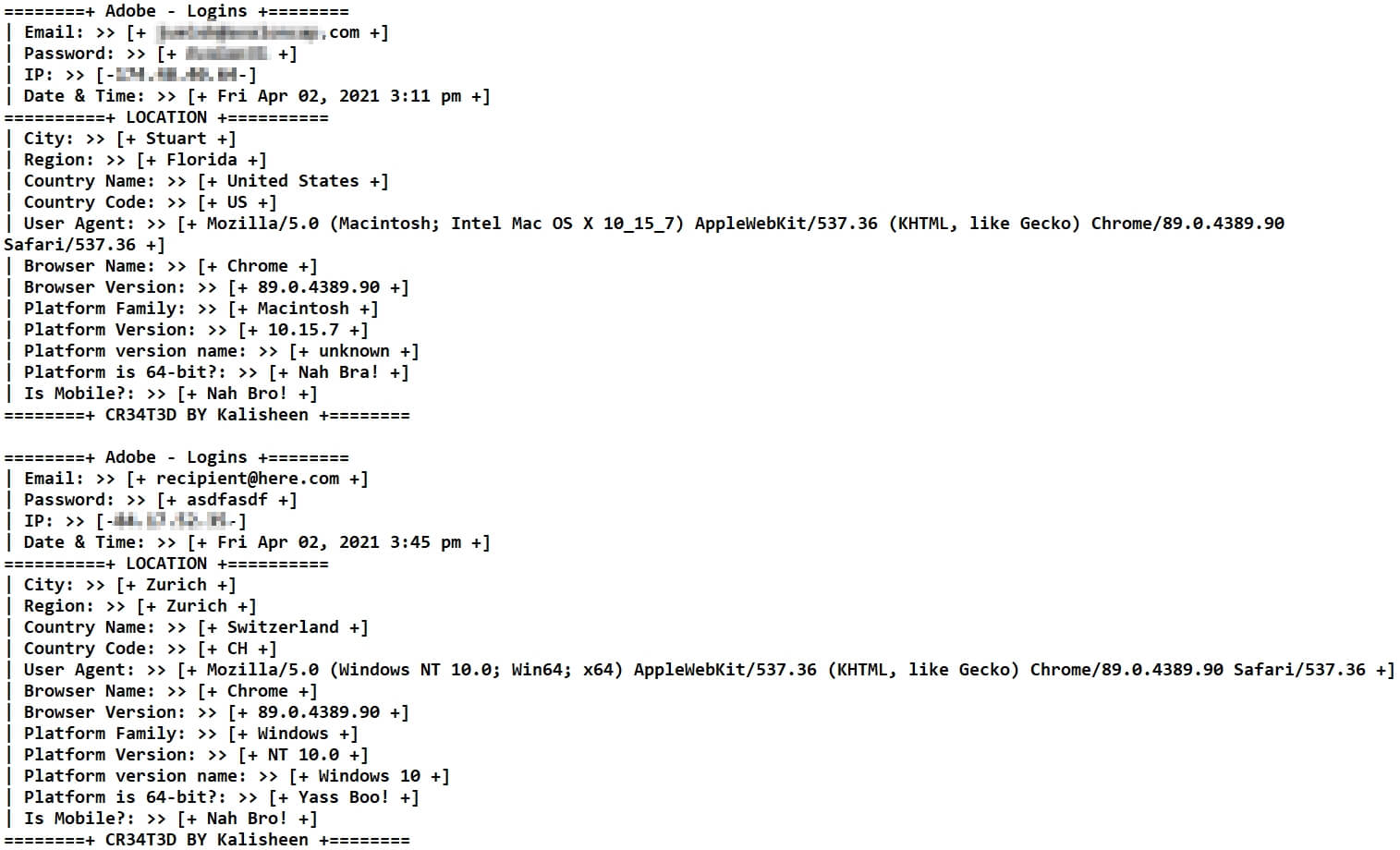
This attack underscores how one successful phish can expose victims to numerous instances of data exposure and thereby create an opportunity for follow-up attacks. In acknowledgment of that threat, organizations need to work to prevent a phish from occurring in the first place.
They can do this by investing in an email security solution that analyzes incoming messages for malware signatures, campaign patterns and other indicators pertaining to known threat behavior. That tool should perform this type of analysis in real time so that it allows legitimate business correspondence to reach its intended destination.
