Attackers Sending Out Phishing Emails from Universities’ Official .EDU Servers
Blog
Attackers Sending Out Phishing Emails from Universities’ Official .EDU Servers
David Bisson

Security researchers observed digital attackers sending out phishing emails from several universities’ official .EDU servers.
A Close Look at Some Samples
Zix | AppRiver spotted and stopped several phishing attack attempts in October 2020 that originated from legitimate universities’ .EDU servers.
In the sample below, malicious actors sent out an attack email impersonating a legitimate university’s IT department.
Using the subject line “Action Needed: Password Expired 2020-10-06,” the email informed the recipient that the password for their Office 365 account was set to expire for that day unless they took action and specified to keep their current password.
Recipients who clicked on the embedded “Keep Same Password” button found themselves redirected to a domain that other security researchers have since flagged as suspicious.
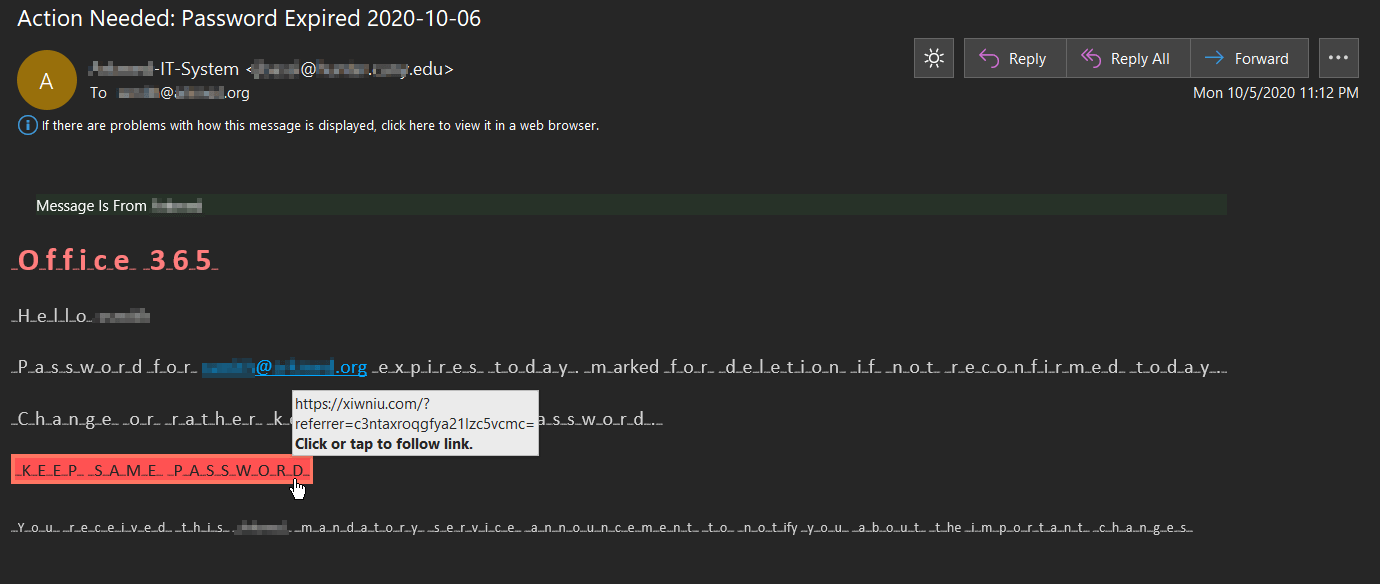
At the time of receipt, that link likely contained a phishing page designed to trick a visitor into attempting to authenticate themselves using their Office 365 credentials.
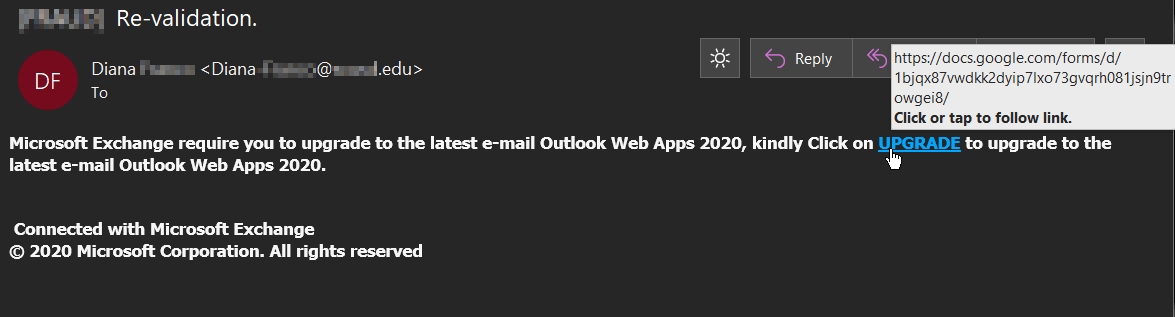
The other sample detected by Zix | AppRiver arrived with the subject line “Re-validation” from someone named “Diana.”
The attack email claimed that Microsoft Exchange required the recipient to upgrade to the “latest e-mail Outlook Web Apps 2020.”
Under that guise, the attack email instructed the recipient to click on an “UPGRADE” link. Compliance with this request redirected the recipient to a file hosted via Google Docs. That page likely hosted an OWA phishing portal.
These email messages dissected above stood out to the Zix | AppRiver team because they managed to successfully bypass sender verification checks such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC).
They also did not just simply spoof .EDU in the friendly-from/display address.
Other Instances of Education Phishing
The attack emails detected by Zix | AppRiver weren’t the first instances in which phishers targeted organizations in the education sector during the 2020-21 academic year.
In October 2020, Malwarebytes revealed that a threat actor known as Silent Librarian had been using spear phishing attacks to target schools and universities.
The security firm found that the threat actor had created domains to impersonate dozens of universities. Those impersonator websites used .ME, .TK and .CF as their top-level domains.
A close look into this threat activity revealed that much of Silent Librarian’s infrastructure was located in Iran at the time of discovery.
It was just a few weeks after Malwarebytes came out with its report when ThreatPost covered a wave of malicious campaigns that had used compromised emails from at least 13 universities.
The malicious actors responsible for that campaign subsequently used attack messages from those compromised email accounts to conduct secondary attacks within the targeted institutions.
Around that same time, DarkReading reported on a research finding that K-12 schools and colleges were more than twice as likely to suffer a business email compromise (BEC) attack than organizations in other sectors.
That same research found that BEC scams accounted for 28% of all spear-phishing attacks launched against educational institutions.
How to Defend Your Education Organization Against Phishing
The attack campaigns described above highlight the need for organizations to defend themselves against a phish. Towards this end, organizations can consider investing in their email security. They can specifically look to invest in an email security solution that scans incoming messages for known malware signatures, campaign patterns, IP addresses and other threat indicators. This solution should perform that type of analysis in real time, thereby allowing legitimate correspondence to reach their intended destination within the organization.
