Malware Distributors Leverage Kaseya Attack
Blog
Malware Distributors Leverage Kaseya Attack
Troy Gill

News of the supply chain style ransomware attack against enterprise technology firm Kaseya has been making huge headlines this week. If you had not already heard, sometime late last week, Kaseya was victim to what appears to be the REvil ransomware gang. This is the same group that has been causing havoc by disrupting fuel supplies and more recently meat distribution. Here, the REvil distributors used a supply chain attack technique via the compromise of a Kaseya software that is used primarily by MSPs and their customers. Kaseya has now confirmed that they believed around 1500 companies have ultimately been impacted from the attack. Those responsible are now demanding $70 million in exchange for a blanket decryption tool.
While many organizations returning from the holiday weekend are scrambling to make sure they are not affected, malware distributors are looking to take advantage and create an opportunity for themselves. Today we have been capturing a malicious email campaign attempting to pose as a security patch related to Kaseya. The malicious emails instruct the recipient to open an attached executable file to fix the Kaseya vulnerability. This attack theme is quite timely as it preys upon the uncertainty and fear surrounding this high-profile incident. Attackers are always eager to capitalize on large scale events that will give them increased attention, especially when that attention may carry some sense of urgency and fear.
The malicious emails began hitting our filters around 11am CST today. They appear to have been somewhat hastily crafted as the subject line was out of context. The sender also directly attached the [EXE] file which is a bright red flag. However, if history is any indication there will likely be new and improved versions yet to come.
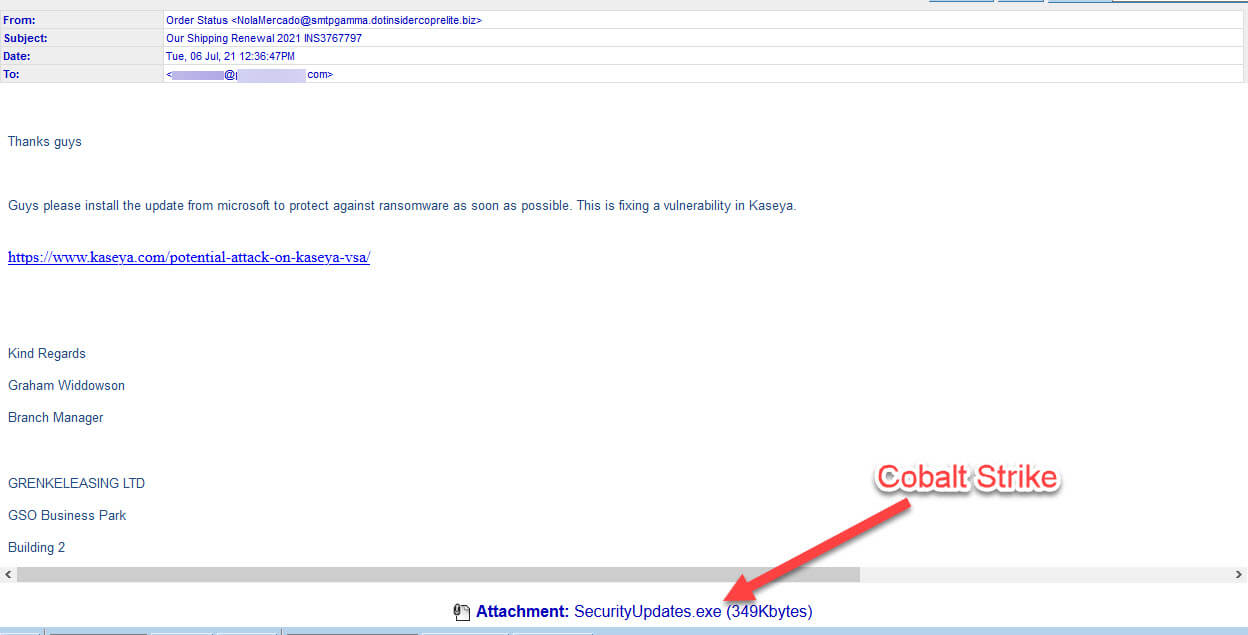
And though these errors exist, the malware attached is just a dangerous as you might expect. The attached [EXE] contained Cobalt Strike. Cobalt Strike is commercially available and often used by pen testers and red teams to help better defend networks. However, as of late the malicious use of Cobalt Strike has been on the rise since threat actors have learned how to weaponize it into an attack tool.
Remember that security advisories/patches are a common theme used in malware and phishing email attacks. Falling victim to this email attack would likely lead to ransomware and/or data theft, the very thing you are trying to avoid.
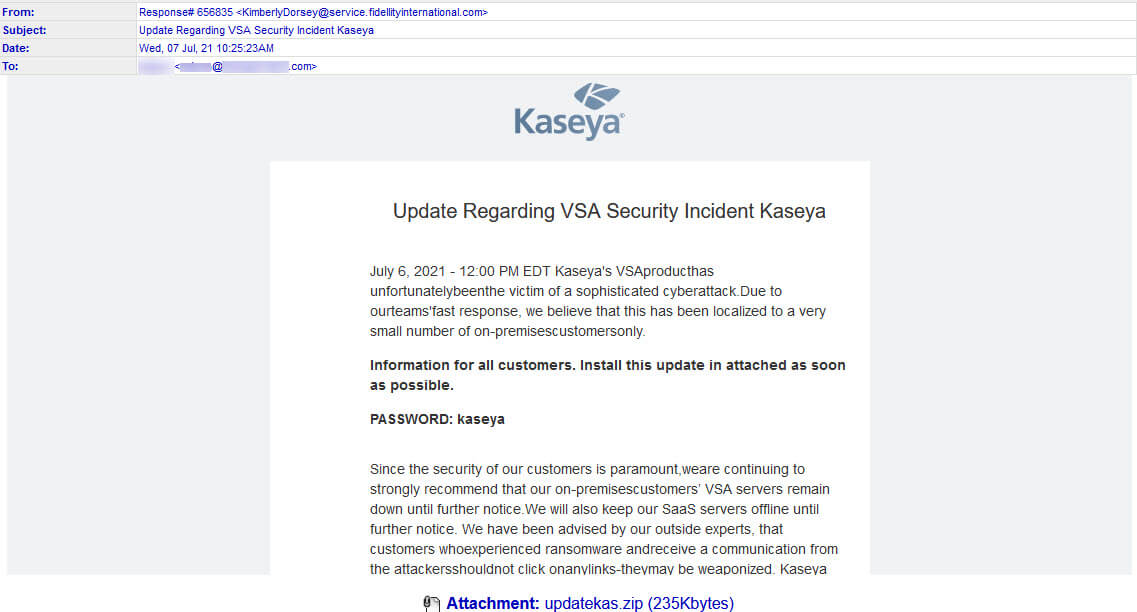
**UPDATE-7-7-2021**
As we suspected we have now spotted additional malware attacks have using the Kaseya security patch theme. The sample below is part of a campaign that began this morning. The password protected archive attached to this email contains an executable which delivers the Dridex Trojan.