Examining Office 365 Phishing Email
Blog
Thought Leadership
Examining Office 365 Phishing Email
Bear Huddleston
Scammers have been sending phishing emails through Office 365 ever since Microsoft launched the product in 2013.
Why phish Office 365's users? The answer is simple: easy access to Microsoft Outlook. Microsoft Outlook is a gold mine of information for malicious actors. They can hijack the mailbox, steal confidential information, and send more phishing emails from the compromised account.
Recently we intercepted the below email and noticed several red flags. While examining the email, we found that two free services were used to create the phishing email. The first was the URL shortener. URL shorteners can be used to redirect users to a website or host images which were used for Office 365 and Microsoft logos in this email. The second was a Dynamic Domain Name System (DDNS). This type of service allows the scammer the option to use a domain instead of IP address. Instead of seeing numbers for the URL, you will see familiar words, like Microsoft, in the URL to make to seem authentic.
To get a better understanding of the process and what to do if your credentials are phished, let's examine one of these phishing emails including the payload, and phishing website pretending to be Office 365.
The email:
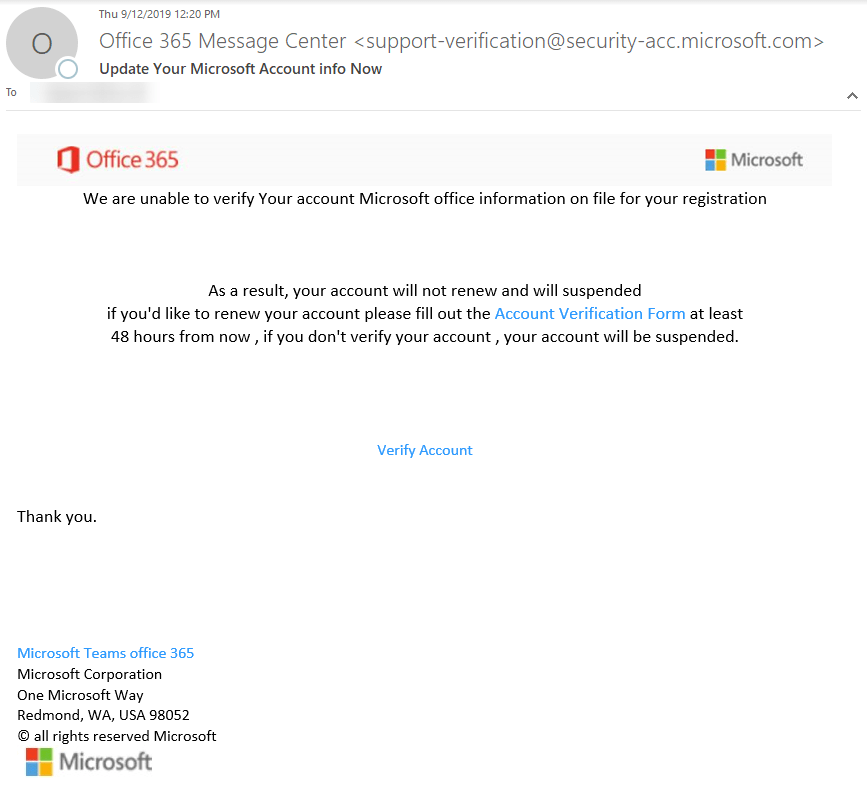
At first glance, the email seemed off-putting. The FROM ADDRESS had an unfamiliar subdomain. Though Microsoft uses many subdomains, @security-acc subdomain is not one of them. The images were blurry and not coming from an original source. Instead, the images were coming from a URL shortener.
Red flags spotted from the email
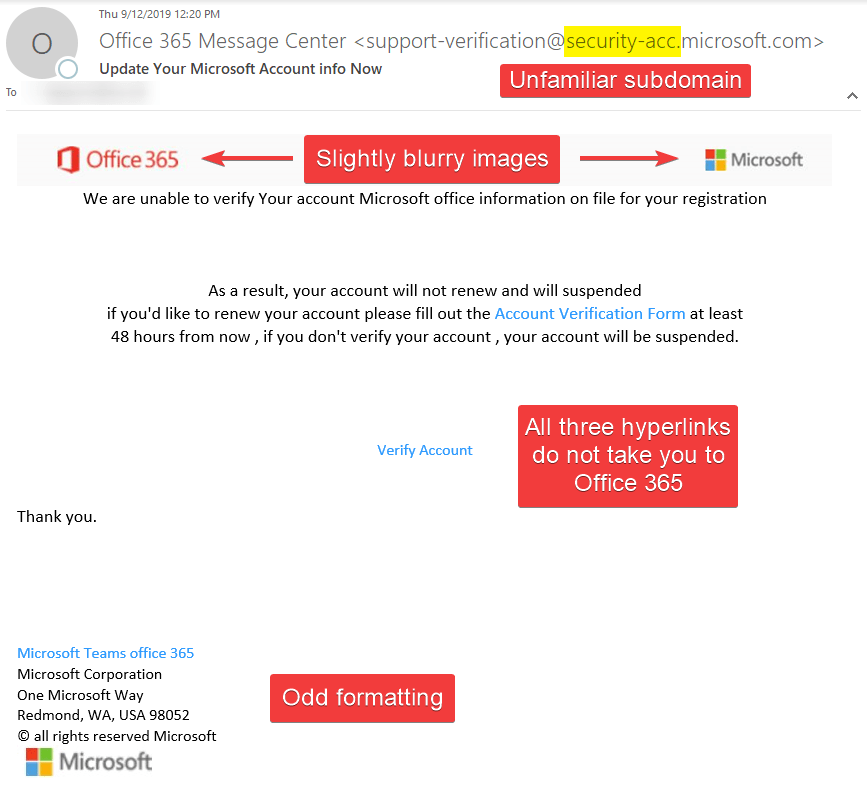
All three hyperlinks directed to one URL. That URL was not Office 365 or its affiliates.
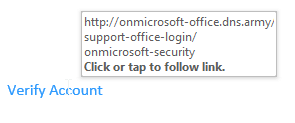

Upon clicking on the link, it would take you this page below.
Phishing website page
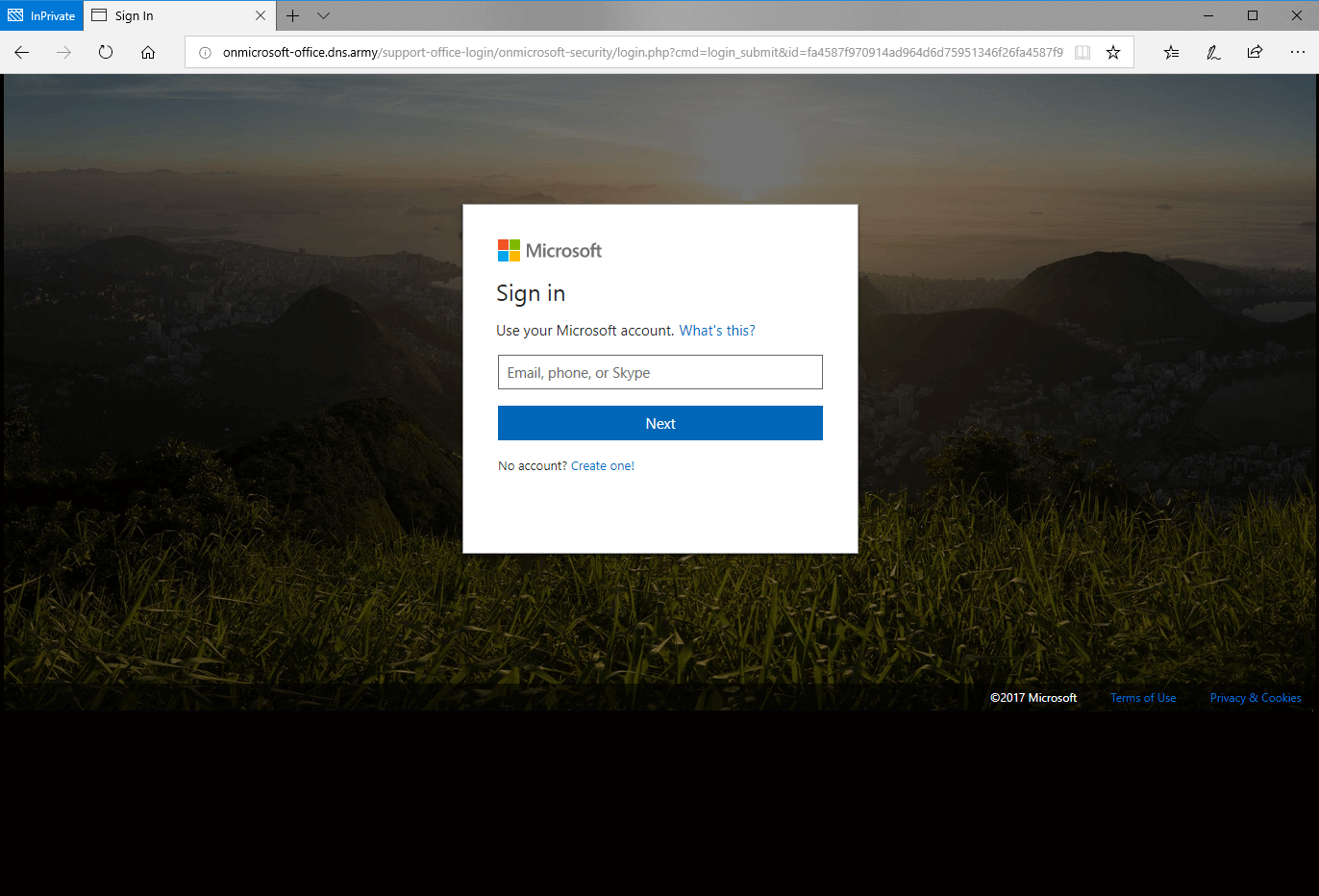
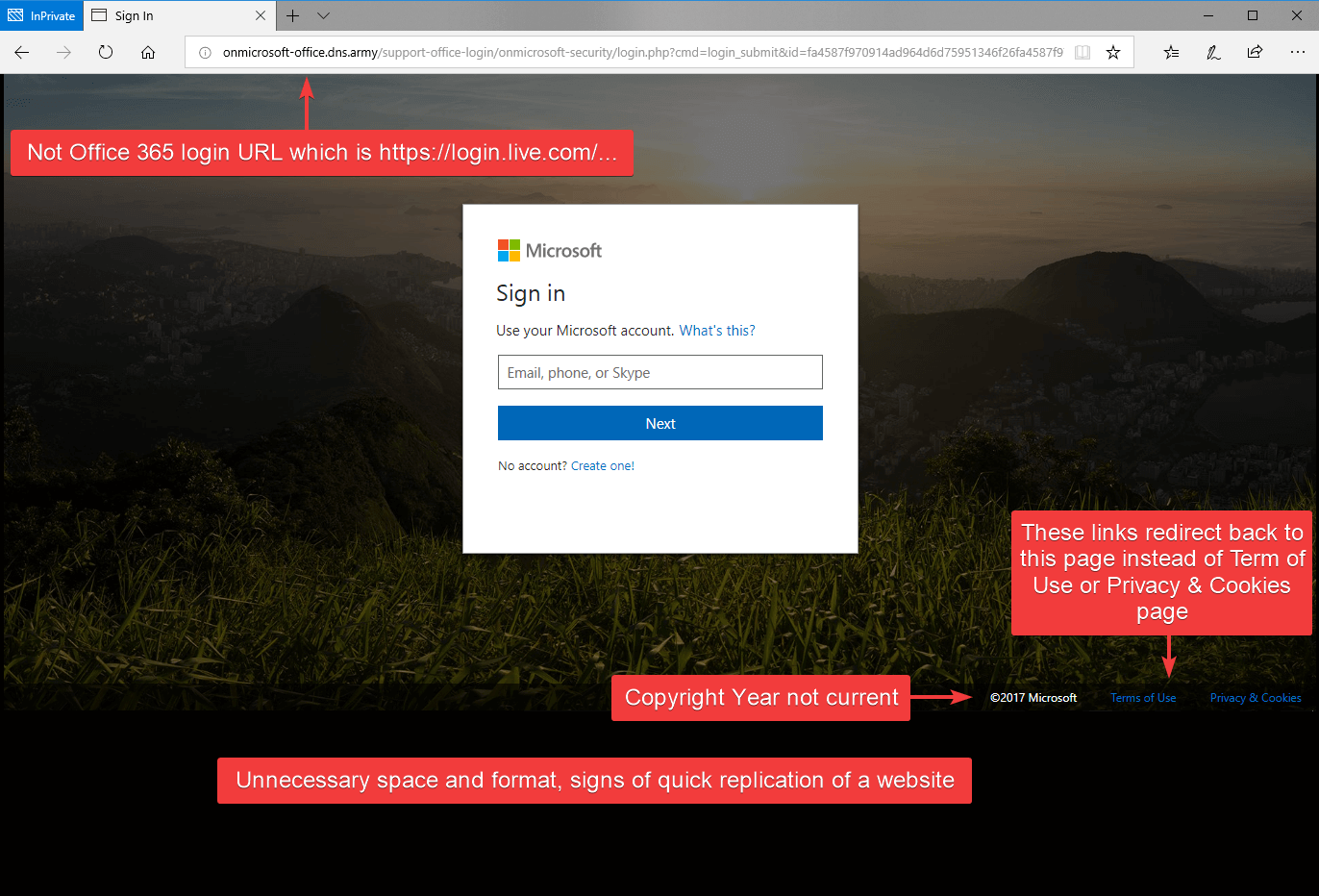
If this is your first time seeing this page, it may appear as a legit login page for Office 365, but look closer, there are several red flags. The URL in the address bar is not a legit Office 365 URL, and the copyright year was not current. All the links on this page redirect back to the page below instead of taking you to the proper page such as Terms of Use or Privacy & Cookies. Finally, the page formatting was not adjusting to the size of the browser; common for quick phish websites.
Red flags on the phishing website
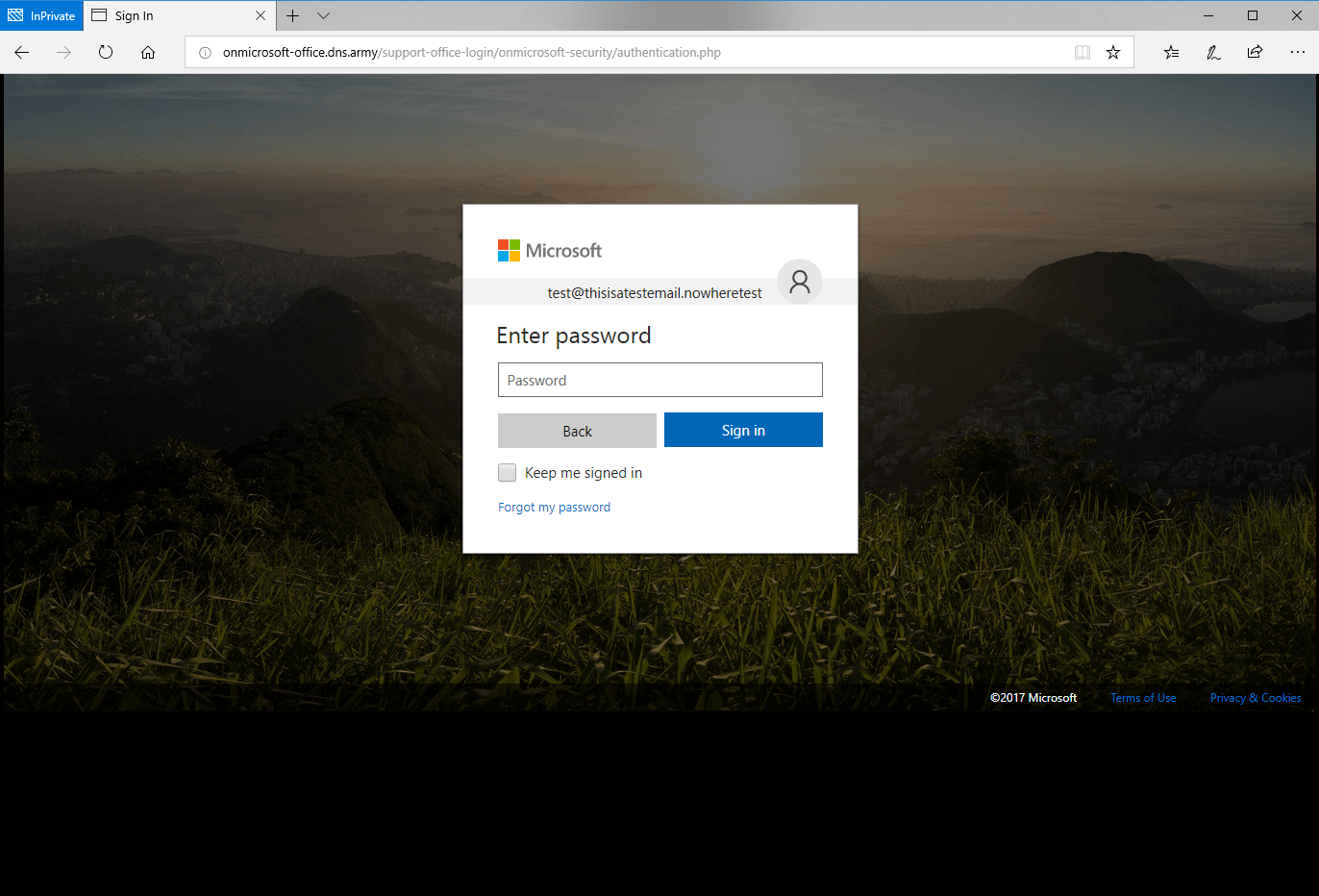
After entering an username, it continues to the password page with same red flags as before.
Password page, can you spot the red flags?
After submitting a password, it redirected you to Microsoft Privacy page while the username and password information was sent to the phisher.
Legit Microsoft Privacy Page
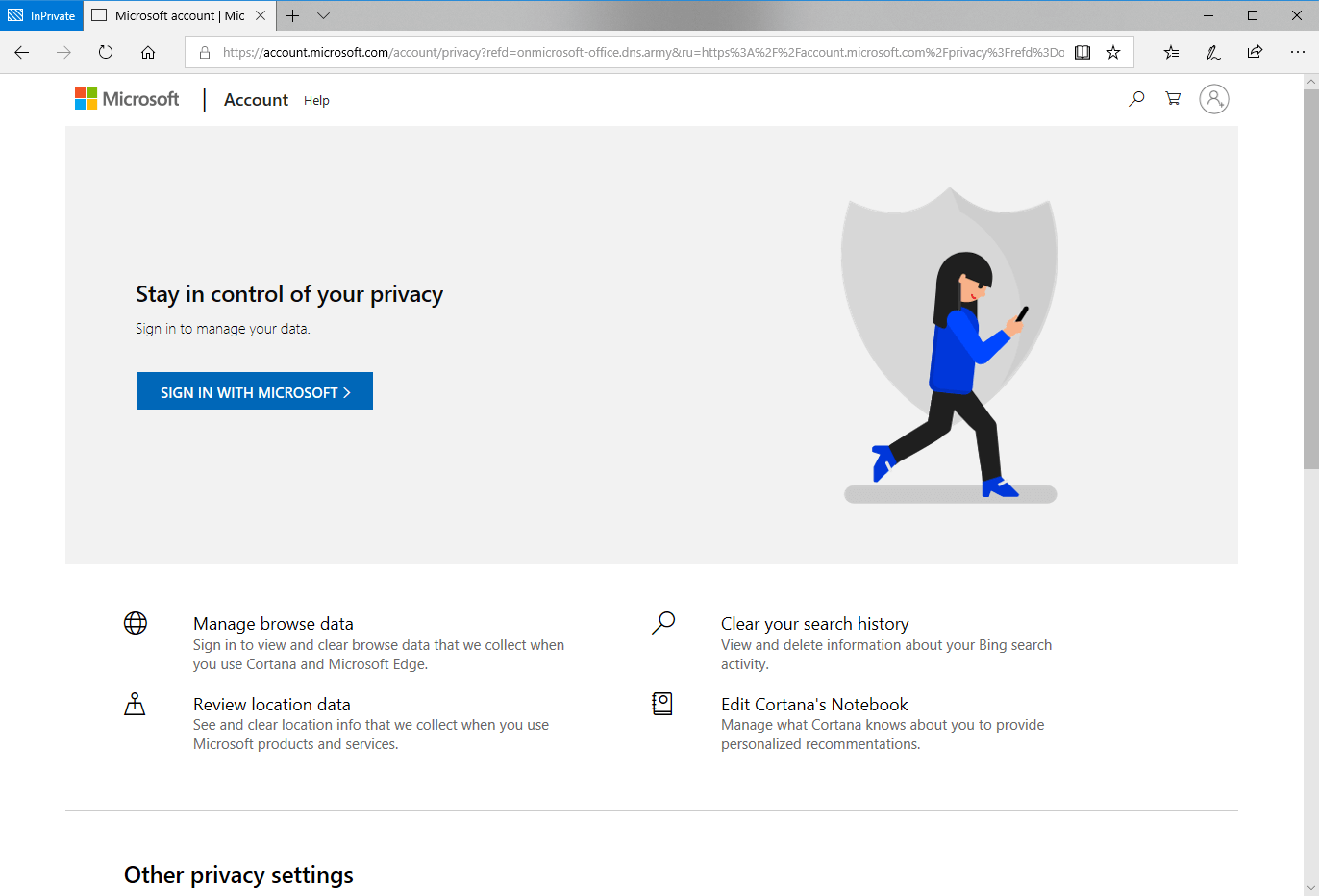
If you ever submit your credentials to a login page and it doesn't send you to the location you were expecting, most likely you were phished. In this situation, the best course of action is to immediately reset your password at the official Office 365 page (see below) and contact your IT department. I highly recommend enabling multifactor authentication (MFA) on your Office 365 account. This will create an extra safeguard in case your credentials get compromised. It will need another form of authentication after the login page such as a code from texts or emails.
Official page of Office 365 login for comparison
Tips on how to spot these phishing emails:
Be wary of emails from that have blurred images and odd formatting. Especially, emails asking you to verify your account.Be caution of impersonal or generic greetings/salutations; e.g. "Dear Customer" or "Hello your@email.address." Legitimate businesses use your first and/or last name.Always verify the links you're about to click on by hovering your mouse over the link. Scammers often use this method to phish for your information and/or infect your computer with viruses/malware.Report emails that contain unknown or bizarre attachments. Emails are the most common way in delivering malicious links and files.Be wary of emails conveying a sense of urgency. Always confirm by going through official channels; not by replying or visiting the URL in the email you received.
If you are an AppRiver customer, forward any suspicious emails to spam@appriver.com and our 24/7 trained cybersecurity specialists will review the email for you.
If you're not an AppRiver customer, contact us for a free trial of our Advanced Email Security
