Bash Bots Waste No Time
Blog
Thought Leadership
Bash Bots Waste No Time
Fred Touchette
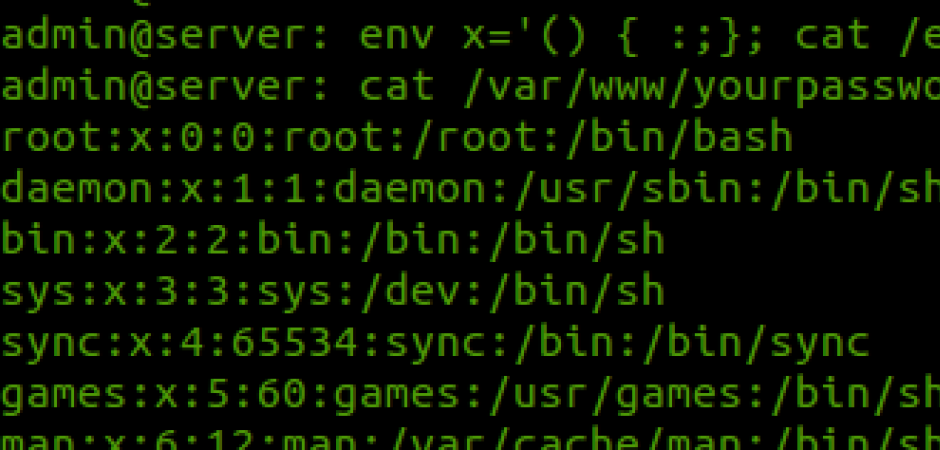
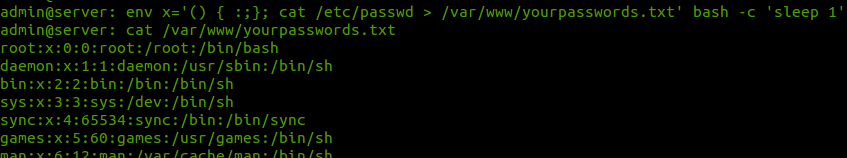 It took less than one day after the news was publically released about a major flaw in the bash command line interpreter before a botnet leveraging this flaw, referred to as ShellShock, has been spotted in the wild. This vulnerability is being compared to Heartbleed, the OpenSSL flaw that made headlines earlier this year, in terms of severity. Unfortunately researchers agree that this actually has the potential to eclipse Heartbleed in that arena. The reason being is that where Heartbleed was able to easily steal data from unsuspecting victims, this new bash vulnerability allows an attacker to actually gain access and control of its victim's machines. Another concerning factor of this new exploit is its potential targets. Bash runs in both Linux and Mac's OS X operating systems, a rarely targeted group which may be caught with their guard down. Every Mac we have tested this on so far has been vulnerable to this exploit, where we achieved varying results with Linux environments due to particular Linux flavors and bash versions that were installed. Bash is the most widely used shell on Linux based systems and is also the default shell in Mac OS X Panther which is (version 10.3) and later. This vulnerability is present in every bash version up to 4.3, which is potentially a large swatch of users. It is being stated however that the likely prime target of these new attacks will be Apache web servers that use standard CGI implementation.
It took less than one day after the news was publically released about a major flaw in the bash command line interpreter before a botnet leveraging this flaw, referred to as ShellShock, has been spotted in the wild. This vulnerability is being compared to Heartbleed, the OpenSSL flaw that made headlines earlier this year, in terms of severity. Unfortunately researchers agree that this actually has the potential to eclipse Heartbleed in that arena. The reason being is that where Heartbleed was able to easily steal data from unsuspecting victims, this new bash vulnerability allows an attacker to actually gain access and control of its victim's machines. Another concerning factor of this new exploit is its potential targets. Bash runs in both Linux and Mac's OS X operating systems, a rarely targeted group which may be caught with their guard down. Every Mac we have tested this on so far has been vulnerable to this exploit, where we achieved varying results with Linux environments due to particular Linux flavors and bash versions that were installed. Bash is the most widely used shell on Linux based systems and is also the default shell in Mac OS X Panther which is (version 10.3) and later. This vulnerability is present in every bash version up to 4.3, which is potentially a large swatch of users. It is being stated however that the likely prime target of these new attacks will be Apache web servers that use standard CGI implementation.
The botnet, known as Wopbot, has already gone to work. It has been busy running distributed denial of service attacks against Akamai and other targets over night. It has also been scanning the entire IP address space of the US Department of Defense apparently searching for open Telnet ports which commonly would be brute forced in order to gain access. This is quick work by cyber attackers which is exactly what those at risk do not want with such a publically available flaw. Currently the Linux community is rushing to create and push out patches for ShellShock while others are arguing whether or not to simply remove the point of vulnerability altogether. It is unclear what Apple's stance is on this or when they may have a fix available. Hopefully they will move quickly as well or all of my friends who "never get viruses" just may be in trouble.
It is recommended that those who may be susceptible to this vulnerability watch closely for patches or hotfixes and apply them as soon as possible.
