Spy MAX Android RAT Targets Luxury Business Sector
Blog
Thought Leadership
Spy MAX Android RAT Targets Luxury Business Sector
David Pickett

On June 4, 2019, AppRiver's Advanced Email Security filter began to quarantine low volume waves of highly targeted attacks directed toward businesses who operate in the luxury services sector.
Examples of these businesses include yacht brokers, executive housekeeping and staffing providers, and some that offer various services to high-net-worth clients.
The malicious attachment included with the message was an Android package file (.apk extension). Upon analyzing it, we found it was Spy MAX v1.0, a Remote Access Trojan (RAT).
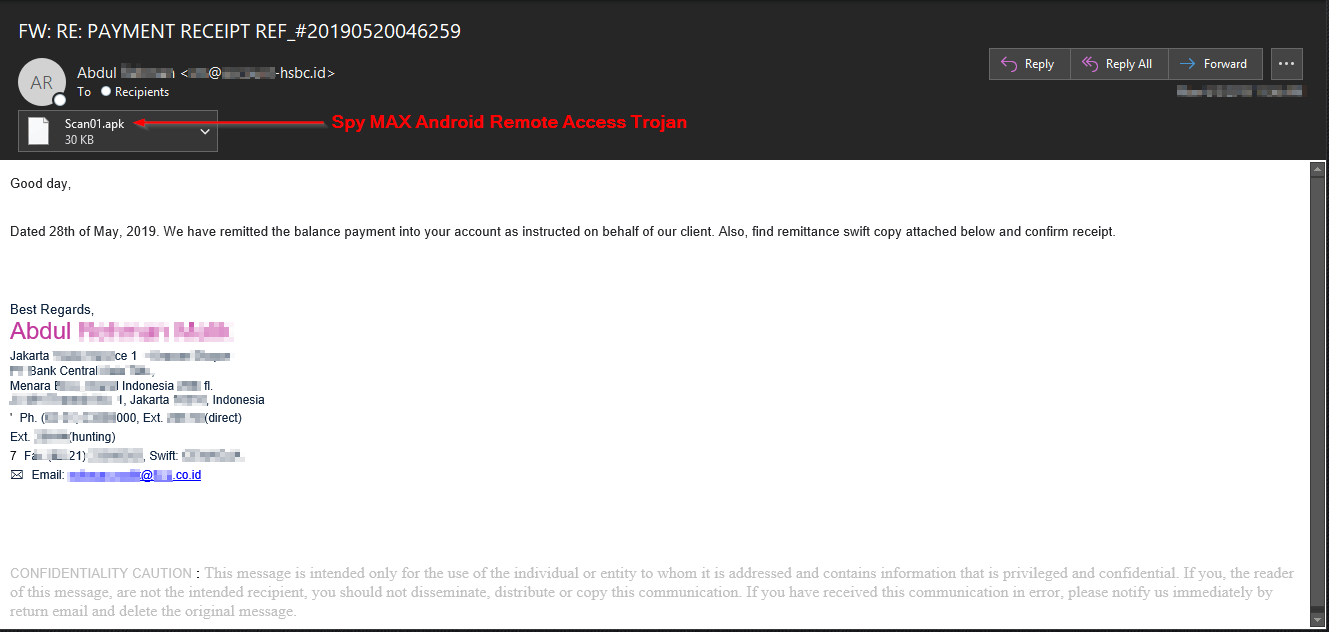
Message Example
The malicious emails sent by this attacker purports to be a remittance into the recipient's bank account. The Society for Worldwide Interbank Financial Telecommunications (SWIFT) system is legitimately used by banks and financial institutions to securely send and receive information such as international money transfers. As such, it is a long-time favorite attack ruse by malicious actors attempting to dupe unsuspecting email recipients.
Most likely these attackers were using the Spy MAX RAT to conduct reconnaissance and steal personal information. This would allow them to conduct follow-up attacks towards very specific wealthy targets.
Spy MAX v1.0 Android Remote Access Trojan
Spy MAX entered the remote access trojan market on various malware, hacking, and dark web forums in March 2019. Cracked versions have been circulating so attacker usage will continue to increase over time. It is currently marketed as the best Android hacking tool on the market and better than the popular SpyNote Android RAT. Spy MAX is compatible with Android systems 6.0 (Marshmallow), 7.0 (Nougat), 8.0 (Oreo), & 9.0 (Pie).
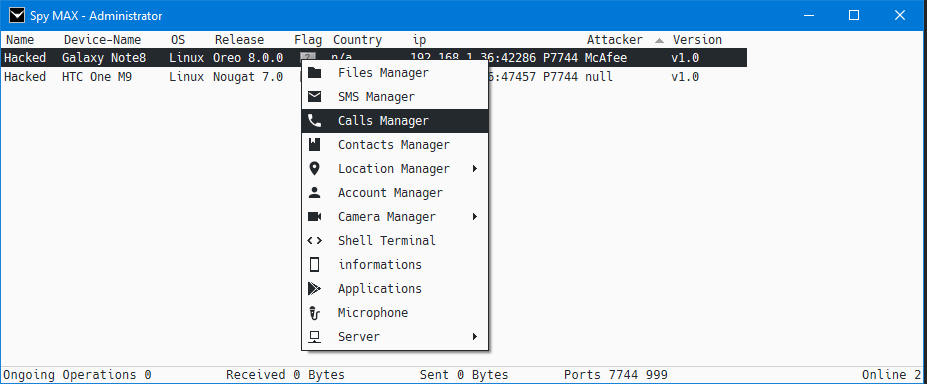
Capabilities of the Spy MAX RAT are very comprehensive, offering a full suite of options for attackers. It includes the ability to monitor SMS (text) messages, access the microphone, record audio, access the camera, contacts, calls, files, GPS data, load applications, utilize proxies, persist after a reboot, and open a shell to the phone.
If GPS is turned on, attackers can click on the location and it will open a map in a web browser pinpointing the phone. Authors have also recently updated Spy Max to v2.0, that version appears to add clipboard features and a key-logger.
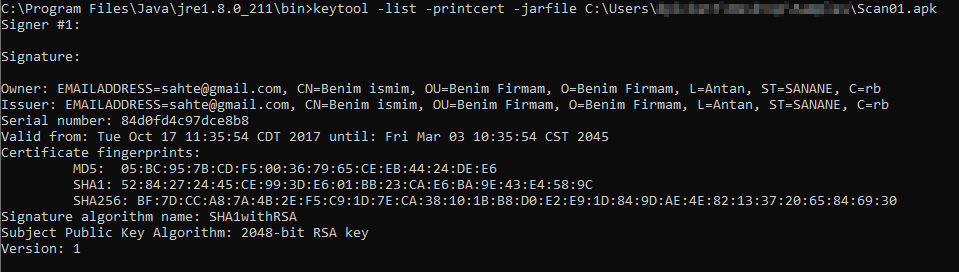
The example we analyzed used an RSA certificate signed with an email address of sahte@gmail[.]com, common name of Benim ismim, organizational name of Benim Firmam, and used an obsolete Bolivia/Botswana country code.
We were able to find additional malicious .apk files located in public sandboxes that also used this same certificate with fraudulent information. Some examples dated back to December 2018, using a different RAT - SpyNote.
We recommend never installing Android package files not located in the Google Play store. Even there, malicious apps are located and removed once discovered. However, it is much safer than installing .apk files from untrusted sources.
These files should never be installed from any unsolicited email. While many businesses utilize and distribute customized apps, verify out of band (not via email) the sender meant to send it and it is a legitimate message before installing.
AppRiver Protection
There is no shortage of spam, malware, phishing, or nefarious websites AppRiver’s staff and systems continuously protect and defend against. Malicious actors work around the clock, therefore, we at AppRiver work even harder to stay one step ahead. Our team is here 24/7, 365 days a year protecting and supporting clients and partners from security threats.
Contact us today for a free trial of our Advanced Email Security
