Keylogger Sending Plain Text Emails
Blog
Thought Leadership
Keylogger Sending Plain Text Emails
Jonathan French

I ran across an interesting piece of keylogging malware that uses a pre-built keylogger named Knight Logger. This particular keylogger is openly available for purchase online by its author. Of course it's labeled for educational purposes only and says you must have the computer owner's permission to install the keylogger. It also boasts its AV detection rate with 0/39 AV engine detections, the ability to recover passwords, and provide "screenshoots" of the computer.
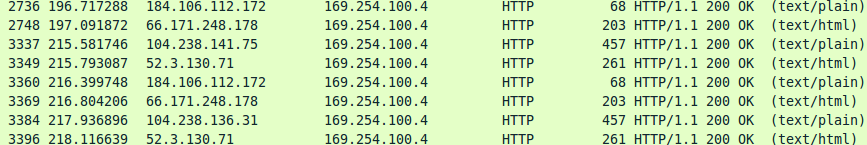
The original message was a 903kb rar file with the exe inside claiming to be from HSBC. This is a rather large file size for malware given our average size is probably closer to 60k for most malware. When uncompressed it comes in at around 1.2Mb. Upon execution, the malware gets it's external IP address from 4 different external websites. These websites are pretty popular with malware since they can make a simple external HTTP request and get their external IP back in plain text. This process is repeated it looks like every time the malware sends out data, most likely to make sure the IP stays up to date for anyone roaming.
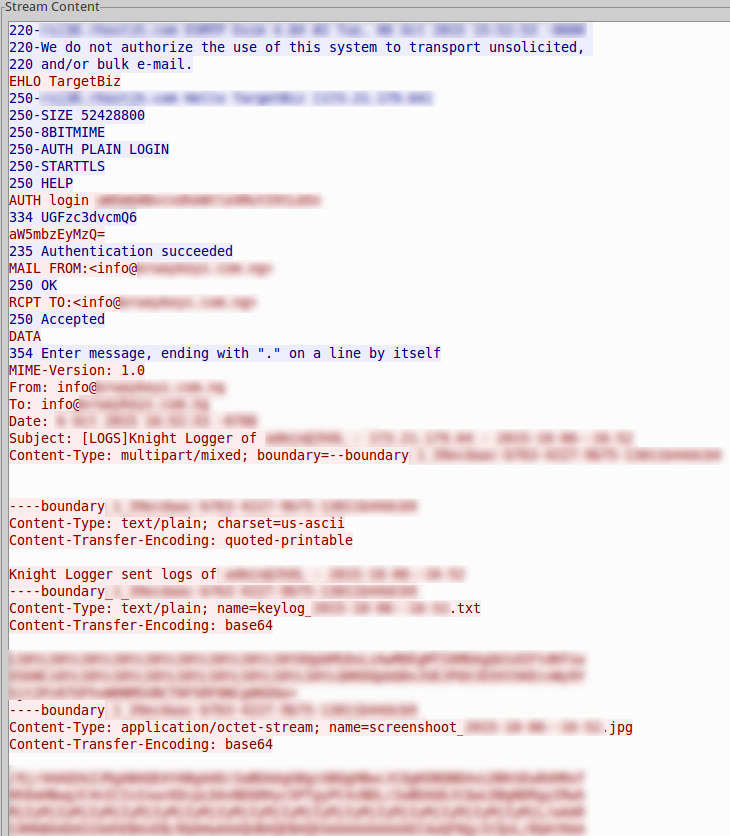
For actually sending out data, the malware sent a plain text email every couple of minutes. This email contained a plain text file of keylogging and a full jpg screenshot of what was on the screen at the time.
So this is where things get sort of interesting and lazy on the attackers part. During the exfiltration of your data, it logs in to the remote SMTP server. It logs in using base64 encoded username and password. The password I do feel like sharing because it was pretty bad. You can see the bad guys email is info@<redacted>. His password was info1234. At least there's a login I guess, only slightly better than an open relay. And once logged in as I mentioned, it then proceeds to send the data in plain text (base64 encoded attachments). I wanted to see if the mail server was still up and running a little bit after I had run the malware. A lot of the time within an hour or so, we see server taken down when they are involved in these types of schemes. So I grabbed the login info and converted it and tried to connect to the server. The server was indeed still up and the authentication was a success.
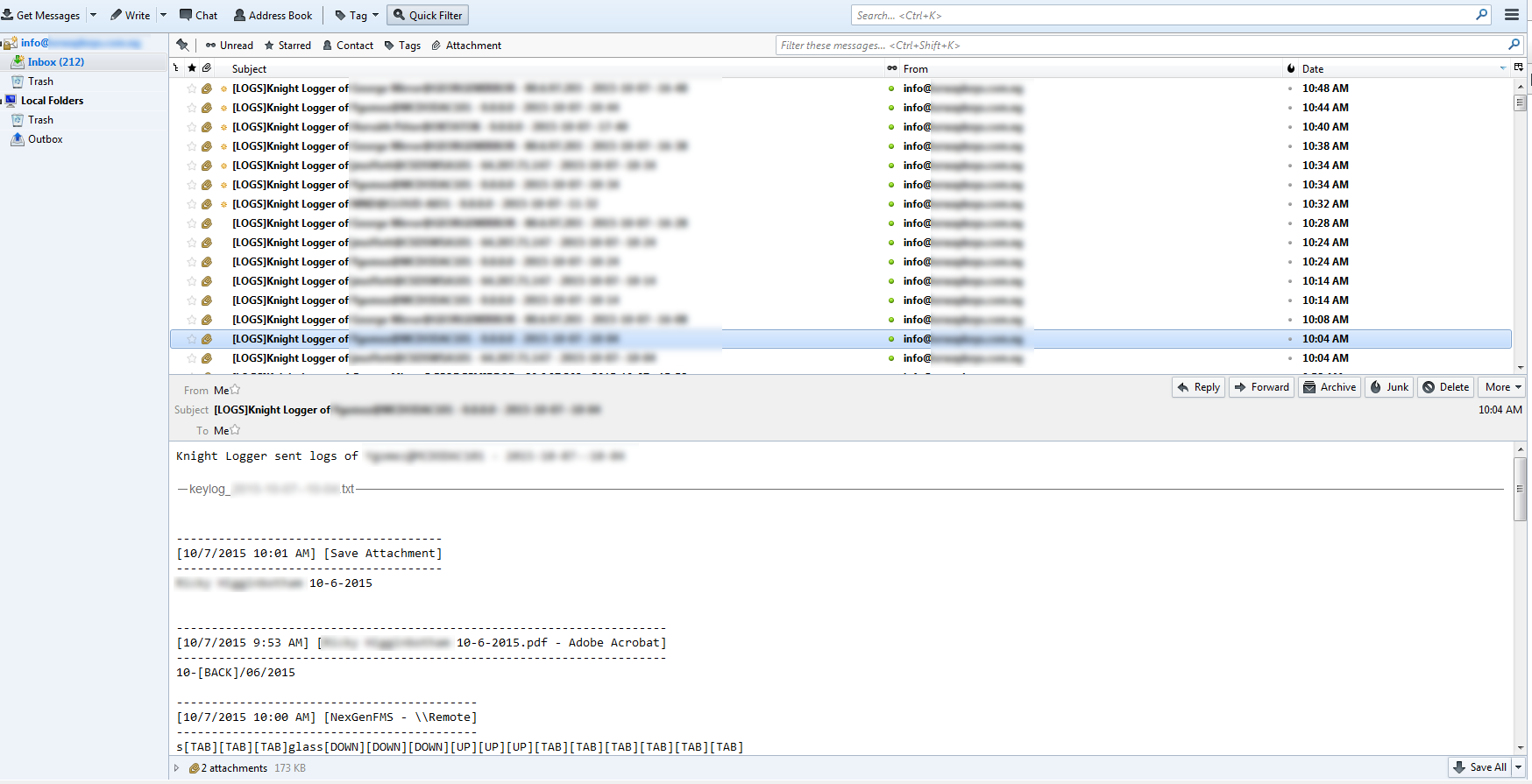
So I noticed on the SMTP transaction, the login address, FROM, and TO were all the same email address. On a hunch, I fired up Thunderbitrd and dropped in the username and password expecting nothing really. But oh no, not this time. The credentials they are using to log in to the mail server also work for a POP connection to the actual destination mailbox the malware sends to. Thunderbird proceeded to download the messages from victim computers with the keylogged data and screenshots (or as Knight Logger says "screenshoots"). This was something I didn't expect to actually work and makes me think this whole thing was thrown together by someone with not too much thought put in to it. They grabbed an available keylogger online and created a wrapper around it to just hopefully get it running on the victims computer.
Data is king when it comes to the dark belly of the internet these days. With a successful attack like this using a keylogger, who knows how long these users personal information would be exposed. Having up to data AV software and network protection can help prevent these types of attacks playing out. Or in the case of software built to evade AV, it can only evade for so long. Having the tools and pieces in place to monitor computers and traffic can help detect what might have otherwise gone unnoticed.