AKO Ransomware Targeting Networks via Email
Blog
Thought Leadership
AKO Ransomware Targeting Networks via Email
David Pickett

AKO Ransomware Targets Networks via Email
The AppRiver advanced email security filter has been catching low volumes of targeted AKO ransomware-laced emails. On Monday, January 13, we captured 247 of these messages destined for customers. While seen in low volumes, this ransomware variant is particularly troublesome to network administrators.
Bleeping Computer forum reports have shown it capable of spreading laterally using ping scans and searching for network shares throughout the environment. It encrypts not only Windows 10 desktops, but also Windows SBS 2011 servers using the typical ransomware behavior of deleting, disabling, or encrypting native shadow files and backup recovery options first. Bleeping Computer also reports the popular ID-Ransomware site has seen an uptick of victims this week.
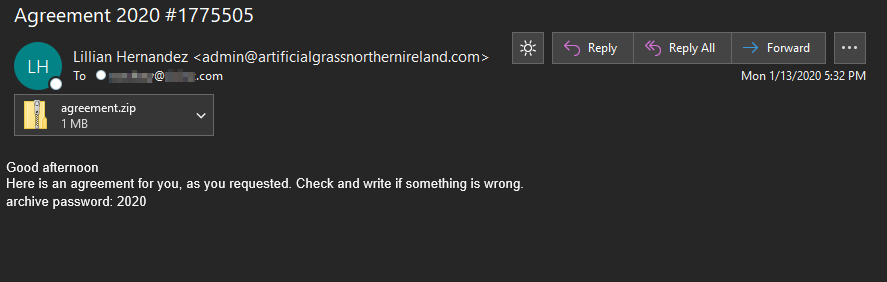
The messages contain a ruse purporting to be “an agreement, as you requested.” Attached is an encrypted zip file with a password in the body of the email. This technique should always be a red flag to users, encrypting a file and including the password inside the same message is not a good security practice and commonly utilized by malicious actors attempting to bypass email virus scans.
The Payload
One the attachment is downloaded and decrypted, inside “appears” to be a screensaver (.scr) file. This should be another red flag for users. While not always the case, this attachment doesn’t match the message ruse.
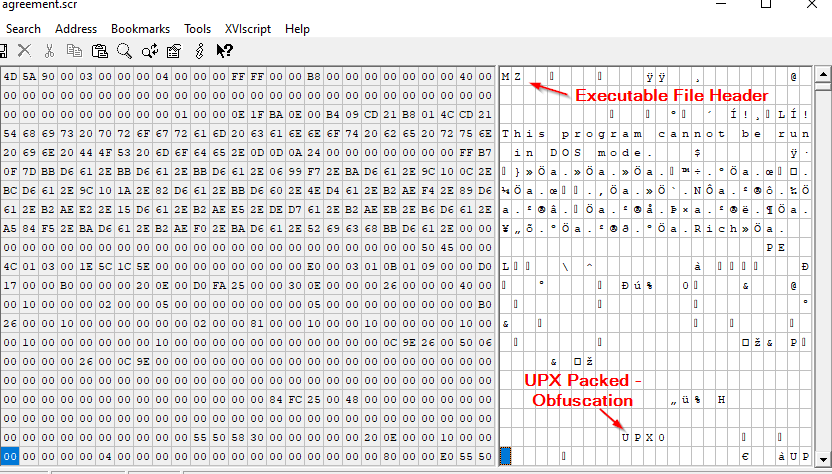
Screensaver files are commonly utilized by attackers and among the globally blocked extensions for all our filter customers by default. However, we can see this file is truly an executable file (.exe) when taking a quick look in a hex editor. The file also utilizes the open-source UPX Packer (legacy v3.08), over the years we’ve commonly seen it utilized for malware obfuscation attempts.
Post-Encryption
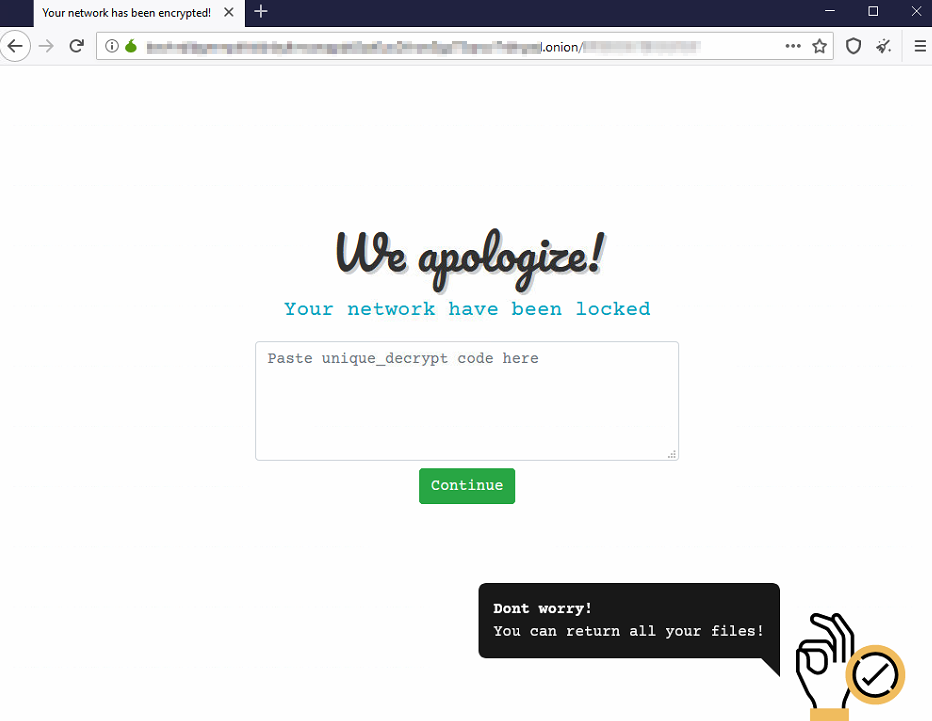
After the ransomware encrypts a victim’s files, a random extension will be added onto the file name. A file named ako-readme.txt will also be placed onto the locked machines desktop with instructions on how to proceed. Some examples instruct the victim to contact the attackers email address, while others demand bitcoin. The ransom demand examples we’ve seen so far range between $3000-$3800 in Bitcoin (btc) with the ransom amount doubling after 2 days.
Indicators of Compromise:
Main object - "agreement.scr (.exe)"
sha256 c817a576455e0534b2500e57ec5c473febe6ca3c0211fe5a1cd96a619508d348
sha1 6127f590e040902e820fbcebc2387fa9450e7ed2
md5 fd5ce9e0ebad9cca91399311b012063b
89.191.227.53 – Email Sending IP
85.173.126.136 – Reported Login from Attackers
Contact us today for a free trial of our Advanced Email Security
