TurboTax Users Targeted on Android Devices
Blog
Thought Leadership
TurboTax Users Targeted on Android Devices
Fred Touchette

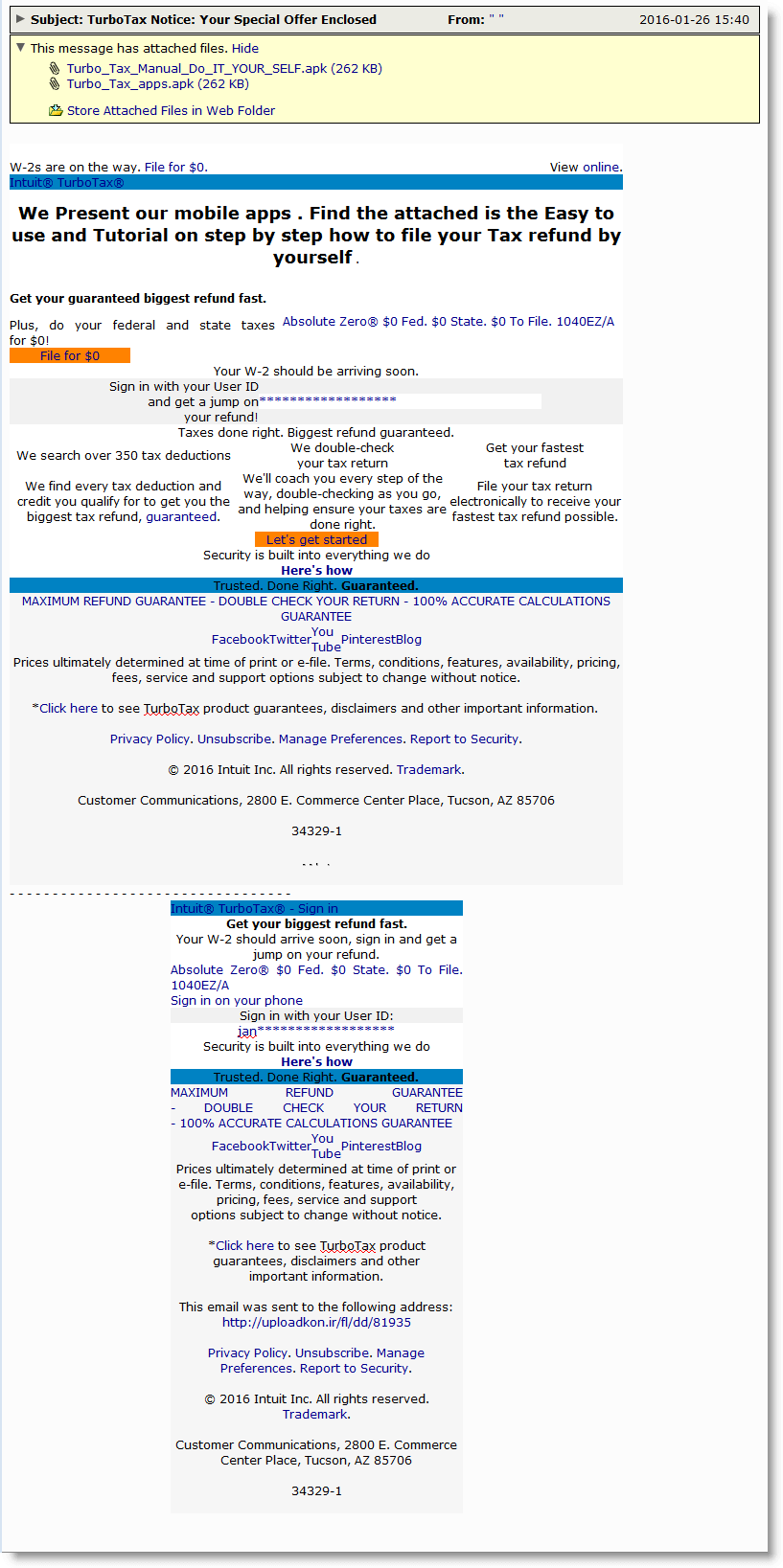
 Whilst pursuing our filters this morning I noticed a handful of emails purporting to be from TurboTax promoting their easy to use tax filing mobile apps. These emails also included two attachments labeled Turbo_Tax_apps.apk and Turbo_Tax_Manual_Do_IT_YOUR_SELF.apk, the latter pretending to be a tutorial on how to file your own taxes using their kindhearted mobile app, and the first being the app itself. Unfortunately, this isn't the case. Both of these are in fact the same file. These are .apk files or Android application file packages, designed to be executed and installed on Android devices. Although they pretend to be handy tax filing software, they are instead invasive pieces of spyware that monitor nearly every facet of the target device's functionality.
Whilst pursuing our filters this morning I noticed a handful of emails purporting to be from TurboTax promoting their easy to use tax filing mobile apps. These emails also included two attachments labeled Turbo_Tax_apps.apk and Turbo_Tax_Manual_Do_IT_YOUR_SELF.apk, the latter pretending to be a tutorial on how to file your own taxes using their kindhearted mobile app, and the first being the app itself. Unfortunately, this isn't the case. Both of these are in fact the same file. These are .apk files or Android application file packages, designed to be executed and installed on Android devices. Although they pretend to be handy tax filing software, they are instead invasive pieces of spyware that monitor nearly every facet of the target device's functionality.
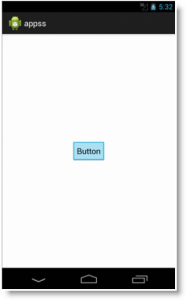
Once installed, the user is shown a single button labeled "Button", not the most creative interface for tax software, but underneath the surface, the application is granting its attacker access to the phone's location via GPS, Wi-Fi state (ability to toggle it on or off), camera, internet, gives it the ability to make calls, send texts, access to the contact list, file storage, etc. Within the source code, the software communicates directly to hardcoded URL's at a very telling domain by the name of droidjack[.]net.
The email itself has a couple of hyperlinks that lead to a different domain, specifically uploadkon[.]ir/fl/dd/81935. This site was down at the time of analysis, but I can assume that this was an alternate route for infection if the user received this email on a PC and was not viewing it on the device itself, thereby unable to install the malicious attachments. Another curious thing about the emails were that they all came from the same place instead of the usual botnet delivered campaign. All of the samples that I found came from 69.63.218.198, which is a mail portal, which makes sense, but the reverse dns entry shows the domain mail.kantora[.]com. The kantora[.]com domain itself, if followed, redirects to yet another domain - mdavidovich[.]com which is a Russian blog site hosted by Wordpress. Wordpress has had a number of vulnerabilities in the past, so it is very likely that this seemingly innocent blog had been compromised and associated with these attacks, though the link between the two sites, save for the redirect, is unclear. Another interesting note in regards to the email is that appears to be dated Jan 26, even though the attacks hit our filters today. This likely the date when the template was created, when an initial test run occurred, or simply spoofed to add a feeling of urgency with the recipient.
We have you covered against these attacks, but keep one eye open when it comes to attacks such as these, especially around tax time, this is a very common theme used to trick people into installing malware. Also, never install an app you received from email. Apps should ONLY be downloaded and installed from the app store approved for the device, for Android users, that is the GooglePlay Store, for iOS (Apple) devices that is the iTunes Store, and Windows phone users should only use the Microsoft Store.