Attackers Leverage Stolen Email Credentials In Malware Attacks
Blog
Thought Leadership
Attackers Leverage Stolen Email Credentials In Malware Attacks
Troy Gill

Throughout 2017 we observed a major increase in phishing efforts, reaching peak levels over the summer, and this trend has continued to intensify in 2018. Much of this effort was expertly tailored to gather users’ login credentials to their preferred email provider. Ultimately attempting to compromise Office365, Gmail, Yahoo, AOL et al.
The phishing attacks always were done gracefully, redirecting in the right places etc, to minimize suspicion on the end user’s part.
While we watched these attacks ramp up in 2017 with a remarkable pace, we theorized on what would come next. Around September/October we got our answer.
This is when we began seeing an unparalleled spike in malware attacks being launched from compromised email accounts.
These ongoing attacks, also known as Conversation Hijacking Attacks (CHA), are personal and fool many.
Phase 1The first phase of this attack begins with an increase in email phishing traffic. Most often these phishing attacks rely on a web link that are often embedded in PDFs. The messages utilize varying themes to entice the end user into opening the attachment and clicking on the embedded URL.
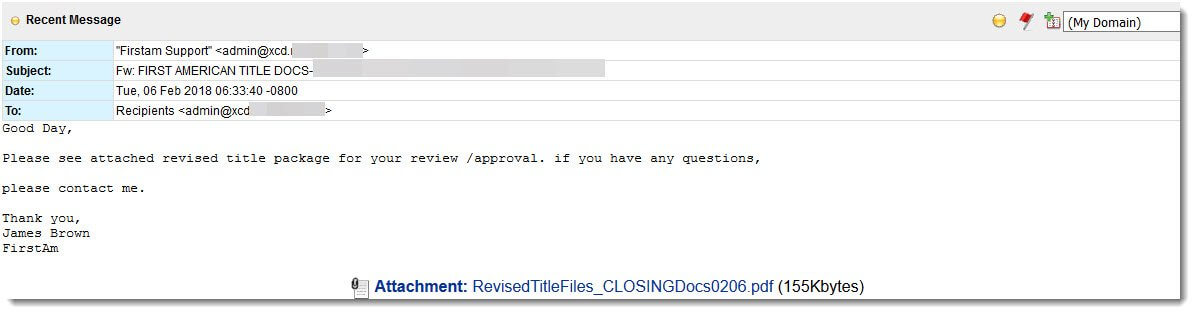
Here is a recent example of this attack. This message purportedly coming from First American Title and is specifically targeting the real estate vertical.
The URL embedded in the PDF attachment leads to the following phishing page where the target user can select their email provider of choice.
The victim is then taken to a customized login page designed to match the specific provider, where their email credentials are harvested.
Phase 2Now that the attackers have gathered the user’s login credentials they have the ability to launch malware attacks from the trusted accounts of their victim and do not have to rely on the same social engineering tactics they normally do.
From the compromised account, the attacker then hijacks ongoing email conversations by sending a malware attachment in a REPLY to a prior, legitimate email conversation. To the end user, the message comes quite naturally as they were having a back-and-forth exchange with the individual.
While most users know they should be highly skeptical of an attachment in an unsolicited email, this scenario looks to disarm the “user awareness” aspect of security, as the malicious message is anything but unsolicited. This significantly increases the likelihood the end user will open the attachment and become infected. In most instances, the malware family being delivered in this attack is the Gozi Banking Trojan.
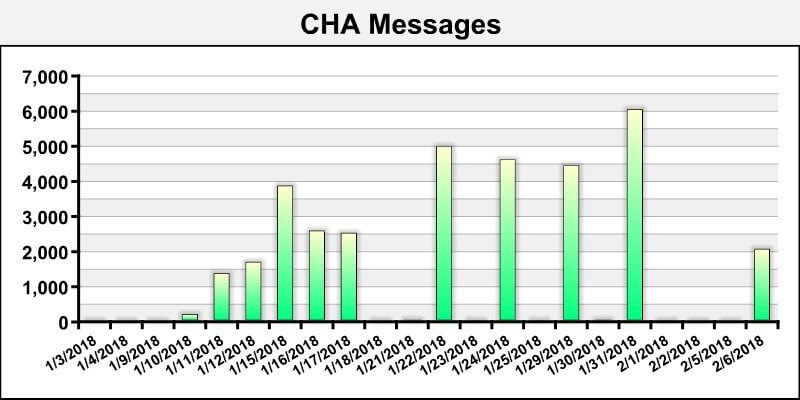
Attacks increasingWhat’s more, the frequency of these attacks has increased significantly over the past few months. We have been tracking them since their arrival. The chart below displays the daily total of the CHA (second phase) emails being sent from compromised accounts in 2018. Since Jan. 1, 2018 we have recorded more than 34,000 unique attacks.
These attacks also can be launched against internal contacts, which could have equally devastating results. In today’s age of highly customized and targeted attacks, one thing is certain — these multi-phased attacks are here to stay and will present even more of a threat going forward.
FOR THE FULL GLOBAL SECURITY REPORT: CLICK HERE
{{cta('8dddce58-7c8f-4e35-8895-353c48f9163a')}} YOU MIGHT ALSO LIKEhttps://blog.appriver.com/2018/02/global-security-report-ransomware/