Sextortion vs Bombtortion Hoaxes
Blog
Thought Leadership
Sextortion vs Bombtortion Hoaxes
David Pickett
Sextortion vs Bombtortion
On Dec. 13, bomb-threat hoaxes via email sparked law enforcement agencies around the world to chase down nonexistent devices. Many researchers and media outlets were quick in observing the similarity the bomb threats shared with sextortion campaigns. While the sextortion threats have been going on for months, adding a bomb-threat component is a new technique for these malicious actors. Since the majority of last week's threats originated from the 194.58.X.X IP space, we pivoted around that data point for further analysis.
IP Pattern Similarities
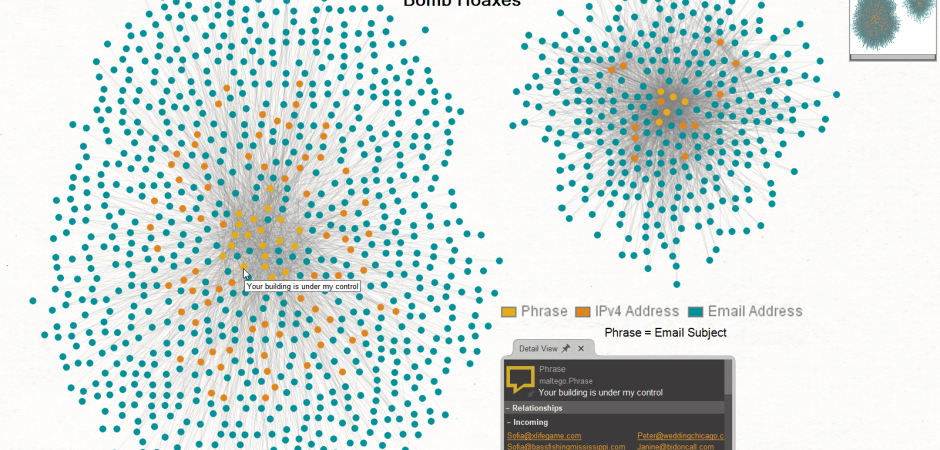
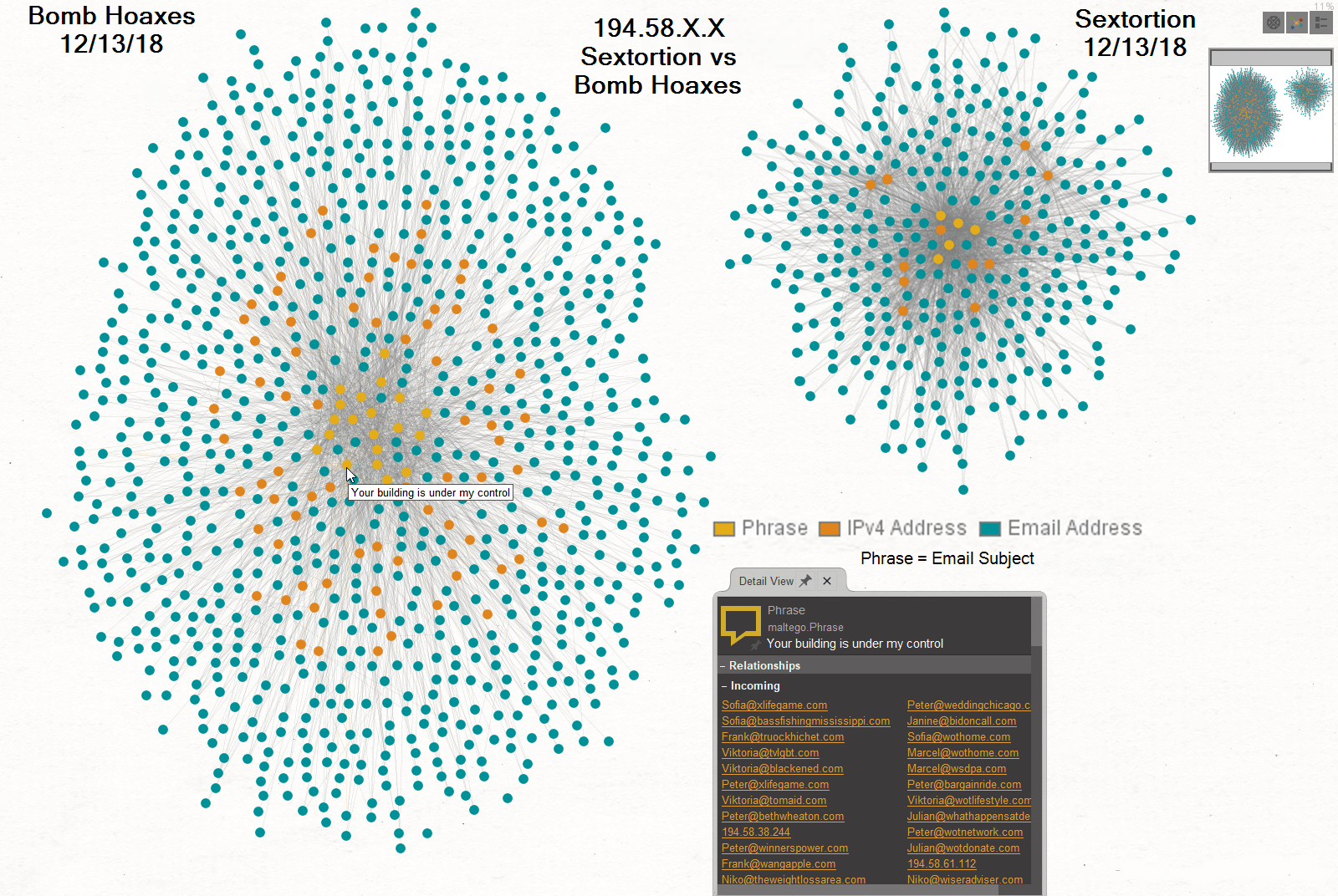
We began with 15,369 messages and pared it down to three data points per message. That provided a total of 46,107 data points to correlate.
DATA POINTS KEY
In the image below, email subjects translate to "Phrase" (gold)The other two data points are the "From: email address" (teal) and "originating IP address" (orange).
Once visualized, the two campaigns are distinctly separate, however, they appear to contain a very similar infrastructure setup. There are multiple instances where the distinct campaigns would alternate back in forth inside the Class-C IP address space but they never shared the same unique address.
One example:
194.58.39.153 - Bombtortion
194.58.39.160 - Sextortion
194.58.39.164 - Bombtortion
194.58.39.168 - Sextortion
194.58.39.179 - Bombtortion
Analyzing Raw Header & Message Data
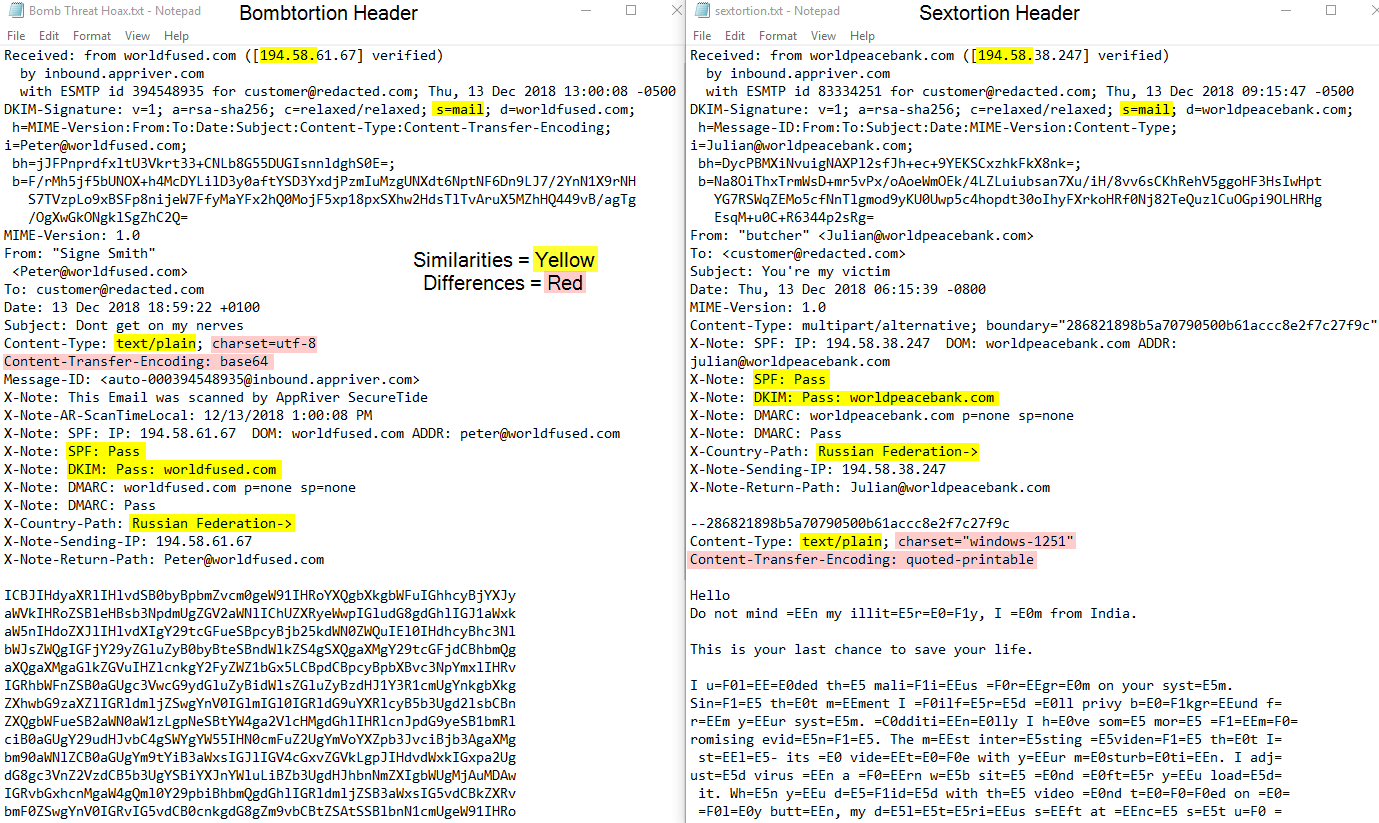
There were similarities and differences in the raw header data. We've highlighted these below for comparison purposes. Both messages passed sender verification checks such as SPF and DKIM, so DMARC passed. Both examples contain DKIM selectors set as "mail", share the 194.58.X.X space, and used text/plain content-types with different character sets and encoding. There is no "smoking gun" in this data set and many other data points to process. As stated, the purpose of this blog is to openly display some of the similarities and differences.
AppRiver Protection
There is no shortage of spam, malware, phishing or nefarious websites AppRiver's staff and systems continuously protect and defend against. Malicious actors work around the clock to infiltrate your network, and we at AppRiver work even harder to stay one step ahead of them. Our team is here 24/7 365 days a year protecting and supporting clients.
We always recommend defense in depth by utilizing layered security solutions. Adding SecureTide email filtering for inbound/outbound email traffic and SecureSurf for web filtering in conjunction with the built-in offerings of Office 365 or Microsoft 365 is an example of this. This builds upon the existing security functionality integrated into products and provides a more comprehensive security solution that will greatly enhance protection for users.
