New American Express Phishing Campaign
Blog
Thought Leadership
New American Express Phishing Campaign
Jonathan French

Phishing sites come in a wide range of persuasion. For example, there are certain nuances of a site, like images not loading and boxes not lining up, that normally raise red flags. But occasionally, an attacker will put in a lot of effort to make a convincing phishing campaign. We recently observed a phishing campaign coming in with links to fake American Express websites in the messages. While phishing campaigns are prevalent, a little more effort was put in to it than a lot of other recent phishing campaigns. As of the publication of this post, the counts are around 220,000.
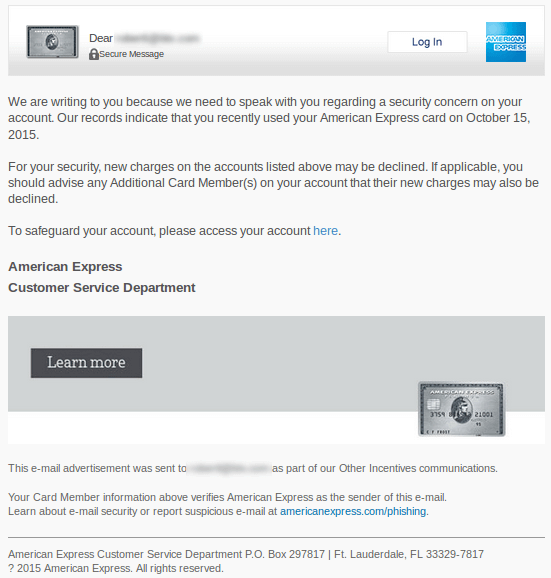
As with all email phishing campaigns we see, it starts out with an email. The email coming in is informing the user there is a security concern on the account and that future charges to their card may be declined unless they access their account. The message looks pretty convincing compared to most spam and phishing emails. It even contains a notice at the bottom about reporting suspicious emails to americanexpress.com/phishing.
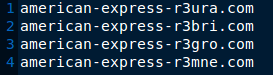
While all of the messages appeared the same, they contained a variation of 4 links to the sites hosting the phishing page. All four had two A record entries in their DNS with one IP belonging to a provider in the US and the other in Romania.
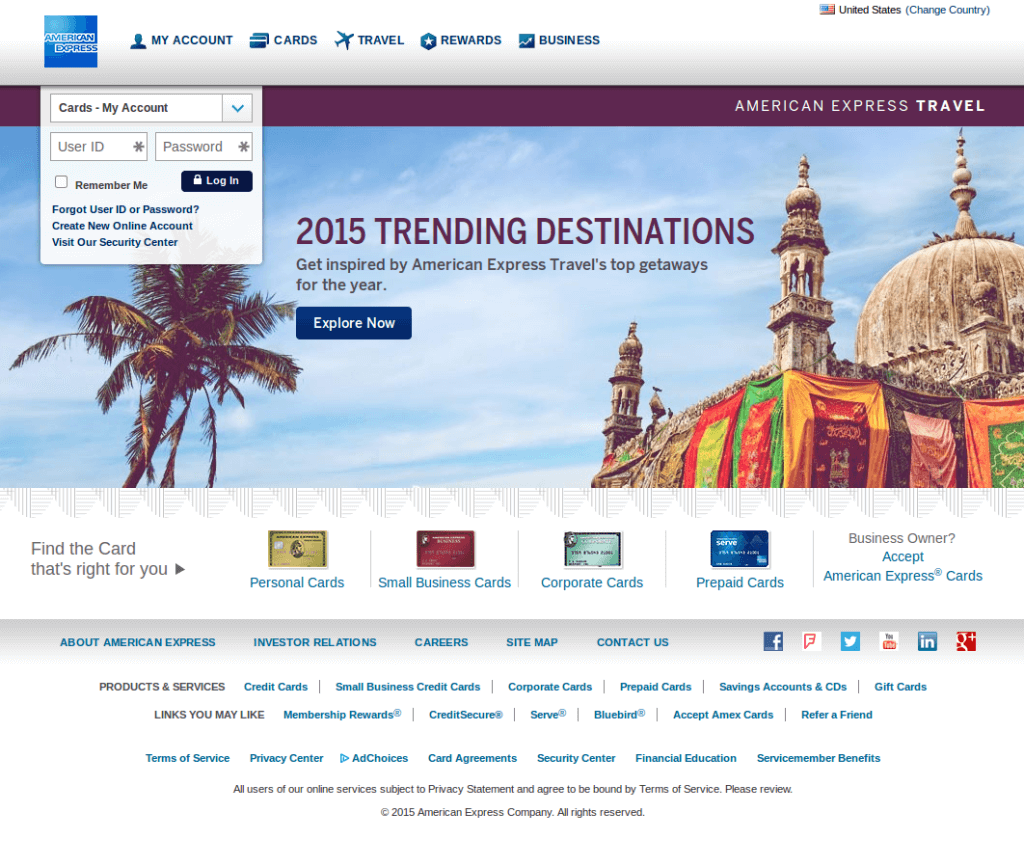
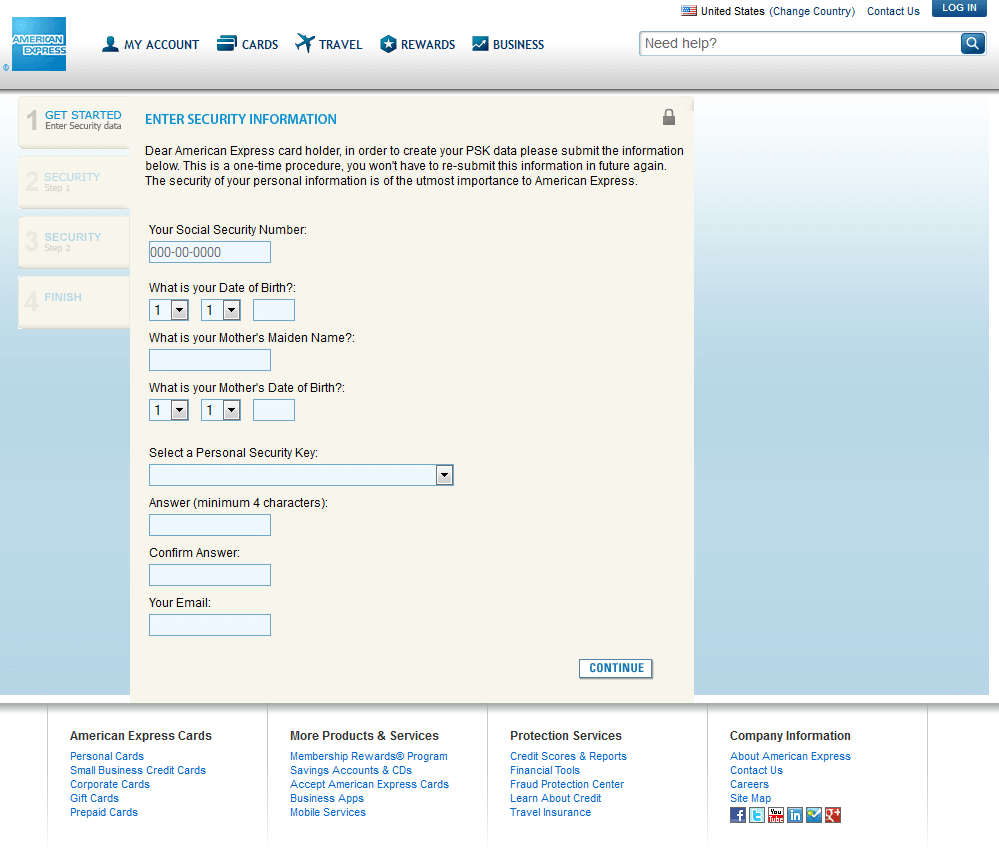
The key to a convincing looking phishing website is to try and make it look and feel as much like the mimicked site. In this case, the attackers did a pretty convincing job. Things like menu items fading, hovering the mouse over things, and the layout were all very similar to American Express' actual website. Feel free to click the images and take a look. Looking at these two images initially,it would probably be hard for most people to know which one is fake. I'll give a hint, the one on the left is real.
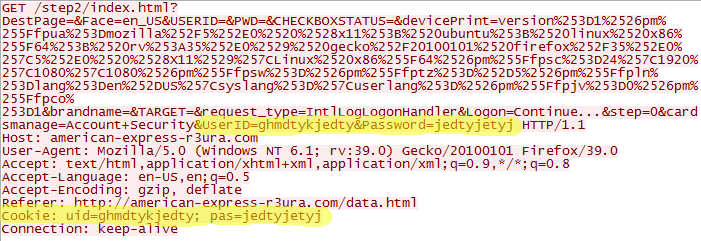
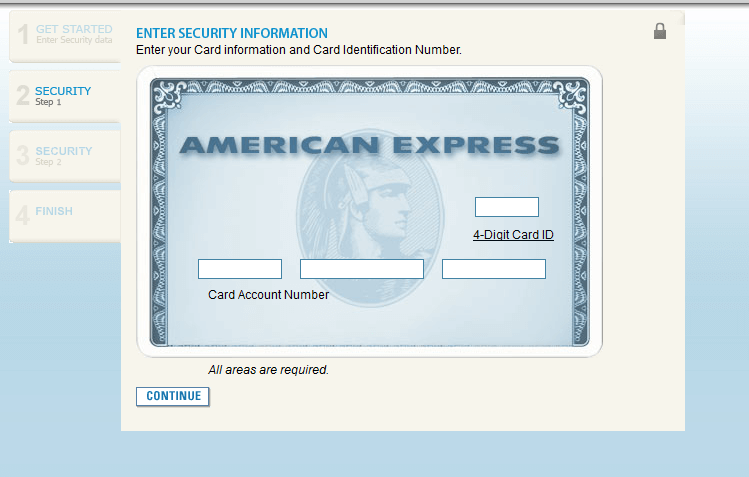
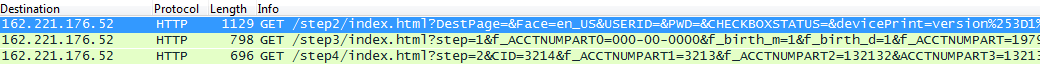
Now if you are unfortunate enough to try and login to the phishing site, they immediately get the username and password you entered. The username and password are sent plain text in the actual uri GET request and set as cookies in the http header. So as soon as you click login, there's no going back.
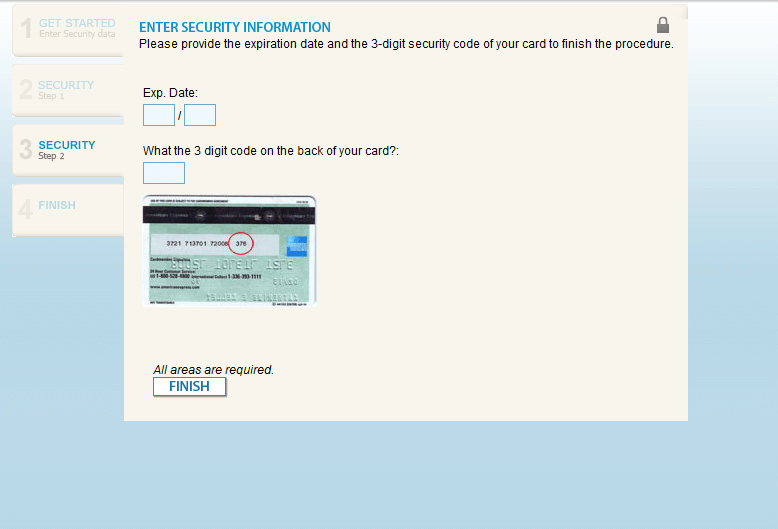
Now, an attacker could just stop there and redirect the user to the actual americanexpress.com website. This is a common tactic with email credential phishing sites. You get an email in that says you need to login to a website to see the attachment, then when you login they just redirect you elsewhere since they already have credentials. But in the case of this attacker, they are going all out and asking for pretty much everything. SSN, DOB, PIN numb, credit card info, etc.
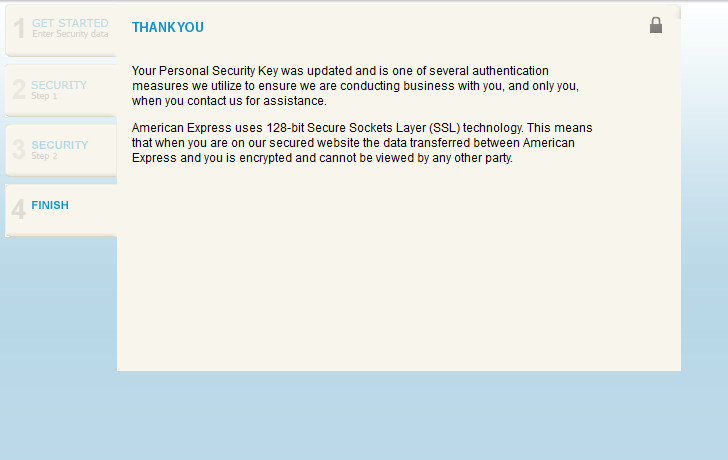
And of course after completing the info on each of thos epages, you can be rest assured they are sending that data back to the server in the GET requests for the next page.
This is a good example to look at of why a site can't be trusted just because it looks nice. Yes there are cases where phishing sites are glaringly obvious, but there are these cases where a lot of effort is put in to tricking users. In this case it sort of becomes pretty obvious it's a scam when it starts asking for all the other information. But with an attack like this at such a high count, there are unfortunately bound to be people that fall victim to this attack. being cautious of any sites asking for information is certainly a step, but also having systems in place to block known phishing sites can prevent the end user from even having to see the page to begin with. When we see campaigns such as this one, we are able to block the emails themselves once they start coming in as well as turn around and block the sites in our SecureSurf platform as well. So if a user did get an email to a phishing site or possibly found it some other way online, we would still be able to stop the connection to the site so the user never has a chance to enter in their personal information.