Zepto Ransomware in .hta files
Blog
Thought Leadership
Zepto Ransomware in .hta files
Jonathan French
Ransomware is very popular these days with many different variants constantly popping up. One of the more recent high impact versions is known as Zepto. We see many different file types abused in these malware campaigns - things like macro enabled word documents, .js script files, .wsf windows script files and so on. This morning though we had a campaign coming in using the lesser known .hta file format. This format is essentially an HTML file that uses some sort of browser supported scripting in it. While we have seen this filetype used before in malware campaigns in the past, it's not one we frequently see used.
The emails in question were pretty boring, lacking anything really other than an attached zip file. Doing something like this may offer attackers a few benefits in a broad campaign, such as having no body content to try and filter as well as not having to come up with some story about why the victim should open it. Curiosity of what's in the file may drive many people to opening and running the malicious attachment without the attacker even having to ask.
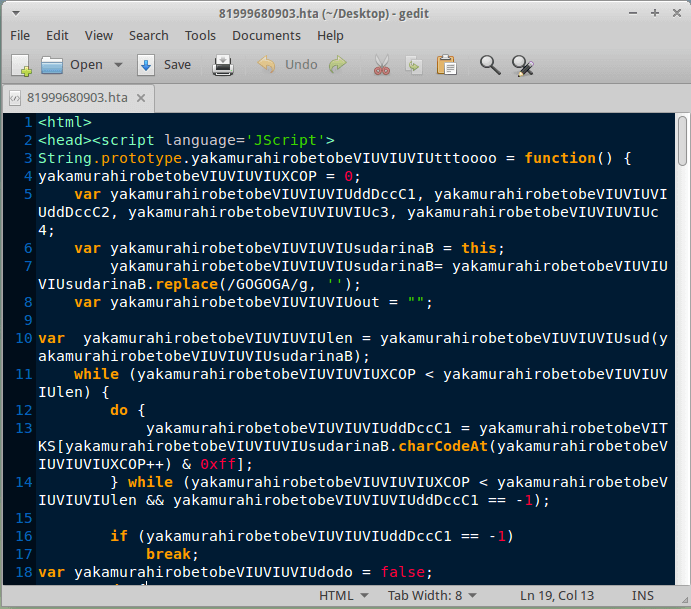
 The .hta file contents are written in an obfuscated javascript fashion that we're so used to seeing these days with the .js and .wsf malware. This obfuscation makes the code very confusing and pretty much unreadable to a human, however the code is still valid and will execute without a problem on the target system.
The .hta file contents are written in an obfuscated javascript fashion that we're so used to seeing these days with the .js and .wsf malware. This obfuscation makes the code very confusing and pretty much unreadable to a human, however the code is still valid and will execute without a problem on the target system.
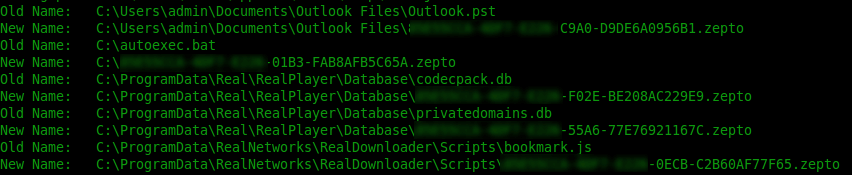
So once you run the malware, it does what you expect and starts encrypting files. It has a remote command server it uses to download the actual payload once the hta script runs, as well as a server it POSTs data to. In testing this, one of the first files it encrypted was the Outlook PST file. Since it used email as the attack vector, this may be a way to try and lock users out of the source of the malware for any investigating someone may do, as well as the broader picture of how important email can be for day to day operations of a business.
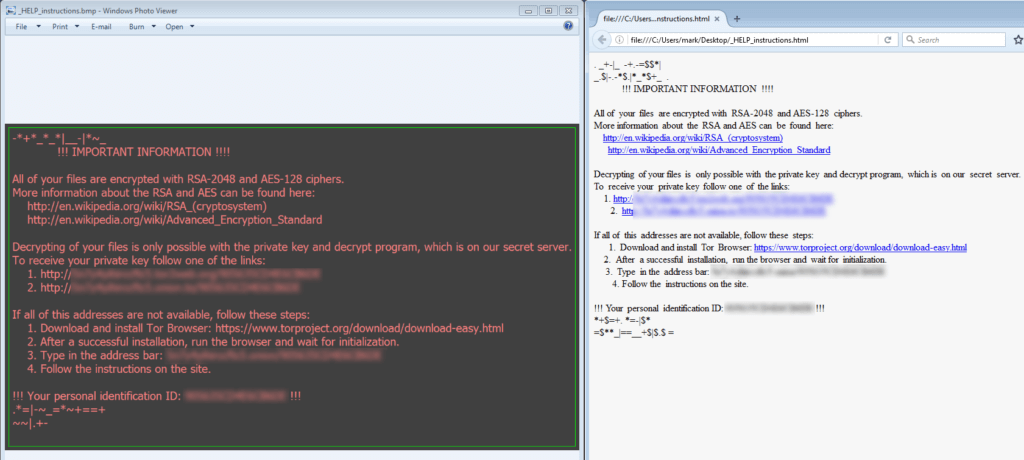
After all is said and done and the malware has done its damage, you get an image file popup as well as an HTML page breaking the bad news and going in to detail on how to pay the ransom.
So far this morning, the count we've seen for the campaign is about 11.5 million. Ransomware in general is a very big an obvious reason to take backups and security seriously due to the widespread occurrences these days. This email also serves as a great example of why you should never open unknown attachments, and that not all bad emails are going to be poorly worded or obvious in what they're trying to get you to do.