PayPal credentials make for popular Target
Blog
Thought Leadership
PayPal credentials make for popular Target
Troy Gill
An onslaught of PayPal themed messages have been hitting our filters over the past few weeks. Utilization of attached (.)HTM/HTML files to distribute malware and phishing attacks has been actively used for the better part of a decade now. This file type is still considered relatively low risk since they are still shared for legitimate purposes quite regularly--despite that fact that they are used for evil with even greater regularity.
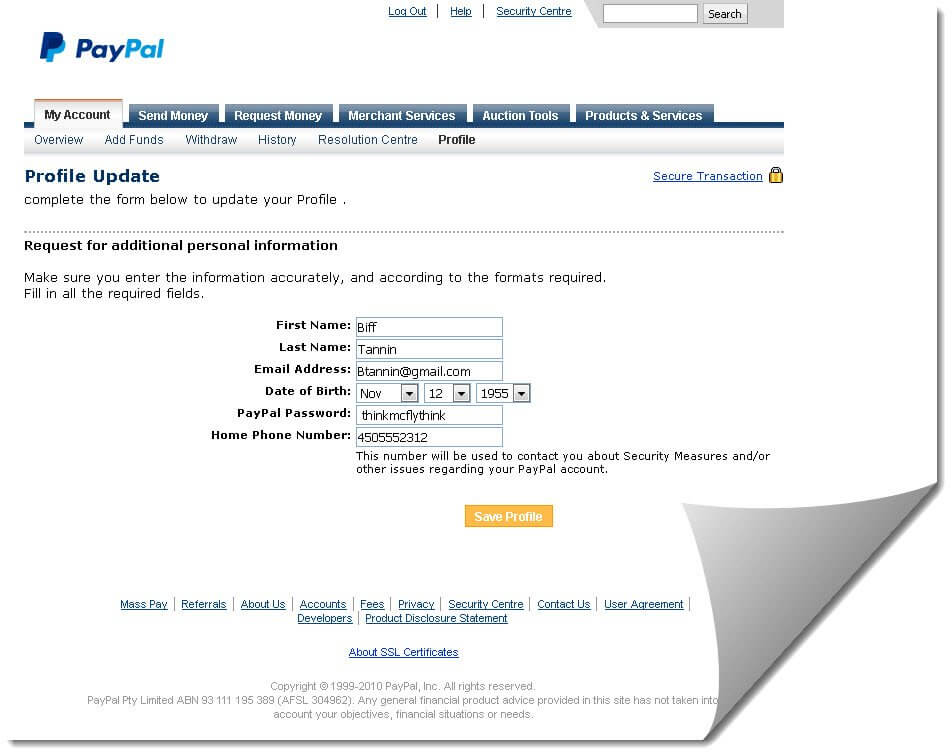
One particular variant poses as a security alert from PayPal. It utilizes an attached (.)HTM file (containing an embedded script) in an attempt to trick users into disclosing a bevy of personal and financial information. Thus far, we have quarantined roughly 250K messages from this particular campaign. In addition to phishing a potentially devastating amount of information from the target, beneath the surface the obfuscated script also serves to install malware onto the victim’s machine.
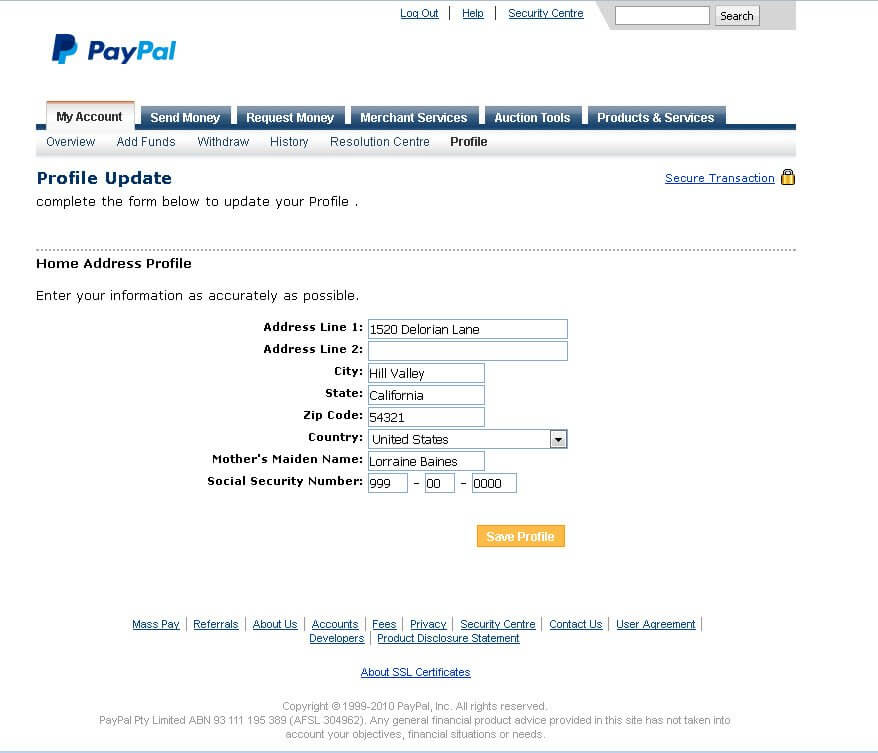
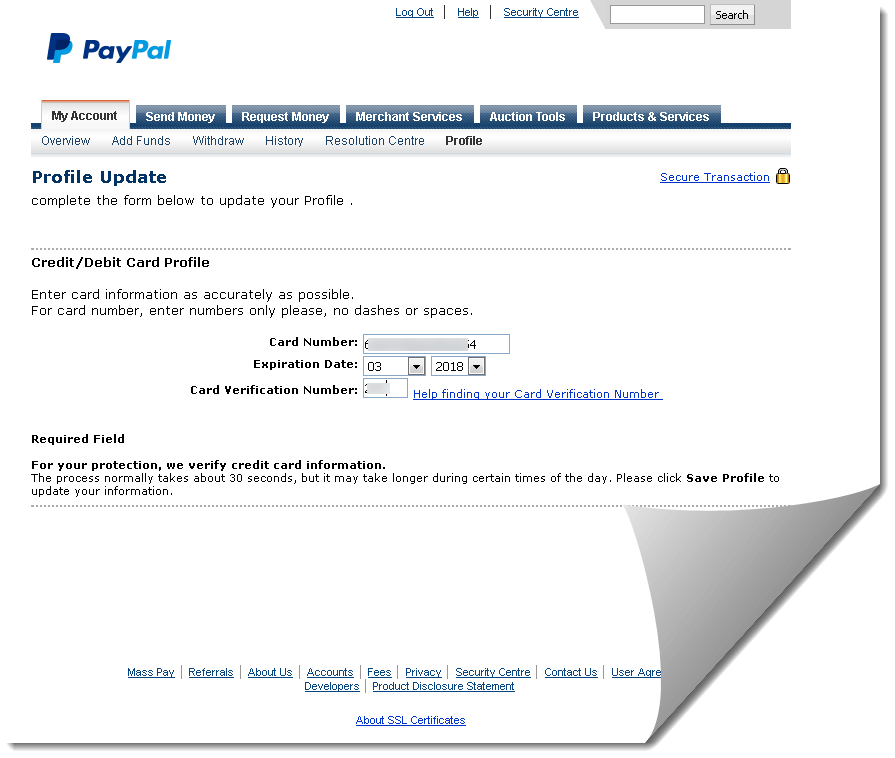
Clicking the attached (.)HTM file begins the process. The phishing pages rendered attempt to gather a great deal of information such as PayPal credentials, mother’s maiden name, social security and credit card data-- in a series of three consecutive phishing pages (displayed below).
page 2
page 3
Remember, a legitimate security alert should never require direct interaction with an email attachment. Should you ever find yourself on the receiving end of a message of this nature, reach out to the company directly to voice your concern.
If you suspect you may have fallen victim to phishing or think your credentials have been exposed through some other means (such as a data breach) you should take immediate proactive measures to help reduce the potential impact. Always contact the provider immediately for their recommended course of action. Change your password for not only the effected account but also for any others where you may be using the same or similar password but surely no one is doing that... right?