Locky Bringing the Malware Volume Back Up
Blog
Thought Leadership
Locky Bringing the Malware Volume Back Up
Jonathan French
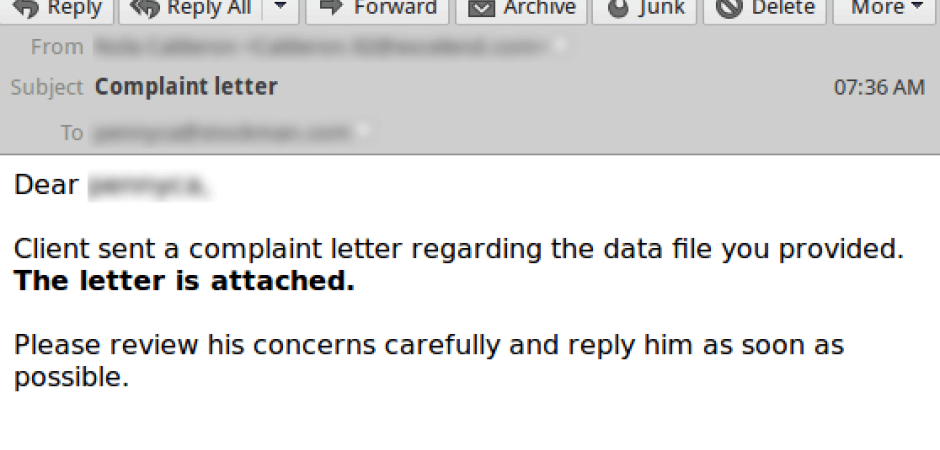
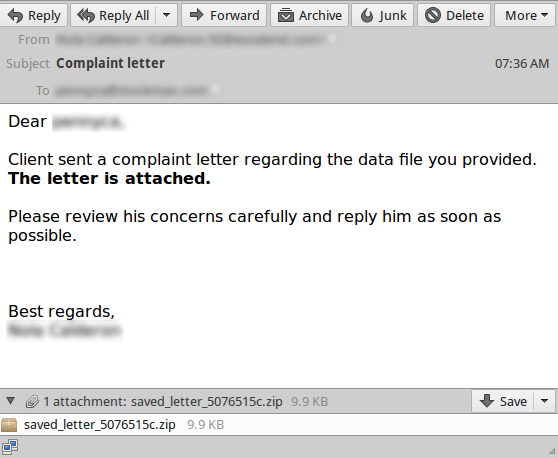
Earlier this year, we had a lull in malware traffic for about three weeks after the Necurs botnet quite suddenly stopped sending out junk. History repeated itself on October 6th when we experienced another drop in malware traffic. Today, that dive in traffic might be over, ending this streak. The Locky malware has kicked it in to high gear again this morning dishing out around 14 million virus emails so far.
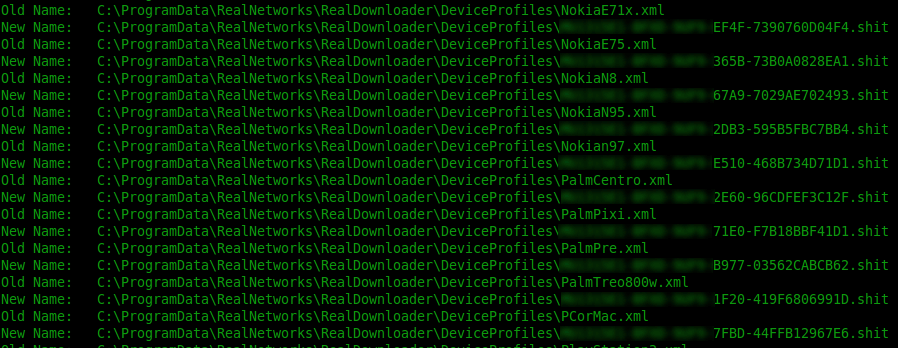
The attached zip file unzips in to 130kb .js file. This file is again similar to the tactics used in JavaScript malware this year where the file itself is heavily obfuscated to avoid detection. When executed, it goes through its normal encryption phase. With many variants out there, we often see the same variety of extensions being used on the encrypted files. If you have a file named family_photos.jpg, ransomware may go back and name it something like M5096-GT654-GHT.locky. This variant is using a similar name format as the others we have seen, but the extension this time is .shit. Presumably this extension was chosen just because they can use whatever extension they desire.
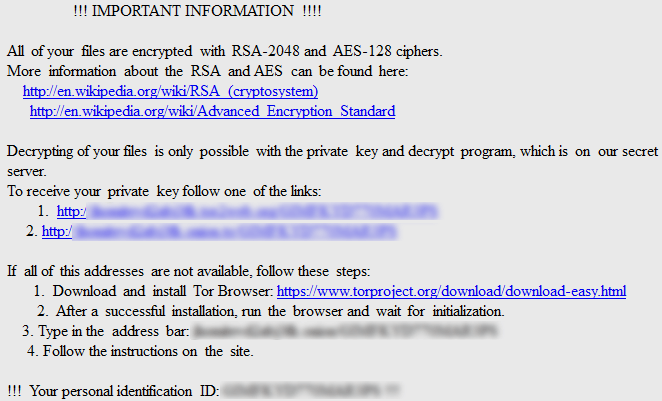
After encryption, I found an HTML file on the desktop with the ransom note as well as receive an image popup with the information on how to pay the ransom using Tor. This is pretty standard practice once the file encryption process is done.