LogMeIn-Themed Emails Deliver Banking Trojan
Blog
Thought Leadership
LogMeIn-Themed Emails Deliver Banking Trojan
Troy Gill
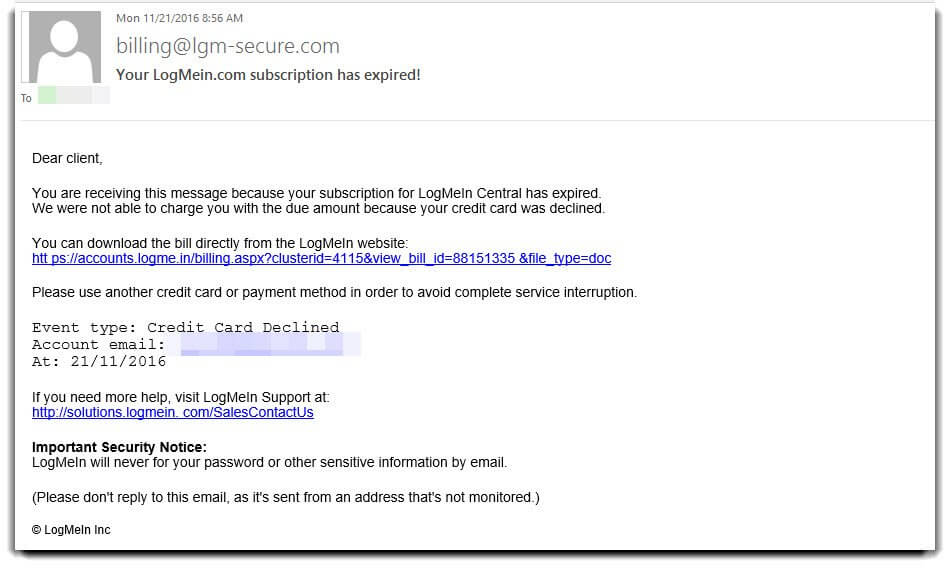
This morning we began seeing an influx of emails attempting to dupe users into downloading and opening a malicious office document. The messages are made to look like an alert from the popular remote access and password management provider LogMeIn. They state that your payment method has been declined and offers a link to “download the bill directly".
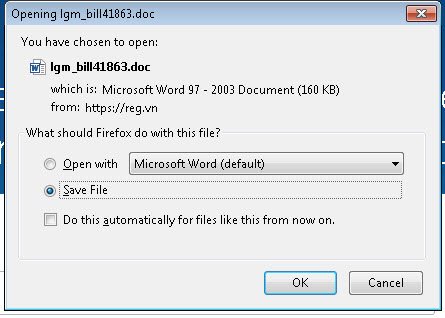
Here's a look at the message and subsequent file download:
The file is actually a macro-enabled .doc file that contains the ever-growing banking malware known as “VawTrack” or “NeverQuest”. While most of the macro malware we have seen lately contains ransomware such as Locky, this one is a different sort of evil. This particular malware has been in circulation for a few years now but has continued to evolve with both the way it infects as well as functionality within the code. In this case it appears to use the Pony executable within the document. Once the infection has gained a foothold, it then calls home and pulls down the VawTrack infection. This malware quickly goes to work collecting and infiltrating data via HTTP that is disguised to look like legitimate traffic.
In the past few hours we have seen tens of thousands of these messages hitting our filters, though this only represents a small percentage of the total traffic associated with this particular campaign. This is just the latest in the ongoing attacks from this malware family that we have been monitoring.