Phony HSBC Emails Carry Spyware Infection
Blog
Thought Leadership
Phony HSBC Emails Carry Spyware Infection
Troy Gill
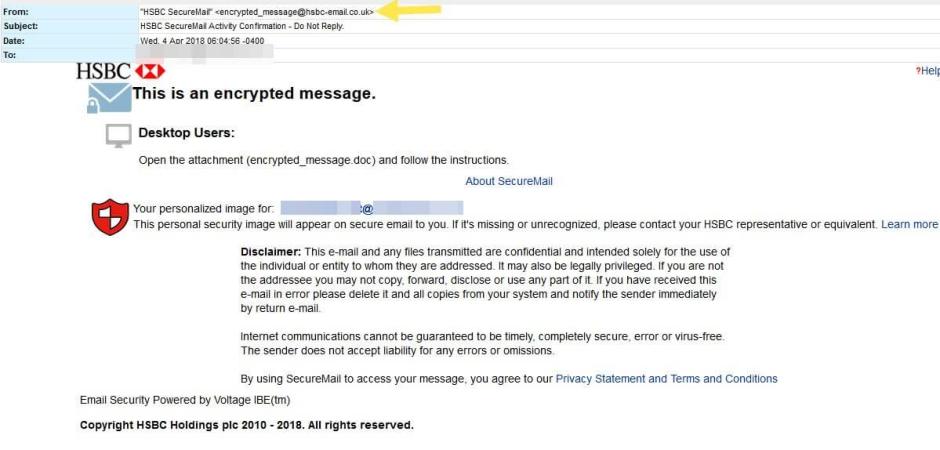
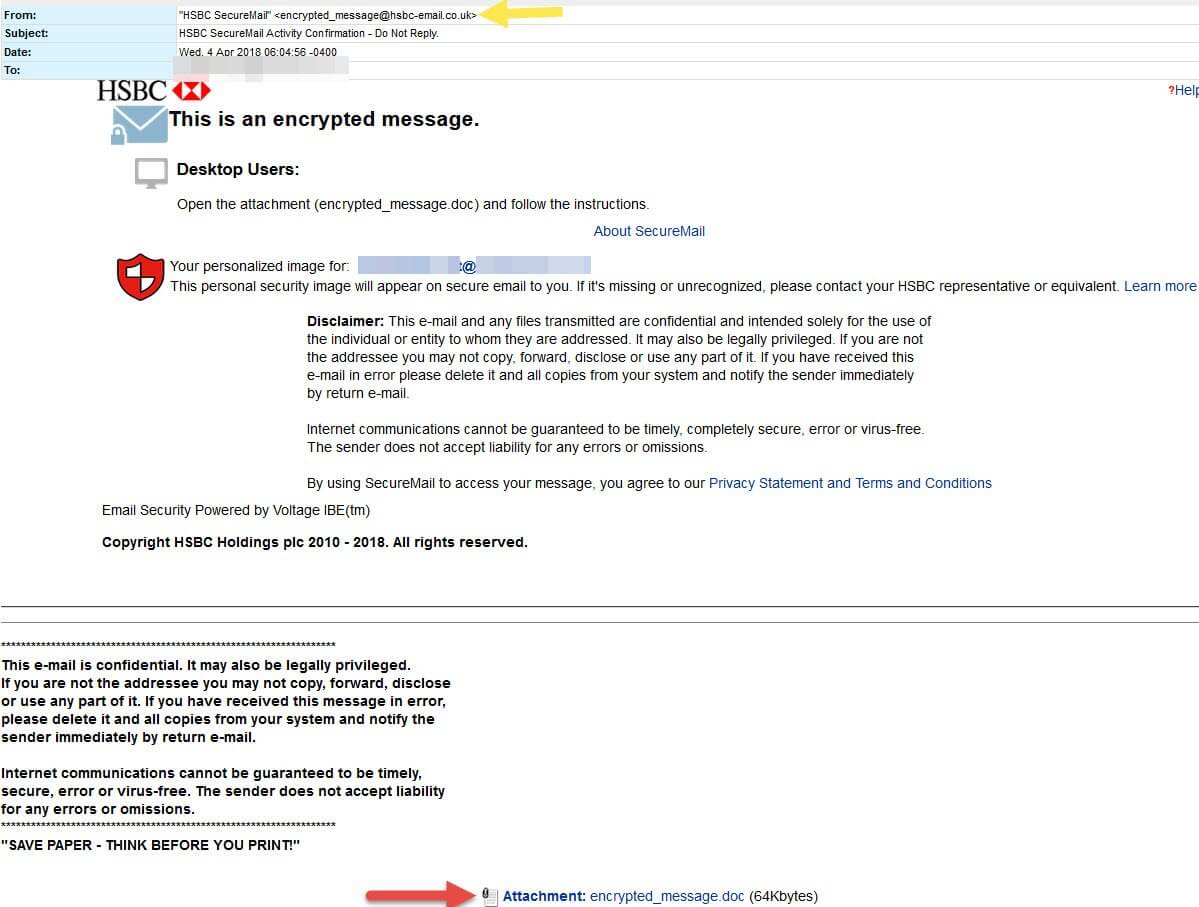
Today we are seeing a malware push from the Necurs botnet attempting to distribute a Spyware Trojan via the Hancitor downloader. The malicious email campaign is somewhat cleverly disguised as an encrypted email from HSBC Financial.
The emails are laid out in a convincing manner and utilize graphics and language meant to be consistent with a legitimate encrypted message from HSBC. The attackers utilize the domain hsbc-email[dot]co[dot]uk in the “From” field. The domain, which was registered yesterday, makes these messages appear a little bit more convincing to the target.
The attached Word DOC file has embedded macro functionality to create the initial infection of the Hancitor dropper. It then goes on to pull down (via PowerShell) more malicious payloads containing some very evasive Spyware which has some indicators of the Trickbot banking Trojan. This is not unusual as we often see the Hancitor downloader serving up banking Trojan infections.
We observed the following network communications during analysis.
214.141.134 Poland 95.97.136 Russian Federation 169.44.149 Indonesia 255.36.1 NetherlandsUsers need to be extra cautious with any unsolicited email, especially ones containing links or attachments, no matter how legitimate they may appear. At the time this campaign began, only 3/58(5.17%) of AV engines were detecting the file as malware according to VirusTotal. Fortunately, SecureTide already contained preemptive rules that blocked this threat from the onset. We are currently blocking all known variants.
CONNECT WITH USLike us today on Facebook, Twitter, YouTube and LinkedIn.
YOU MIGHT ALSO LIKEhttps://blog.appriver.com/2018/02/office-365-business-email-compromise-attacks-proliferate/