BEC Attacks Evolving - Phishing via XPS Files
Blog
Thought Leadership
BEC Attacks Evolving - Phishing via XPS Files
David Pickett

We've seen it time after time, malicious actors routinely attempt to confuse recipients of messages with obscure or lesser-utilized file extensions.
Over the past month, some phishing attempts using xps files instead of the typical pdf or doc/docx formats have been captured by our filters. The xps file format is Microsoft's alternative to pdf files. Windows machines with Vista or later operating systems natively support this extension with Windows xps file viewer. Actors have started taking advantage of this lesser-utilized format for their phishing campaigns.
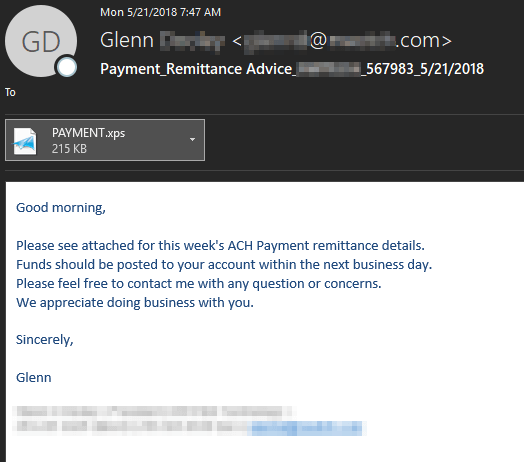
Phishing ExamplesOur SecureTide email filtering has captured a wide range of these phishing messages. So far, they appear to be attributed to threat actors currently conducting Business Email Compromise (BEC) attacks. Attacks originate from legitimate (compromised) senders with the similar techniques, tactics, and procedures. Below is an example which could easily dupe unsuspecting users.
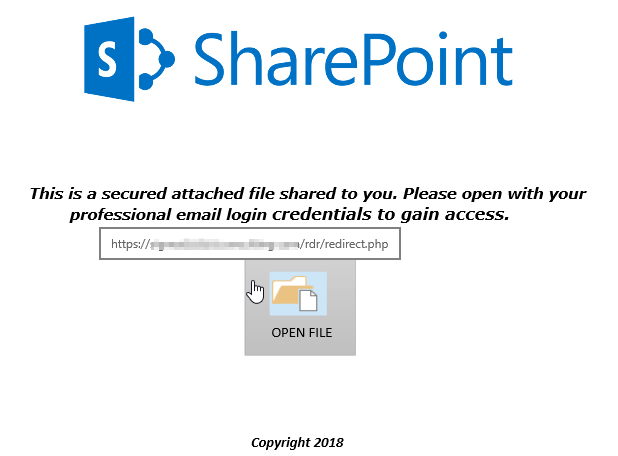
Viewing the XPS FileUsers should not open or view unsolicited attachments, even from a known sender without intense scrutiny and/or verification. Scammers do exploit the trust that known contacts share. Hopefully a user will never see one of these, however, this is what these attached files look like when opened in an isolated test environment.
Linked Phishing Portals
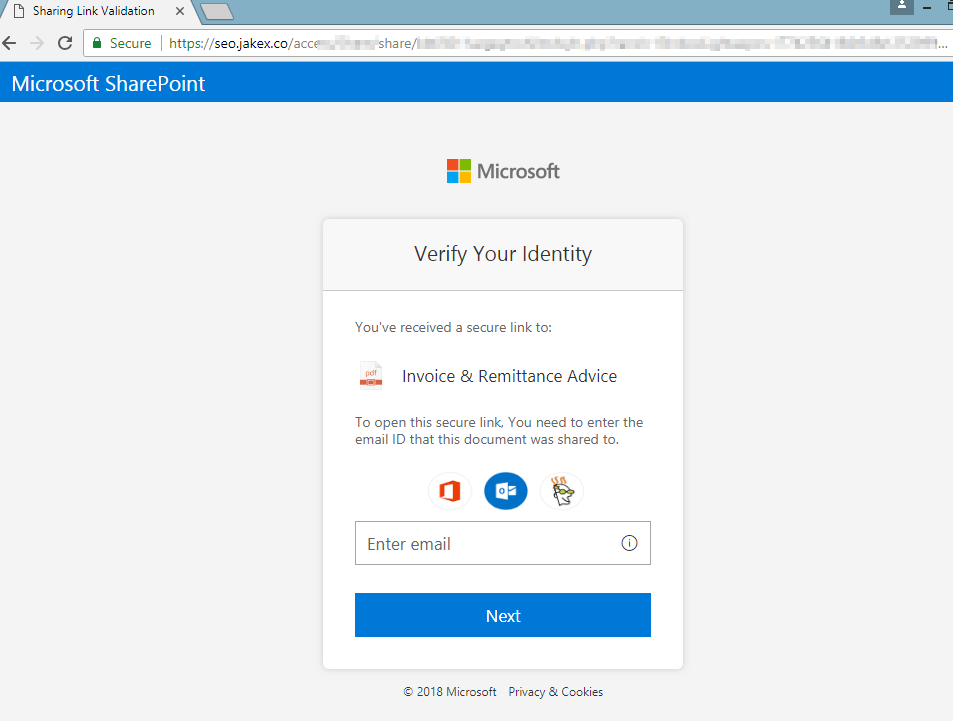
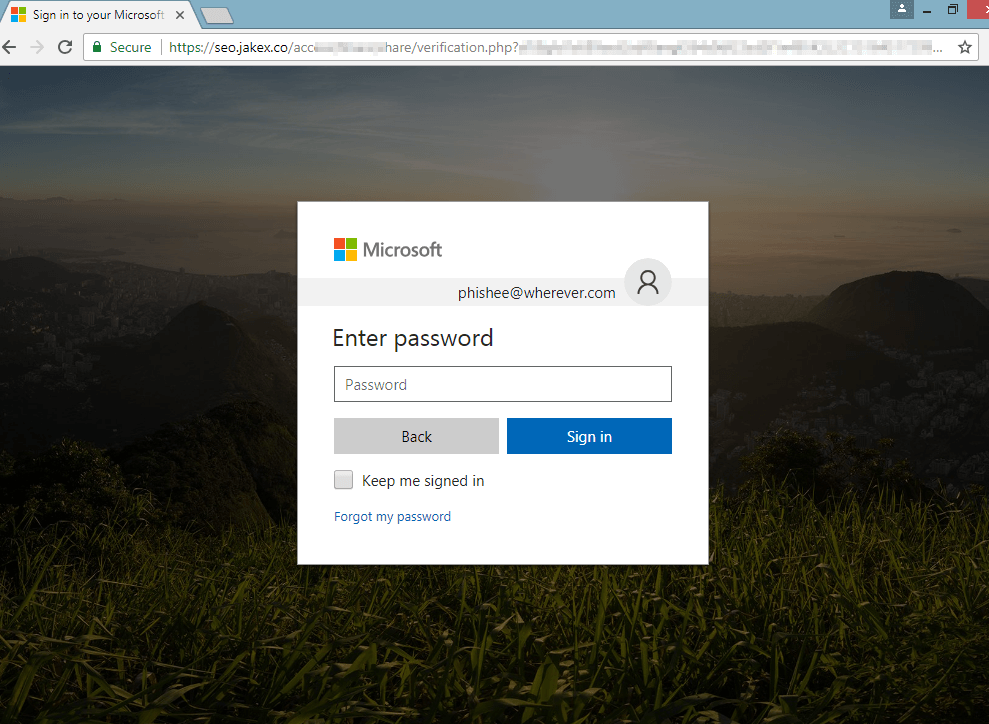
If the user happens to click on the link in the attached xps file (pictured above), below is an example web phishing portal they might encounter. For this particular one, the first screen requests their email address. If they proceed with entering it, the next image shows the resulting page requesting their email credentials.
After entering email address:
Filter Evasion Techniques
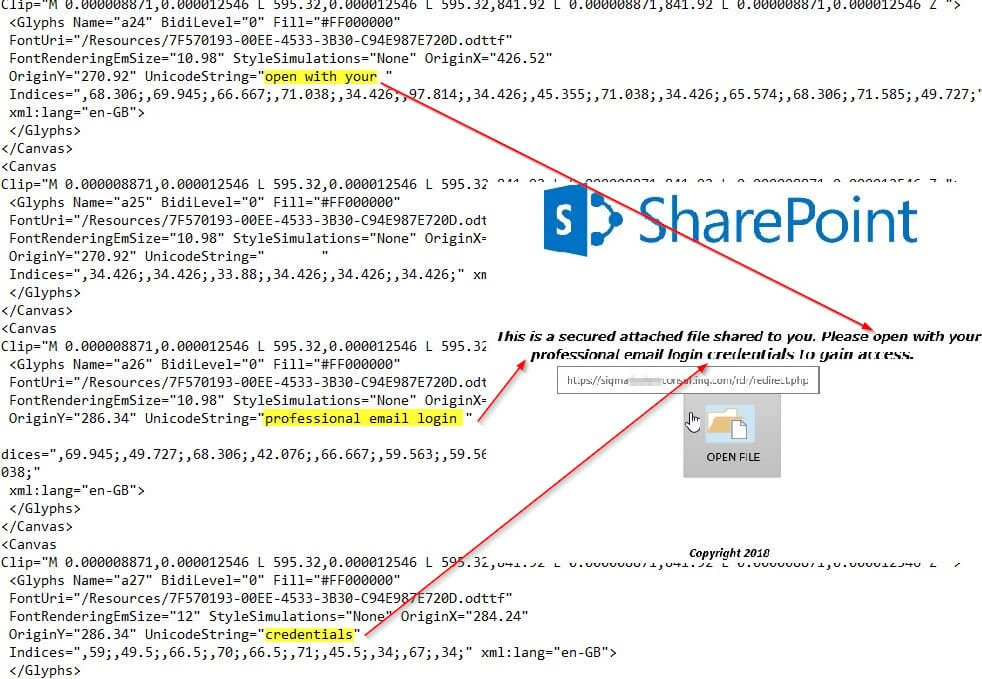
Malicious actors are attempting to use filter evasion techniques. They break up the suspicious phishing text via canvas clip mappings inside deeply embedded fpage files. An image portion below displays how they used multiple canvas clip mappings to stitch together the words, "open with your professional email login credentials."
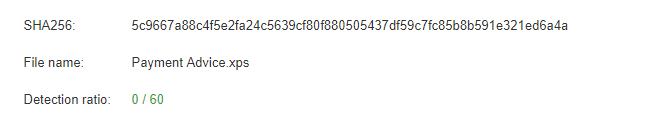
Minimal Anti-Virus Signatures for XPS FilesMost anti-virus engines do not have many phishing rules setup for the xps extensions like they would for more commonly used ones. We can see this example received 0/60 hits when processed thru a popular anti-virus engine aggregator.
AppRiver ProtectionThere is no shortage of spam, malware, phishing, or nefarious websites AppRiver’s staff and systems continuously protect and defend against. Malicious actors work around the clock, therefore, we at AppRiver work even harder to stay one step ahead. Our team is here 24/7 365 days a year protecting and supporting clients and partners from security threats.
{{cta('8dddce58-7c8f-4e35-8895-353c48f9163a')}}
You May Also Likehttps://blog.appriver.com/2018/02/office-365-business-email-compromise-attacks-proliferate/