WANTED: Your Office 365 Credentials
Blog
Thought Leadership
WANTED: Your Office 365 Credentials
Troy Gill

Here we go again - attackers are going "phishing" in search of user's Office 365 credentials.
In the past we have seen this sort of activity ramp up dramatically at many different points in time, and it is usually followed by a corresponding increase in attacks being launched from the compromised accounts.
Today we are seeing an increase in this (phishing) activity to be certain. In particular, one campaign is targeting Office 365 users by posing as emails from Microsoft. They purport to be "delivery failure" notifications and offer a clickable link to fix the issue.
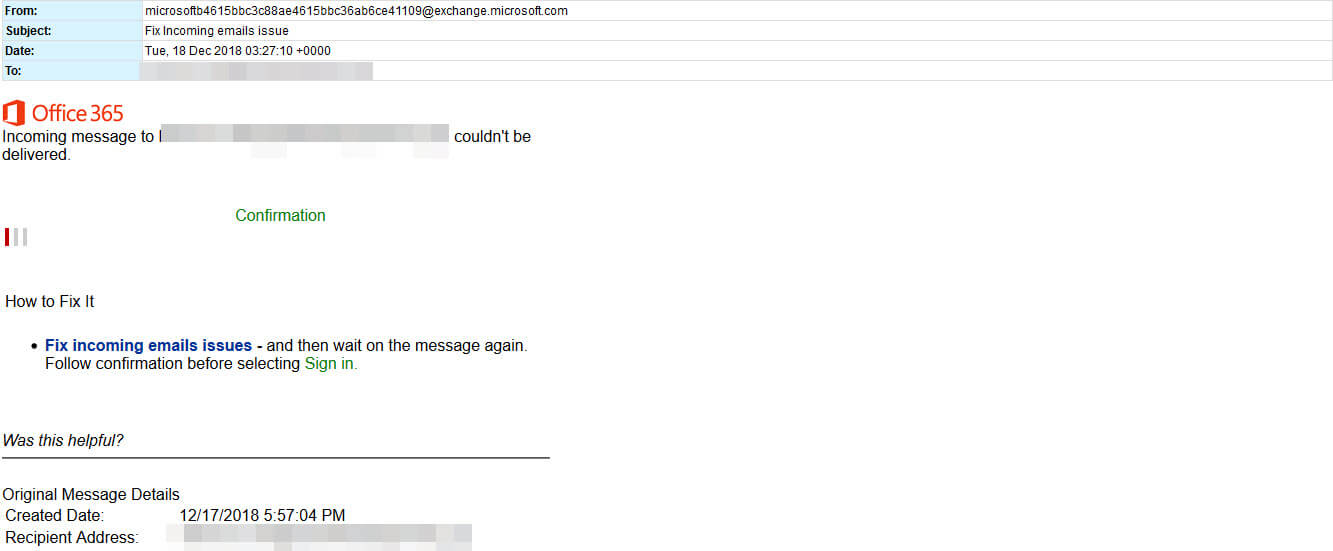
NOTE: This type of email is NOT something Microsoft ordinarily would send.
Interestingly the URL’S embedded into the messages appear to be abusing Microsoft Azure Blog “Azure Blob storage is Microsoft's object storage solution for the cloud. Blob storage is optimized for storing massive amounts of unstructured data, such as text or binary data. Blob storage is ideal for: Serving images or documents directly to a browser.”
I guess in this case that data just happens to be payload links to a phishing site.
It's unclear at this time as to how the attackers are exploiting Blob. Whether they are abusing a legitimate hacked resource, have created their own resource to be used in this attack or (and probably the least likely) found some way to exploit this service to expose links publicly remains to be seen. Some of these attacks have spoofed the Microsoft domain as the sender while others are spoofing the xbox domain.
Here’s a look at the phishing page attempting to harvest user credentials
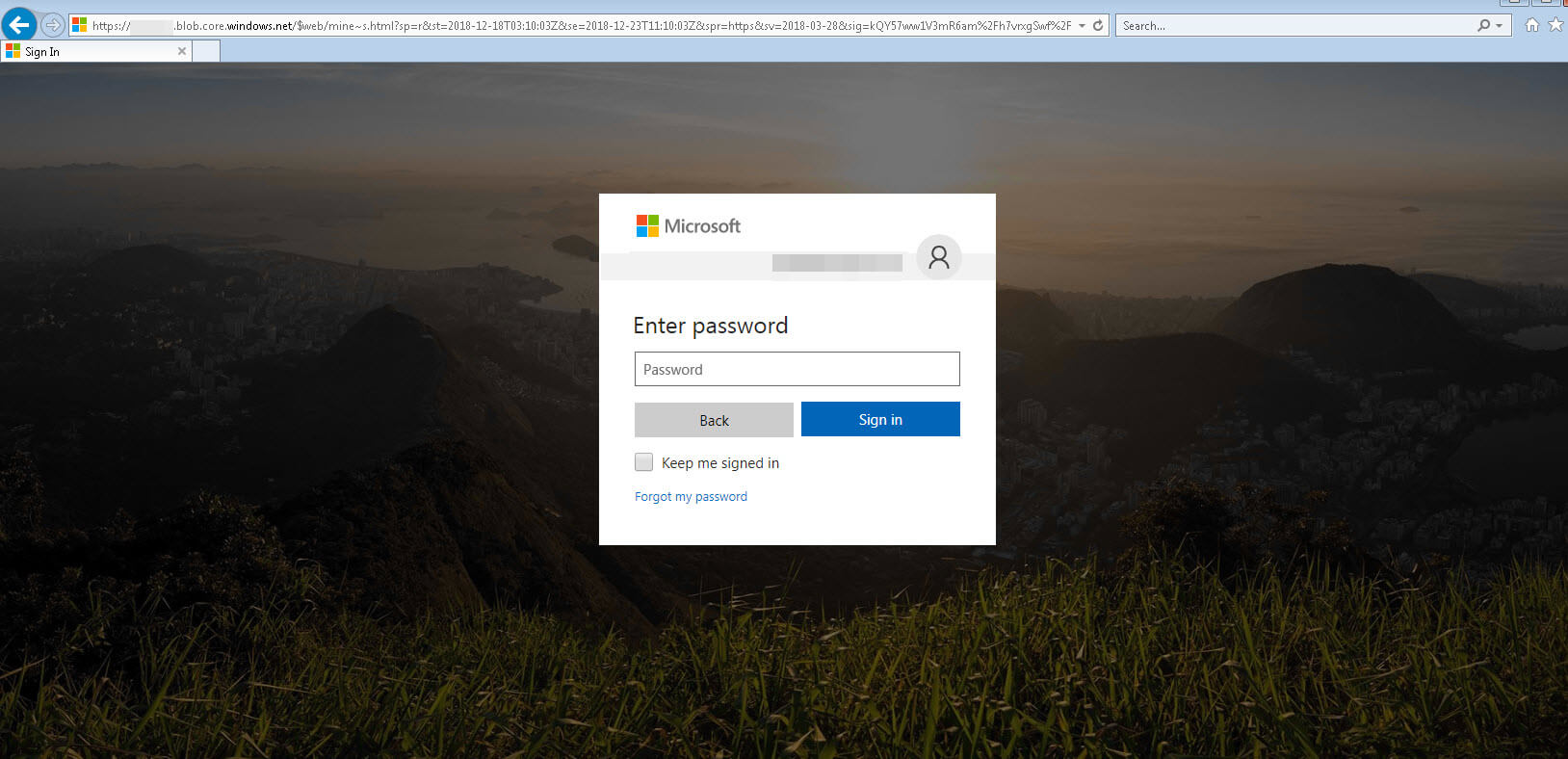
As we know all too well. These credentials will be used to commit IP theft, launch CHAs and commit BEC (wire transfer) attacks and more as it follows the normal patter of Phish,Exploit,Phish,Exploit, rinse and repeat.
Our Advanced Email Security customers are protected from all known variants of this threat. If you think you have fallen for this attack or one similar fell free to contact us about our Microsoft O365 Security Audit—which can help identify user accounts who may be compromised.
