Social Engineering Attack Escalation
Blog
Thought Leadership
Social Engineering Attack Escalation
David Pickett

SANS Institute conducted a survey on how attackers were able to compromise user devices. They found 74 percent entered via an email attachment or email links, 48 percent from web based drive-by or download, and 30 percent through application vulnerabilities. Phishing (72 percent), spyware (50 percent), ransomware (49 percent) and Trojans (47 percent) are the threats most seen by respondents. We continuously monitor the latest attack vectors and scam techniques utilized. This helps us stop current campaigns and anticipate future vectors. This blog details how an example social engineering attack occurred.
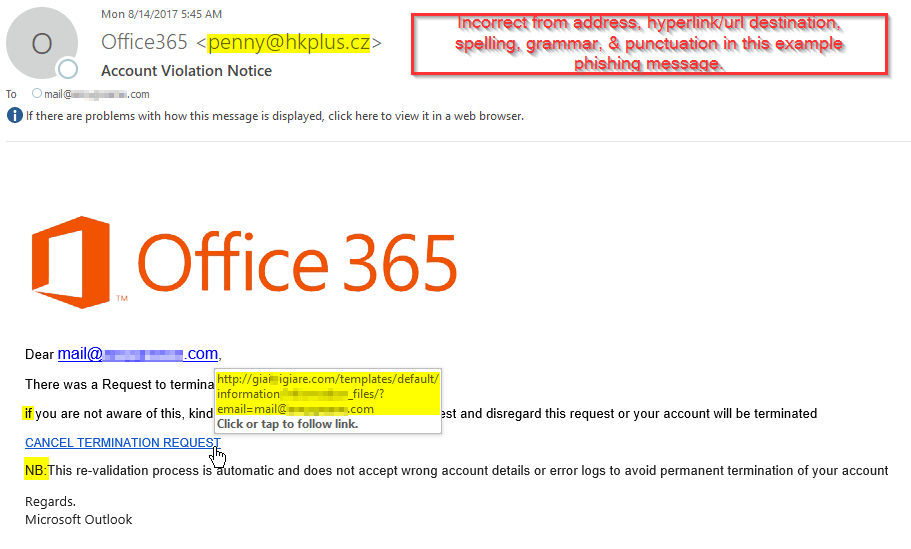
Step One: Phishing Attack
There are no shortages of phishing email examples. Attempts closely mirror the use of a whack-a-mole analogy. We'll knock one attempt out and see another pop back up elsewhere. While creating rules to stop these we think outside the box to anticipate what the payload will be, how it will appear, and where the next one will pop up. I've highlighted areas that should raise user suspicion of authenticity.
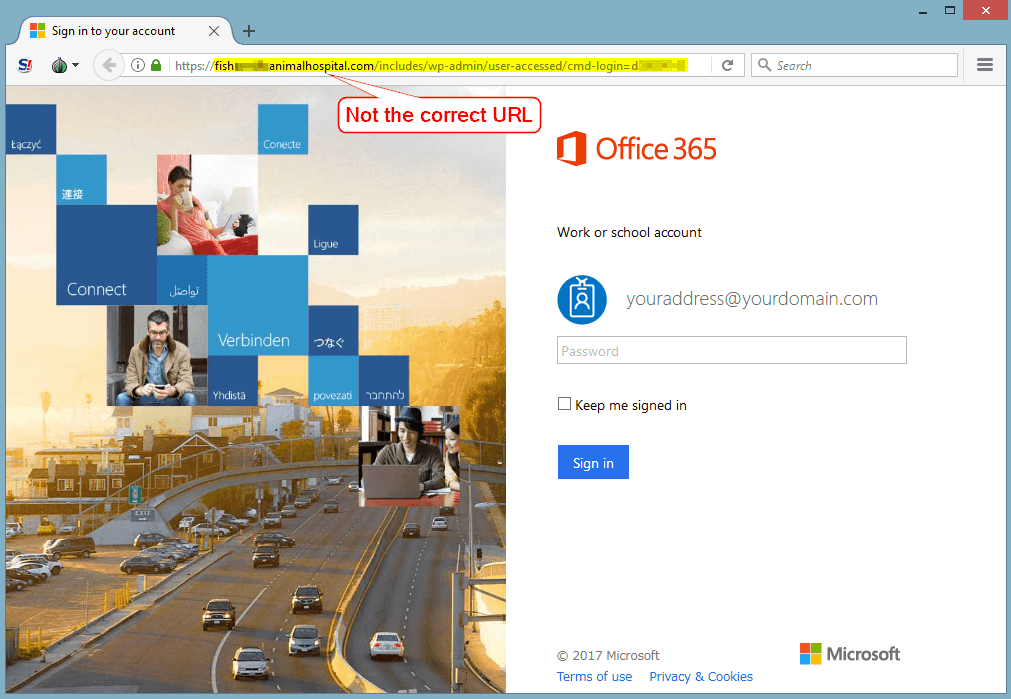
Step Two: Fake Login Portals
The attackers have gone out of their way to make the website login portal appear legitimate. Hopefully the user didn't fall for the phishing attack and make it this far as some sites contain malicious content. The url in the web address bar should cause internal alarms to sound before credentials are entered.
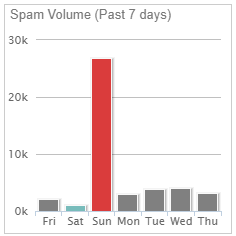
Step Three: Distributed Spam Distraction AttackDistributed spam distraction (DSD) is a term we use to describe this technique. The attacker floods the victim inbox with thousands of emails quickly to create a distraction. This occurs simultaneously with account theft, fraudulent activity, password resets, or whatever the malicious intent may be. Typically they are after victim or client money the victims has access to. Targets should prioritize attention to financials, data theft/loss, or other suspicious account activity then seek assistance for the email distraction.
The recent DSD examples have been an avalanche of email newsletter signups and confirmation emails. The attackers use thousands of legitimate website newsletters, forms, and email lists to sign up the victim for. When ready, they run a bot, script, or website to send emails at a rapid rate. The average duration of heavy inbound email traffic subsides under 24-48 hours. As an example, one customers spam volume graph is pictured below. At AppRiver, our SecureTide spam and virus filtering team works 24/7/365 to block these attacks.