THREAT ALERT: Cybercrooks Abusing Microsoft Azure Storage Custom Domain Name Feature
Blog
Thought Leadership
THREAT ALERT: Cybercrooks Abusing Microsoft Azure Storage Custom Domain Name Feature
David Pickett

THREAT ALERT: Cybercrooks Abusing Azure Custom Domain Name Feature
AppRiver's SecureTide email filter provides customers protection against the latest threats 24/7/365. We see plenty of new variants each day, however, this particular attack caught our attention. Malicious actors search for any technique possible to entice an unsuspecting user to fall for a phishing message. The more legitimate looking they can make their emails, the more effective they are at duping unsuspecting recipients. The phishing emails appear to be of the garden-variety we routinely block against. However, there are some interesting trademarks to this attack notated that add a sense of legitimacy to the user by using Microsoft's own products for the attack. Microsoft offers customers the ability to configure a custom domain name for Azure storage accounts. This is an extremely helpful feature for legitimate purposes, however, very useful to malicious actors as well.
Windows.net Hyperlink
The emails below masquerade as Microsoft's OneDrive service. The malicious hyperlinks inside utilize the Microsoft Azure storage hyperlink extension of .web.core.windows.net. Many of the examples our filters have captured so far were using images instead of text in the body. This helps prevent many email filters from recognizing the message as phishing by the text alone.
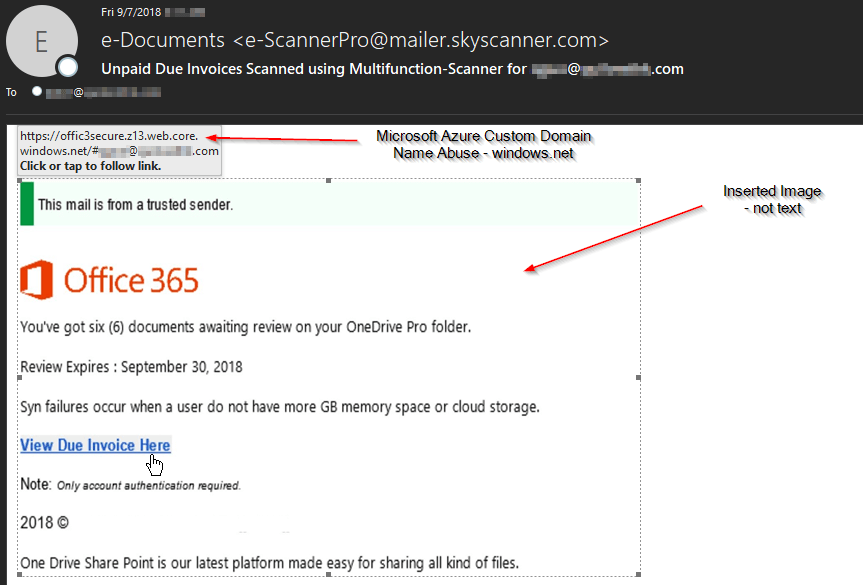
Example 2:
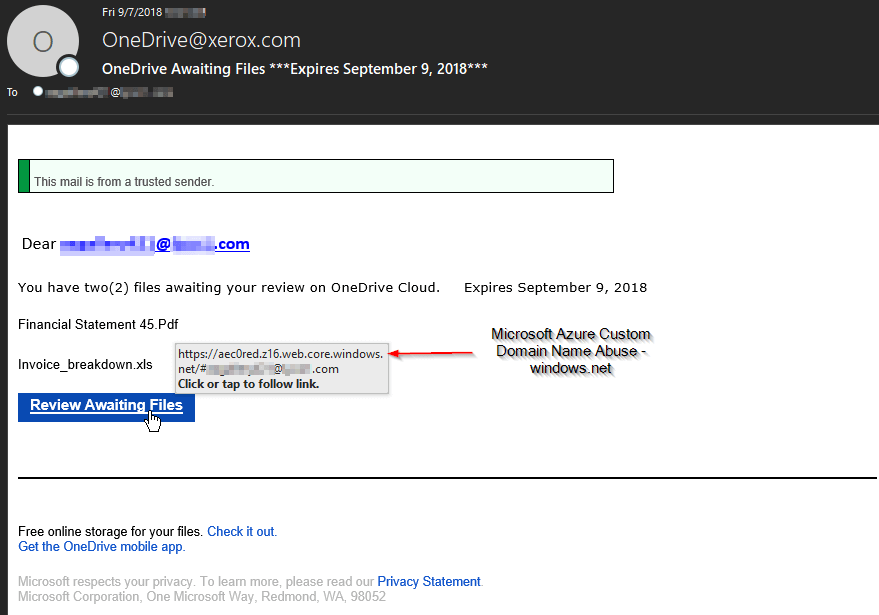
Phishing Sites Harvest Credentials
Users should never click on the links contained in malicious emails. Beside phishing pages, it may direct to a site hosting malware or exploit kits. However, on an isolated test machines using external networks we maintain systems designed just for this type of research. The links, in this case, direct to phishing sites mirrored from legitimate Microsoft login screens. The site url contains the recipient's address to auto-populate into the screen to appear more legitimate.
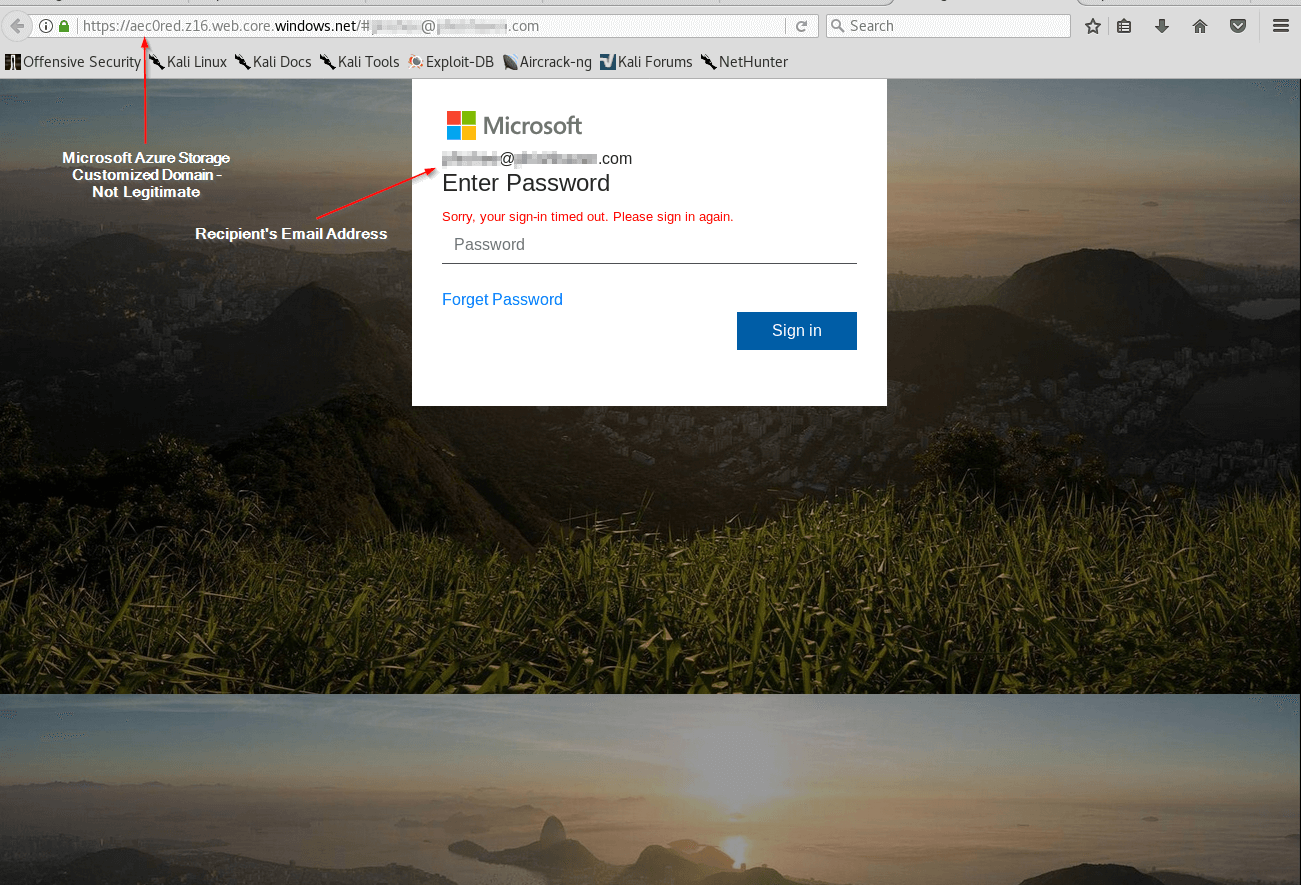
Source Code - URL Encoding Combined with Obfuscation
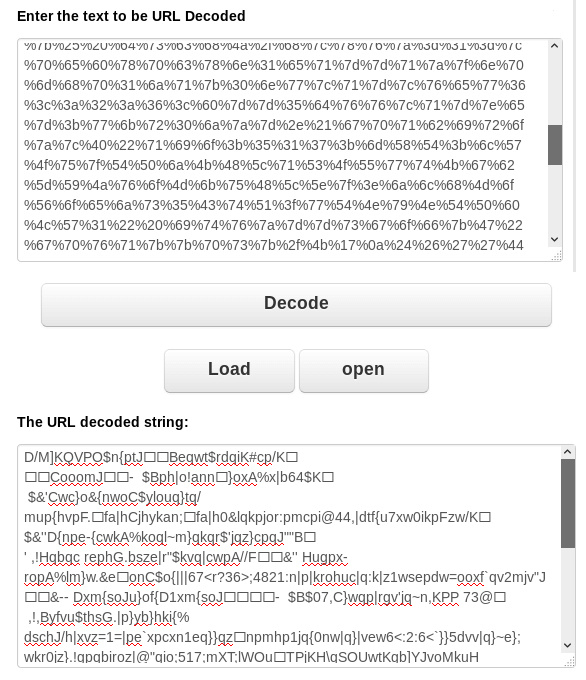
The malicious actor has URL encoded the phishing site's source code, as seen below. Upon decoding the beginning portion we can also see they are obfuscated the remaining scripting. Multiple methods attempting to hide the true site code like this are used to foil website scanners attempting locate malicious sites. This allows the site to remain up longer before it is removed by the hosting provider.
Raw Source
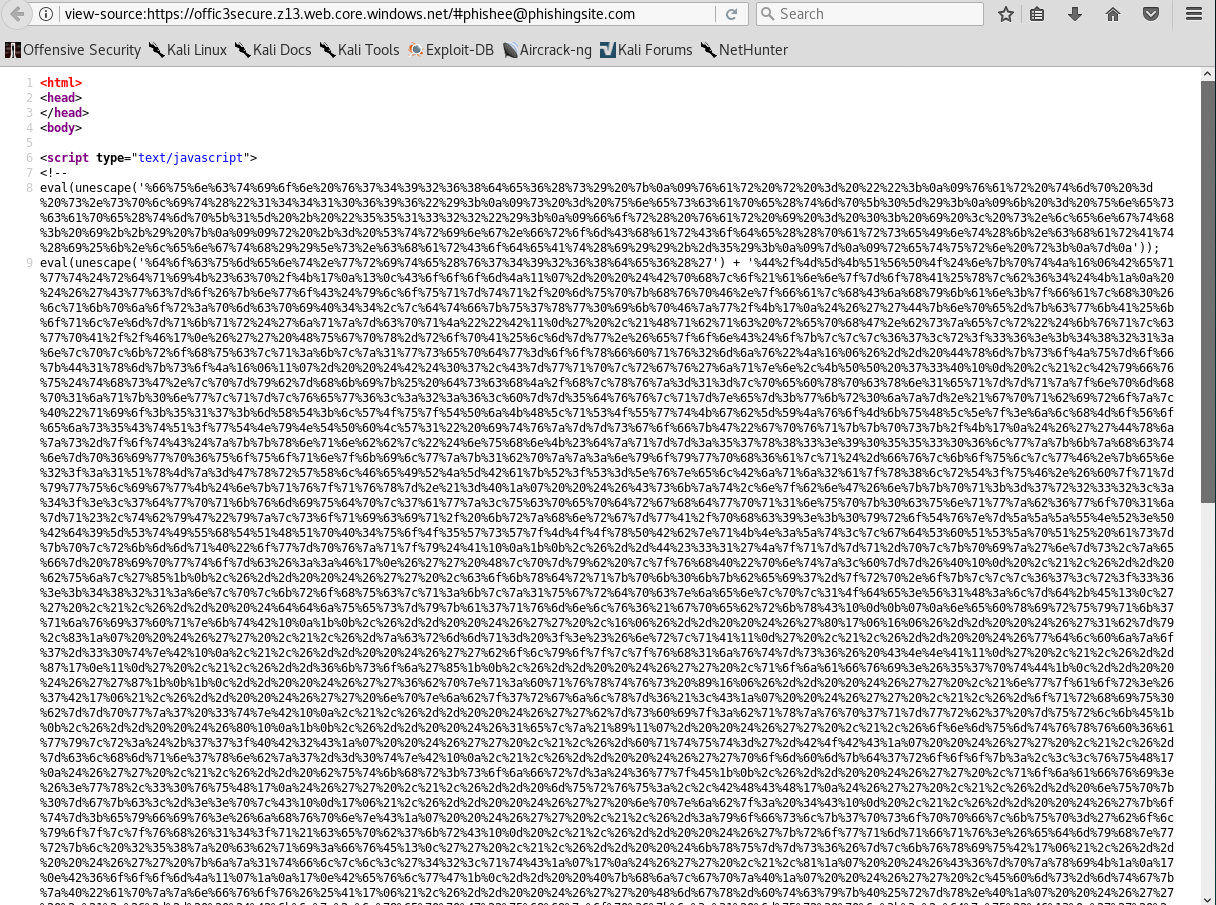
Function used to obfuscate the remaining scripting
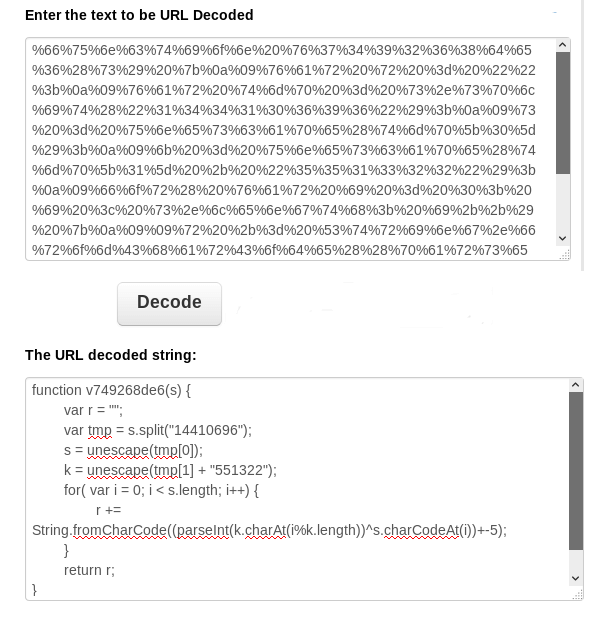
Still Obfuscated after URL Decoding
AppRiver Protection
There is no shortage of spam, malware, phishing, or nefarious websites AppRiver’s staff and systems continuously protect and defend against. Malicious actors work around the clock, therefore, we at AppRiver work even harder to stay one step ahead. Our team is here 24/7 365 days a year protecting and supporting clients and partners from security threats.
